Correct port settings for separate WiFi VLAN
Our school’s network has always had just one subnet for everything. Now, we want to isolate WiFi. Thanks to help from user SIM50 on a previous Xperts-exchange question, I’ve done this with one WAP, connected to a switch which is in turn connected to our Sonicwall router as follows:
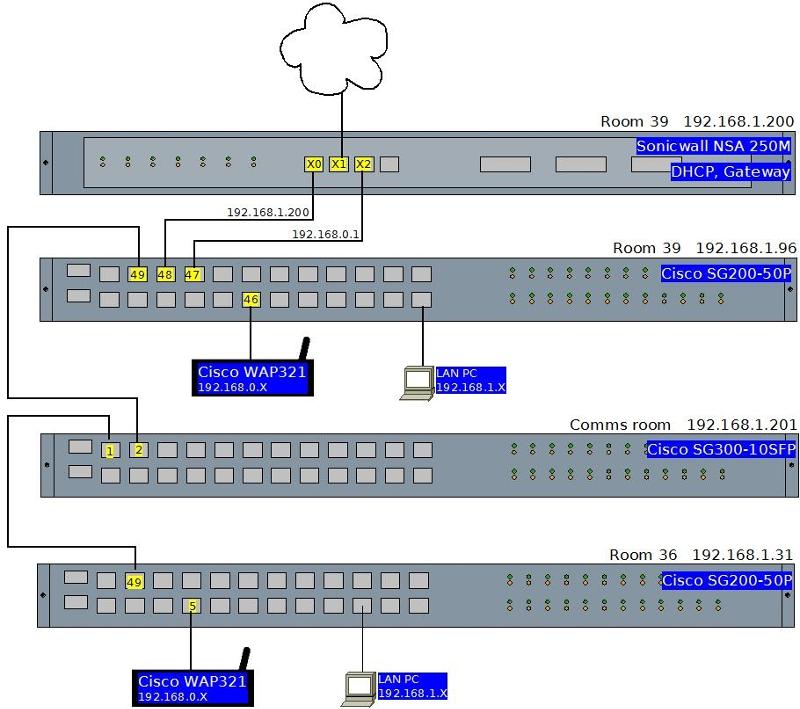
VLAN1:192.168.1.1 (LAN)
VLAN100:192.168.0.1 (WiFi)
In the above, the first WAP is working, but I haven’t extended VLAN100 beyond that switch. I now need to replicate these settings to the above “Room 36” switch, but I believe there are VLAN settings I need to assign to the pre-existing trunks (fibre) between those two rooms (and the comms room switch in the middle so, Room 39 switch -> Comms room (fibre) -> Room 36 switch).
Working on what I learned from the previous question, I guessed I needed to create the same VLAN on the other two switches, make the trunk ports “tagged” for that VLAN and then replicate the port settings for the working WAP to the port for the second WAP. SIM50 also said I needed to make sure VLAN100 was allowed through the trunk, but aside from adding the ports to the VLAN, I wasn’t sure what he meant. So I gave it a shot yesterday and I’m not sure how (possible mistake), but I managed to remove all administrative access to all three switches! (the SG200s don’t have admin ports). After reconfiguration, I’m back where I started (first WAP still working).
This is what I think should work:
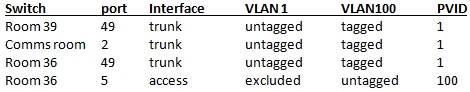
So, I’m looking for some pointers as to where to go from here.

VLAN1:192.168.1.1 (LAN)
VLAN100:192.168.0.1 (WiFi)
In the above, the first WAP is working, but I haven’t extended VLAN100 beyond that switch. I now need to replicate these settings to the above “Room 36” switch, but I believe there are VLAN settings I need to assign to the pre-existing trunks (fibre) between those two rooms (and the comms room switch in the middle so, Room 39 switch -> Comms room (fibre) -> Room 36 switch).
Working on what I learned from the previous question, I guessed I needed to create the same VLAN on the other two switches, make the trunk ports “tagged” for that VLAN and then replicate the port settings for the working WAP to the port for the second WAP. SIM50 also said I needed to make sure VLAN100 was allowed through the trunk, but aside from adding the ports to the VLAN, I wasn’t sure what he meant. So I gave it a shot yesterday and I’m not sure how (possible mistake), but I managed to remove all administrative access to all three switches! (the SG200s don’t have admin ports). After reconfiguration, I’m back where I started (first WAP still working).
This is what I think should work:

So, I’m looking for some pointers as to where to go from here.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER