yairge
asked on
Windows 10 Machine not applied beeing applied by the WHOLE GPO , 2012 R2 Domain
Hi,
I have very weird issue.
I have 2012R2 Domain Controller(I have imported Windows 10 ADMX into the 2012DC, via this manual http://www.windowstricks.in/2016/07/group-policy-setting-not-applying-windows-10-computers.html)
along windows 7 machines, i recently started to add windows 10 machines
windows 7 machines receive the GPO fine.
All the windows 10 machines receive only partial of the GPO
For instance: a machine and a user on Windows 7 computer will get more GPO then identical Windows 10 Machine
This is how the GPO look on server side:
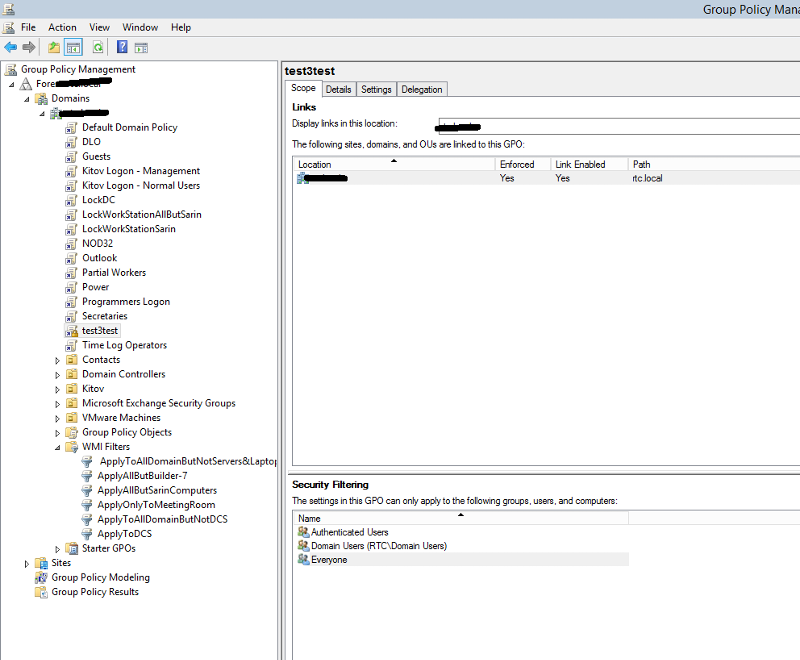
As you can see there are more GPO`s exists at the server then the onces applied at the machine below:
gpresult /r on windows 10 machine:
for instance, test3test GPO should be applied on the machine, It has no WMI filter, Its anabled and its marked as "Everyone"
So why i dont even see test3test GPO even beeing rejected under " The following GPOs were not applied because they were filtered out"
Help anyone?
Anyway to debug this?
It seem like the Client does not event get the GPO at all from the server.
i have also tried to do this:
HKEY_LOCAL_MACHINE\SOFTWAR
“\\*\SYSVOL”
“RequireMutualAuthenticati
HKEY_LOCAL_MACHINE\SOFTWAR
“RequireMutualAuthenticati
I have very weird issue.
I have 2012R2 Domain Controller(I have imported Windows 10 ADMX into the 2012DC, via this manual http://www.windowstricks.in/2016/07/group-policy-setting-not-applying-windows-10-computers.html)
along windows 7 machines, i recently started to add windows 10 machines
windows 7 machines receive the GPO fine.
All the windows 10 machines receive only partial of the GPO
For instance: a machine and a user on Windows 7 computer will get more GPO then identical Windows 10 Machine
This is how the GPO look on server side:

As you can see there are more GPO`s exists at the server then the onces applied at the machine below:
gpresult /r on windows 10 machine:
Domain Type: Windows 2008 or later
Applied Group Policy Objects
-----------------------------
Default Domain Policy
LockWorkStationAllButSarin
DLO
NOD32
The following GPOs were not applied because they were filtered out
-------------------------------------------------------------------
LockDC
Filtering: Denied (WMI Filter)
WMI Filter: ApplyToDCS
Local Group Policy
Filtering: Not Applied (Empty)
The user is a part of the following security groups
---------------------------------------------------
Domain Users
Everyone
BUILTIN\Administrators
BUILTIN\Users
NT AUTHORITY\INTERACTIVE
CONSOLE LOGON
NT AUTHORITY\Authenticated Users
This Organization
LOCAL
Authentication authority asserted identity
High Mandatory Levelfor instance, test3test GPO should be applied on the machine, It has no WMI filter, Its anabled and its marked as "Everyone"
So why i dont even see test3test GPO even beeing rejected under " The following GPOs were not applied because they were filtered out"
Help anyone?
Anyway to debug this?
It seem like the Client does not event get the GPO at all from the server.
i have also tried to do this:
HKEY_LOCAL_MACHINE\SOFTWAR
“\\*\SYSVOL”
“RequireMutualAuthenticati
HKEY_LOCAL_MACHINE\SOFTWAR
“RequireMutualAuthenticati
ASKER
Well,
Ofcourse i did gpupdate before the gpresult.
the output is the same.
how do i start to debug this
Ofcourse i did gpupdate before the gpresult.
the output is the same.
how do i start to debug this
Do a group policy modeling at the DC for that win10 machine. That modeling will tell you if those policies should have gotten applied or not.
ASKER
I have...
the Dc says should be applied
hence its only client side problem? this weird.. many clients have this issue
i havedisabled the FW
the Dc says should be applied
hence its only client side problem? this weird.. many clients have this issue
i havedisabled the FW
How about if you also add
RequireIntegrity=0,Require
to both those registry locations ??
RequireIntegrity=0,Require
to both those registry locations ??
Take a clean test vm with win10, join it to the domain, add it to that OU and test.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
The issue is because
MS16-072 Update
I managed to solve it by doing this
https://blogs.technet.microsoft.com/askds/2016/06/22/deploying-group-policy-security-update-ms16-072-kb3163622/
MS16-072 Update
I managed to solve it by doing this
https://blogs.technet.microsoft.com/askds/2016/06/22/deploying-group-policy-security-update-ms16-072-kb3163622/
Do a gpupdate on an elevated command prompt on win10 and retest.