IIS8 Internal IP Address Disclosed in HTTP Headers
Hi
Recently a site hosted on an IIS8 server failed a pen test with Internal IP Address Disclosed in HTTP Headers.
I have found loads of ways to sort in iis7 and earlier but not in iis8.
Please help.
thanks
Recently a site hosted on an IIS8 server failed a pen test with Internal IP Address Disclosed in HTTP Headers.
I have found loads of ways to sort in iis7 and earlier but not in iis8.
Please help.
thanks
Fairly common vulnerability. You can go into the features view in IIS and find HTTP Response headers. Double click and then right click and remove https://imgalib.wordpress.com/tag/ssl-certificate-vulnerability/ look about half way down
ASKER
I dont have anything listed in HTTP Response headers.
ASKER
Also it is turned off in my web.config
<httpRuntime targetFramework="4.5" maxRequestLength="1048576"
<httpRuntime targetFramework="4.5" maxRequestLength="1048576"
What Response Header are you concerned about? Name?
There are several Response Headers that leak info in default IIS installation. Some can be addressed in the web applications config and some can be globally addressed in the server scope configuration of IIS.
What does your web infrastructure look like?
1. an IIS Server sitting behind a firewall with setup with a public IP (no NAT)
2. an IIS Server sitting behind a firewall with a private IP (firewall doing NAT)
3. an IIS Server sitting behind a firewall with a load balancer (using a public IP) (no NAT)
4. an IIS Server sitting behind a firewall with a load balancer (using a private IP) (firewall doing NAT)
I ask because in these scenarios, the leak may not necessary be coming from IIS. There may be other device in front of your server that could be adding response headers to the outgoing http replay. You may have to address these other devices as well.
Dan
There are several Response Headers that leak info in default IIS installation. Some can be addressed in the web applications config and some can be globally addressed in the server scope configuration of IIS.
What does your web infrastructure look like?
1. an IIS Server sitting behind a firewall with setup with a public IP (no NAT)
2. an IIS Server sitting behind a firewall with a private IP (firewall doing NAT)
3. an IIS Server sitting behind a firewall with a load balancer (using a public IP) (no NAT)
4. an IIS Server sitting behind a firewall with a load balancer (using a private IP) (firewall doing NAT)
I ask because in these scenarios, the leak may not necessary be coming from IIS. There may be other device in front of your server that could be adding response headers to the outgoing http replay. You may have to address these other devices as well.
Dan
ASKER
HI Dan
The site is behind a firewall and nat'd.
Its leaking the Internal IP Address of the server.
Thanks
Tim
The site is behind a firewall and nat'd.
Its leaking the Internal IP Address of the server.
Thanks
Tim
What is the name of the response header? It would be helpful to know the name of the actual header.
What brand of firewall are you using?
Dan
What brand of firewall are you using?
Dan
ASKER
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks Dan. could it still be the firewall even though its reporting the IIS servers local address?
thanks
thanks
If you directly hit the IIS Server, I believe you will not see the location response header. You can verify this by using a developer tool plugin/extension on your browser. For example, in FireFox, I open the Developer tools and view the conversation between the browser and the server. Here you can see the raw info being passed back and forth. You can also do this in either IE/Edge and Chrome.
When I directly hit the various IIS server I manage, I do not see a location header.
I suggest you test hitting the server directly and check for the presence of the location response header. If it exists on a direct hit (not going thru your firewall NAT) then you can remove it with URL Rewrite.
If the response header is not present, then the firewall is adding the header to the outbound http reply. You will need to modify what the firewall is doing in this situation.
Dan
When I directly hit the various IIS server I manage, I do not see a location header.
I suggest you test hitting the server directly and check for the presence of the location response header. If it exists on a direct hit (not going thru your firewall NAT) then you can remove it with URL Rewrite.
If the response header is not present, then the firewall is adding the header to the outbound http reply. You will need to modify what the firewall is doing in this situation.
Dan
ASKER
Ok thanks Dan thats great, i will investigate further and report back.
ASKER
Do you see an issue it turning off HTTP 1.0?
Can you explain a little more about where you intend to "turn off HTTP 1.0?"
Dan
Dan
ASKER
Putting the following into web.config
<rewrite>
<rules>
<rule name="RequestBlockingRule1
<match url="*" />
<conditions>
<add input="{SERVER_PROTOCOL}" pattern="HTTP/1.0" />
</conditions>
<action type="AbortRequest" />
</rule>
</rules>
</rewrite>
<rewrite>
<rules>
<rule name="RequestBlockingRule1
<match url="*" />
<conditions>
<add input="{SERVER_PROTOCOL}" pattern="HTTP/1.0" />
</conditions>
<action type="AbortRequest" />
</rule>
</rules>
</rewrite>
You can certainly do that, but I can not think of any reason to block HTTP/1.0. It isn't really a security issue, so would you want to implement a block.
I run many IIS Server instances across 4 environments (DEV, QA, Staging, PROD) and do not block HTTP/1.0 requests anywhere.
Dan
I run many IIS Server instances across 4 environments (DEV, QA, Staging, PROD) and do not block HTTP/1.0 requests anywhere.
Dan
ASKER
Im just assuming that blocking http 1.0 would stop the reporting of the internal ip?
Not really. Have you tested hitting the site internally and then externally to compare the response headers?
I believe the header is being added by the device doing the NAT.
Dan
I believe the header is being added by the device doing the NAT.
Dan
ASKER
I have tested internally and externally and i cannot see where its referencing the internal ip.
I might need to get some more information if possible from the pen test company.
I might need to get some more information if possible from the pen test company.
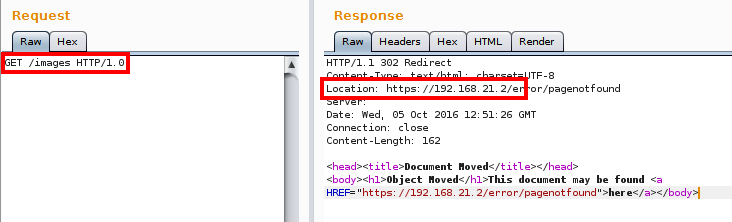
The location is response header inserted into the http reply to the browser. You need to view the raw http data to see it. as I mentioned before, browser Dev tools will let you view this info.
Also, a device doing reverse proxying r NAT can be inserting the header because its acting as an intermediary for the destination resource.
Reference link for the "Location" response header: https://en.wikipedia.org/wiki/HTTP_location
Dan
Also, a device doing reverse proxying r NAT can be inserting the header because its acting as an intermediary for the destination resource.
Reference link for the "Location" response header: https://en.wikipedia.org/wiki/HTTP_location
Dan
Have you been able to resolve the issue? Is that any additional info?
Dan
Dan
ASKER
Looks like it was the WatchGuard so details removed in HTTP proxy.
thanks Dan.
thanks Dan.