Buffalo Terastation - Drive and Raid configuration
We had a drive go down in our Buffalo Terastation the other day and ordered the "same" drive from amazon. When we installed the drive it's appearing a bit too small to allow us to do a raid recovery.
Can someone suggest what we should do to ensure we get the exact same drive as the ones we have? Even though we ordered a drive that was ST4000DM000 we couldn't specify the 1F21 portion of it...and the new drive is a little too small.
Here's a screen shot of the other drives plus the new drive.
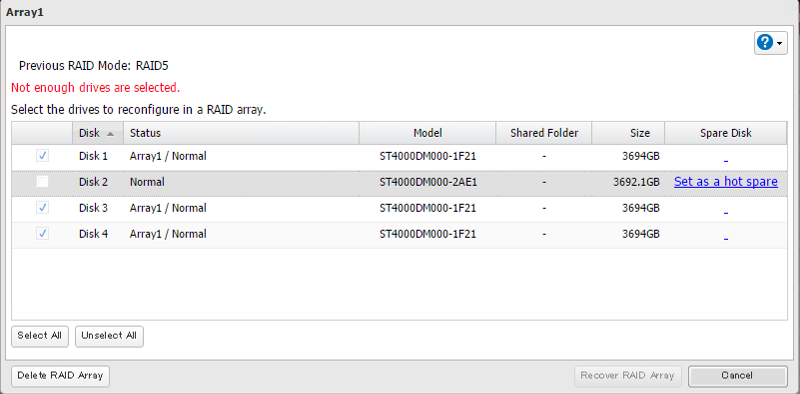
Can someone suggest what we should do to ensure we get the exact same drive as the ones we have? Even though we ordered a drive that was ST4000DM000 we couldn't specify the 1F21 portion of it...and the new drive is a little too small.
Here's a screen shot of the other drives plus the new drive.

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
If I added a larger drive this time, would I also need to match that size in the future?
http://en.faq.buffalo-global.com/app/answers/detail/a_id/14105/p/0,31,32,7000,7002 says it will use the larger disk but ignore the extra space, that's pretty standard with any RAID system. If that disk fails then one of the original size should work as a replacement since it's only used 4GB of the 6GB disk.
Buffalo seem to use "higher capacity" as the key phrase in their documentation so search on you specific model plus "higher capacity" should give confirmation from their FAQs.
Buffalo seem to use "higher capacity" as the key phrase in their documentation so search on you specific model plus "higher capacity" should give confirmation from their FAQs.
ASKER
Thanks for your assistance with this.
ASKER