Use VLAN to separate WiFi from everything else
This is a problem which has soaked up many hours over the past few days. Currently, our school's LAN does not utilise VLANs. Now, I want to create a VLAN just for WiFi use. I've created the following VLAN on the SonicWall NSA 250M router:
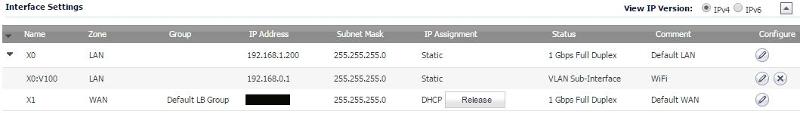
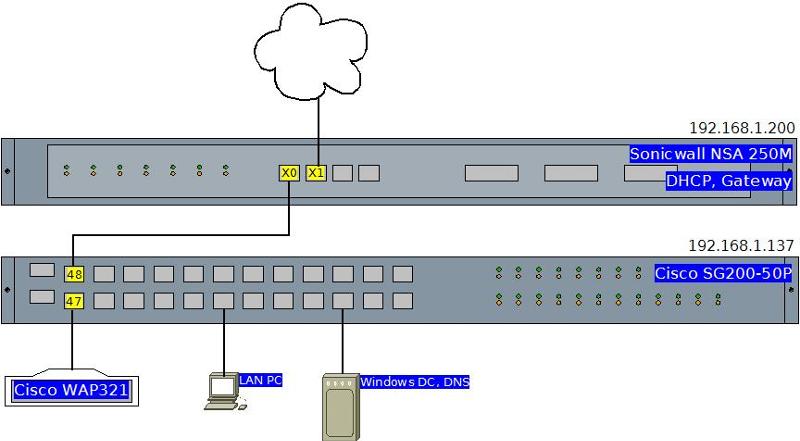
which automatically enabled it's own DHCP scope: 192.168.0.2 - 254 on the X0:V100 interface. On the Cisco SG200 Layer 2 switch to which the WAP is connected, I added the same VLAN. For testing, I have a PC on the future WAP port (no.47). So, apart from that, it now looks like this:
What I want to do:
I want this PC (future WAP) to exist on this new 192.168.0.x subnet and have clients access only the internet, not any servers, etc. on the existing 192.168.1.x LAN.
Problem I'm having:
No matter what settings I use on port 47, either nothing changes regarding subnet and access to resources, or, it's completely isolated from everything including the sonicwall router.
What I've tried:
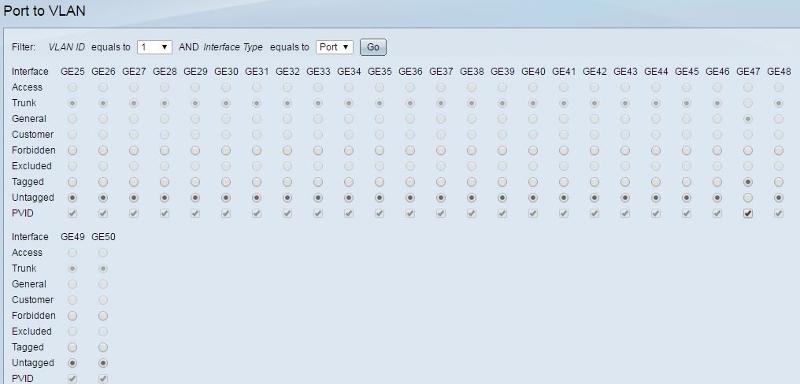
All LAN ports are set to "excluded" for VLAN 100 by default, so I've tried setting port 47 to both tagged and untagged. For VLAN 1 (where all ports are "untagged" by default) I've tried setting port 47 to both forbidden and tagged as below:
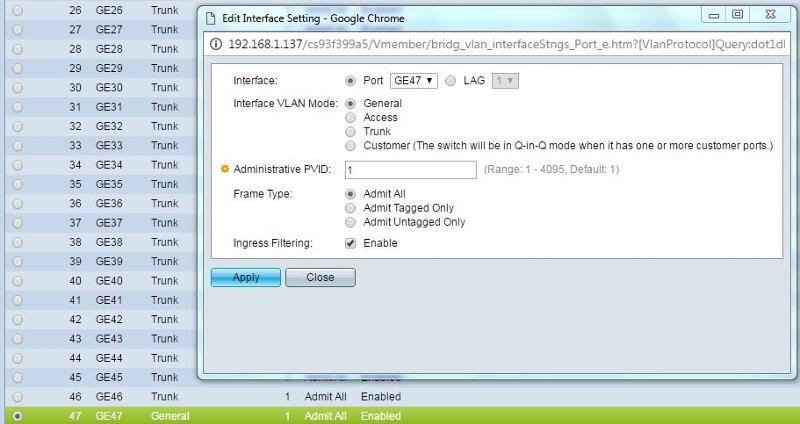
I've also tried setting the "interface settings" for 47 to be trunk (default for everything), General and Access (with the various frame type options).
I've researched this thoroughly, but can't find where I'm going wrong. Questions I have would include:
What interface should each involved port be? general, access, trunk or customer?
If general or trunk, what should the PVID be?
If general, should it be Admit All, Admit Tagged Only or Admit Untagged Only and should Ingress Filtering be enabled?
For each of VLANs 1 and 100, what should the settings be for each of ports 47 and 48?
Is there anything else I need to do on the Sonicwall? Firewall settings perhaps?
Any help would be much appreciated as I have very little hair left to tear out.
which automatically enabled it's own DHCP scope: 192.168.0.2 - 254 on the X0:V100 interface. On the Cisco SG200 Layer 2 switch to which the WAP is connected, I added the same VLAN. For testing, I have a PC on the future WAP port (no.47). So, apart from that, it now looks like this:

What I want to do:
I want this PC (future WAP) to exist on this new 192.168.0.x subnet and have clients access only the internet, not any servers, etc. on the existing 192.168.1.x LAN.
Problem I'm having:
No matter what settings I use on port 47, either nothing changes regarding subnet and access to resources, or, it's completely isolated from everything including the sonicwall router.
What I've tried:
All LAN ports are set to "excluded" for VLAN 100 by default, so I've tried setting port 47 to both tagged and untagged. For VLAN 1 (where all ports are "untagged" by default) I've tried setting port 47 to both forbidden and tagged as below:
I've also tried setting the "interface settings" for 47 to be trunk (default for everything), General and Access (with the various frame type options).
I've researched this thoroughly, but can't find where I'm going wrong. Questions I have would include:
What interface should each involved port be? general, access, trunk or customer?
If general or trunk, what should the PVID be?
If general, should it be Admit All, Admit Tagged Only or Admit Untagged Only and should Ingress Filtering be enabled?
For each of VLANs 1 and 100, what should the settings be for each of ports 47 and 48?
Is there anything else I need to do on the Sonicwall? Firewall settings perhaps?
Any help would be much appreciated as I have very little hair left to tear out.
If you have empty physical port on sonicwall, can you allocate it to DMZ (wifi) and connect it to port 47? Port 47 will be in access mode and assigned to vlan 100. Don't create vlan 100 interface on the switch and use interface on sonicwall as gateway.
ASKER
@SIM50
Not sure I understand what you're saying - do you mean run a patch cable between a spare port on the sonicwall and port 47 on the switch? That's the port I want to plug the WAP into. And wouldn't that make it a port-based VLAN rather than tagged?
Not sure I understand what you're saying - do you mean run a patch cable between a spare port on the sonicwall and port 47 on the switch? That's the port I want to plug the WAP into. And wouldn't that make it a port-based VLAN rather than tagged?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for that, it certainly sounds promising - I'll try that when I'm onsite later. As we roll out further WAPs on different switches on the LAN (same model), can we use that same Sonicwall-switch port 48 connection (ie without adding extra cables to the sonicwall)?
can we use that same Sonicwall-switch port 48 connection (ie without adding extra cables to the sonicwall)?
Yes. You need only one connection to the firewall. If you want to add another WAP, you would have to assign that port to VLAN 100. If WAP would be connected to a different switch, you would need to create VLAN 100 on that switch and connect switches using trunk ports. Also make sure that VLAN 100 is allowed through the trunk.
ASKER
Ok, I cannot get this to work. No matter what I do, sonicwall DHCP will not work for me on a VLAN. If I understand you correctly, you suggested I connect an extra cable between the switch and the sonicwall and then create a new VLAN within sonicwall based on that new interface. You said not to creat vlan 100 on the switch, but as far as I can see, you can't avoid doing that if you want to add switch ports to the vlan... unless I'm taking you up wrong. So I followed your instructions as best I could:
Cabling
======
Sonicwall Router Cisco Switch
X0 --------------> Port 48 (as per above diagram - was always in place)
X2 --------------> Port 47 (extra cable between switch and sonicwall)
Test PC (future WAP) is connected on port 46
Sonicwall Settings
===============
INTERFACES
X0 (cable 1/2) LAN 192.168.1.200 255.255.255.0 STATIC
X2 (cable 2/2) DMZ 192.168.0.1 255.255.255.0 STATIC (also tried DMZ, LAN)
X2:V100 LAN 192.168.2.1 255.255.255.0 STATIC VLAN SUB-INTERFACE (also tried DMZ, LAN)
DHCPv4 SERVER LEASE SCOPES
DYNAMIC RANGE:192.168.1.5 – 192.168.1.99 INTERFACE X0
DYNAMIC RANGE:192.168.2.2 – 192.168.2.254 INTERFACE X2:V100
SWITCH PORT-TO-VLAN, INTERFACE SETTINGS
==========================
PORT: 46 47
VLAN 1: excluded excluded
VLAN100: untagged untagged
Interface setting: Access Access
admin PVID: 100 100
Connected to: PC Sonicwall
It really feels like I'm almost there - if you've anything to add or point out, I'd be grateful!
Cabling
======
Sonicwall Router Cisco Switch
X0 --------------> Port 48 (as per above diagram - was always in place)
X2 --------------> Port 47 (extra cable between switch and sonicwall)
Test PC (future WAP) is connected on port 46
Sonicwall Settings
===============
INTERFACES
X0 (cable 1/2) LAN 192.168.1.200 255.255.255.0 STATIC
X2 (cable 2/2) DMZ 192.168.0.1 255.255.255.0 STATIC (also tried DMZ, LAN)
X2:V100 LAN 192.168.2.1 255.255.255.0 STATIC VLAN SUB-INTERFACE (also tried DMZ, LAN)
DHCPv4 SERVER LEASE SCOPES
DYNAMIC RANGE:192.168.1.5 – 192.168.1.99 INTERFACE X0
DYNAMIC RANGE:192.168.2.2 – 192.168.2.254 INTERFACE X2:V100
SWITCH PORT-TO-VLAN, INTERFACE SETTINGS
==========================
PORT: 46 47
VLAN 1: excluded excluded
VLAN100: untagged untagged
Interface setting: Access Access
admin PVID: 100 100
Connected to: PC Sonicwall
It really feels like I'm almost there - if you've anything to add or point out, I'd be grateful!
Don't create vlan 100 interface on the switch and use interface on sonicwall as gateway.
You need to create VLAN on the switch. You don't need to create VLAN interface. Use the interface on your firewall as the gateway for that network.
ASKER
Thanks for the super-fast reply and for solving the problem! It actually made no difference at first, the eureka moment came when I rebooted switch and router in desperation.
ASKER
Remember - even with reasonably decent networking gear, if at first you don't succeed, try a reboot.