Windows 10 updates turns off public folders
We have a small application that is located in Public Folders. The majority of our clients are 2-5 users small peer to peer networks. As such we turn on Public Folder Sharing and turn off Password required under "Change Advanced Network Settings".
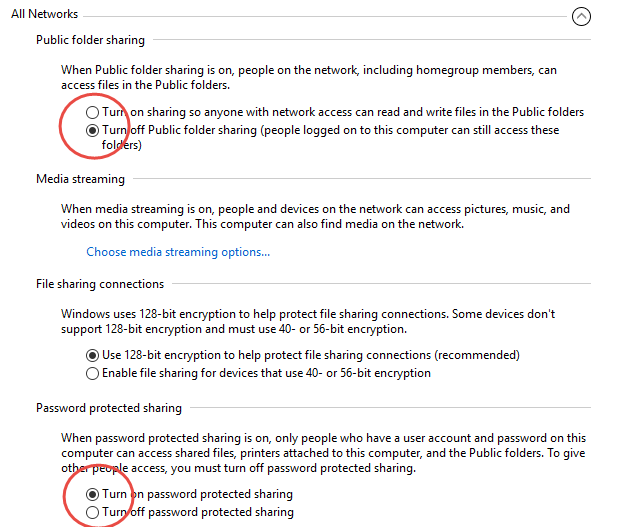 This has worked now since Windows 7
This has worked now since Windows 7
In the last 4 weeks though I repeatedly get calls from clients whom cannot access the application.
The reason is that after a Windows update these settings change, not all clients but a large enough proportion of them.
Ideally it would be great for the developer to relocate the application into its own folder in the root directory to share
But until that happens why is this so?
Searching the net to date I have found no references from Microsoft as to why this would happen.
Any ideas? Can it be prevented?
 This has worked now since Windows 7
This has worked now since Windows 7In the last 4 weeks though I repeatedly get calls from clients whom cannot access the application.
The reason is that after a Windows update these settings change, not all clients but a large enough proportion of them.
Ideally it would be great for the developer to relocate the application into its own folder in the root directory to share
But until that happens why is this so?
Searching the net to date I have found no references from Microsoft as to why this would happen.
Any ideas? Can it be prevented?
It was done to further secure Windows. That is the why. Now you need to overtly re-enable if you want them.
ASKER
John, any references to your comments?
This means that I must re-enable after every update, surely this cannot be the case.
I need ammunition to get the developer to relocate the application.
This week I have re-enabled 25 clients to date not something that I wish to do weekly.
Thanks for feedback
Philip
This means that I must re-enable after every update, surely this cannot be the case.
I need ammunition to get the developer to relocate the application.
This week I have re-enabled 25 clients to date not something that I wish to do weekly.
Thanks for feedback
Philip
I think once you re-enable, the settings should stay that way. My folder settings are already secure and not changing at this point.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks to all your feedback it is appreciated however there is nothing in the above that confirms Microsoft turns it off in their updates other than anecdotal evidence. And yes I have considered a Powershell script to revert. As my clients are predominantly desktops in a peer to peer environments, allowing them access to Public Folders should be acceptable. As mentioned long term Solution is for developer to modify application folder but in the absence of any evidence its a long straw to request.
Thanks
Thanks
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I see on a couple of Windows 10 machines that updates have turned Homegroup ON. I keep it OFF, so I have to change this after each very significant update.
Phillip: I just had a system with the settings intact AND due for an update that was expected to change the settings. It happened last night. For me this isn't anecdotal. The behavior has been observed over many systems. I have a host of systems that were working until recently and now aren't working. Many of them haven't been "fixed" yet - so remain in the state left by the update. I don't think that's anecdotal either. It happened. The results are observable.
The issue that you bring up about password protected sharing is one that we have observed. I don't understand how you would say this is anecdotal when you have said:
Just to be clear: I have control of perhaps 100 computers over a number of companies. By "control" I mean that I'm the only person who is able or likely to make changes of the types we're talking about. The users just want to go on with their work. I'm sure your experience is very similar. So, when I see these changes occur then there is but one place to go to investigate. I've been investigating and the source of the issue seems clear. These problems have been evident in all of the companies who have settings of importance that have been changed.
Microsoft has so far run a test regarding changes to firewall rule scope. They claim that *added* firewall rules with expanded scope are not changed by the updates. All of my firewall rules were not *added* but were existing/standard that I had *changed*. The changes went away. Presumably they are confirming this now...
John Hurst seems to confirm that this update behavior is intentional but hasn't given us a reference to that information yet. It might be reasonable for him to provide us with reference links to his assertions. I have no idea what Microsoft has said about changing settings and have found none so far. Even they don't seem to know about it in recent discussions I've had with them. Woody Leonhard says they "will fix it next year". "Improving security" is not something that one would expect would mean "we're gonna change your settings for you". Yet, that seems to be what's happening.
I am somewhat amazed that if you Google [windows 10 updates are changing settings] there is nothing found but the old tales about the Windows update process and how to manage/control that. Yet we see this happening and have to overcome the results.
I don't use Homegroups but do allow Windows to manage homegroup connections - as we do have systems with file sharing not using passwords. So I can't confirm John Hurst's observation about that setting.
The issue that you bring up about password protected sharing is one that we have observed. I don't understand how you would say this is anecdotal when you have said:
The reason is that after a Windows update these settings changeAnother issue is that firewall rules with expanded scope have had the scope expansions removed (i.e. added subnets).
Just to be clear: I have control of perhaps 100 computers over a number of companies. By "control" I mean that I'm the only person who is able or likely to make changes of the types we're talking about. The users just want to go on with their work. I'm sure your experience is very similar. So, when I see these changes occur then there is but one place to go to investigate. I've been investigating and the source of the issue seems clear. These problems have been evident in all of the companies who have settings of importance that have been changed.
Microsoft has so far run a test regarding changes to firewall rule scope. They claim that *added* firewall rules with expanded scope are not changed by the updates. All of my firewall rules were not *added* but were existing/standard that I had *changed*. The changes went away. Presumably they are confirming this now...
John Hurst seems to confirm that this update behavior is intentional but hasn't given us a reference to that information yet. It might be reasonable for him to provide us with reference links to his assertions. I have no idea what Microsoft has said about changing settings and have found none so far. Even they don't seem to know about it in recent discussions I've had with them. Woody Leonhard says they "will fix it next year". "Improving security" is not something that one would expect would mean "we're gonna change your settings for you". Yet, that seems to be what's happening.
I am somewhat amazed that if you Google [windows 10 updates are changing settings] there is nothing found but the old tales about the Windows update process and how to manage/control that. Yet we see this happening and have to overcome the results.
I don't use Homegroups but do allow Windows to manage homegroup connections - as we do have systems with file sharing not using passwords. So I can't confirm John Hurst's observation about that setting.
ASKER
Fred, thanks for your detailed response. I stand corrected on the anecdotal but ...... The changes are not necessarily consistent as I don't see across all PC's. Like you also I'm amazed the searching either Google or Bing shows no reference to this.
But yes it does happen. My concern is the time it takes me each week to revert back to pre update settings. Whilst this in itself is a quick process its the quantity and the necessity of it.
So to John and Fred thanks. I have this also posted in the MS Community so we'll see what that turns up but I wont hold my breathe. I guess all I'm really looking for is that MS confirms this process and that it is intentional as opposed to maybe this just effects a certain criteria.
FYI last two weeks I have had close to 25 systems a week to turn public folders back on and turn off password protected sharing, in total I support well in excess of 600-700 desktops. In so far as I am concerned it is only significant on the "peer server" where our application is shared via public folders. The reason being that workstations need to access the executable to launch our application. Even then that would amount to 200 plus systems. If it was across all Windows 7 & 10 PC's I would have far more calls.
Maybe there still to come.
Again thanks and will close this post by the end of the weekend.
But yes it does happen. My concern is the time it takes me each week to revert back to pre update settings. Whilst this in itself is a quick process its the quantity and the necessity of it.
So to John and Fred thanks. I have this also posted in the MS Community so we'll see what that turns up but I wont hold my breathe. I guess all I'm really looking for is that MS confirms this process and that it is intentional as opposed to maybe this just effects a certain criteria.
FYI last two weeks I have had close to 25 systems a week to turn public folders back on and turn off password protected sharing, in total I support well in excess of 600-700 desktops. In so far as I am concerned it is only significant on the "peer server" where our application is shared via public folders. The reason being that workstations need to access the executable to launch our application. Even then that would amount to 200 plus systems. If it was across all Windows 7 & 10 PC's I would have far more calls.
Maybe there still to come.
Again thanks and will close this post by the end of the weekend.