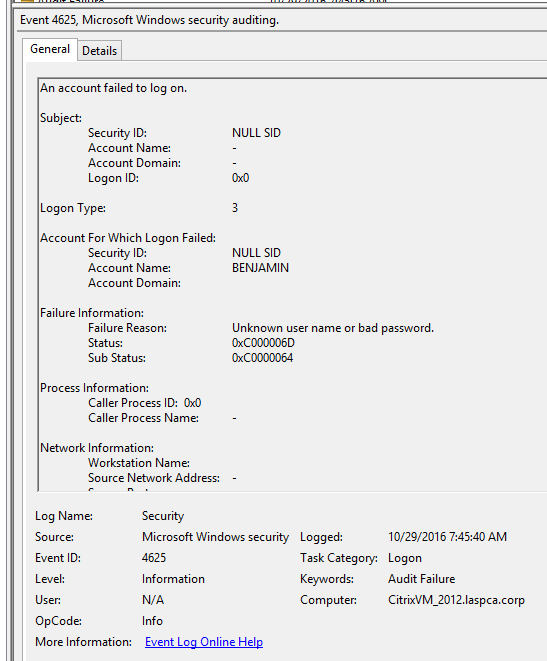
Getting EventID 4625 logon failures
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thanks
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Going back to the image you posted originally, there is no information in the source network address field.
Are you sure that the system is being attacked over the network? It might have been infected and the infection may be using an internal connection to attack.
Are you sure that the system is being attacked over the network? It might have been infected and the infection may be using an internal connection to attack.
ASKER
no I'm not sure. I ran a virus scan this morning and nothing was found
I would also run Malwarebytes as a good and additional starting point...
ASKER
doing that already. Thanks
ASKER
no solution found as of this post. Still getting 4625 audit failures every 20 seconds.
You may need to try this after hours.
Unplug it from the network, let it sit for five minutes, and plug it back in. See if the attacks stopped for that period. If they did, the attack is probably external. If they did not, the attack is definitely internal.
Unplug it from the network, let it sit for five minutes, and plug it back in. See if the attacks stopped for that period. If they did, the attack is probably external. If they did not, the attack is definitely internal.
ASKER
it is a Virtual server. How would I disconnect it? Change the network connection to "not connected"
ASKER
I took it off line. The errors continued except the Account Name was always the name of the server CitrixVM_2012. When is was online the Account Name was things like Mohamed, Robert, Sally, Admin, etc.
So does this tell you it's internal? If so, why does it have other Account Names when connected to the network?
So does this tell you it's internal? If so, why does it have other Account Names when connected to the network?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Dr. Klahn:
I read your last post. We are still deciding what to do. I'll get back to you.
Thanks
I read your last post. We are still deciding what to do. I'll get back to you.
Thanks
ASKER
Thanks for all the help. We've decided to build a new server from scratch.
ASKER
I thought it was important to update this. Prior to building a new server I spent hours just looking for anything logical or not that could cause this.
I noticed that this VM had 2 network cards. Only was was active. I changed the one that was connected to "not connected". Connected the other.
I then checked the Event logs and all the 4625 errors had stopped.
Why would a different IP stop the problem?
I noticed that this VM had 2 network cards. Only was was active. I changed the one that was connected to "not connected". Connected the other.
I then checked the Event logs and all the 4625 errors had stopped.
Why would a different IP stop the problem?
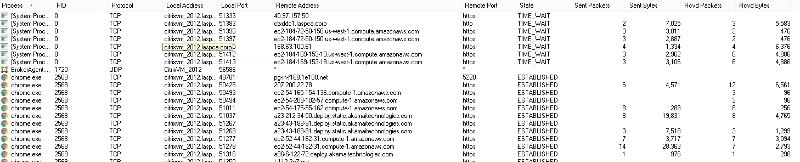
If it is coming from within your LAN, locate the system currently on the attacking IP address, unplug it from the network and restore it from a clean backup.
If it is coming from outside your LAN, block the offending IP block (at least to the /24 level) at the firewall.