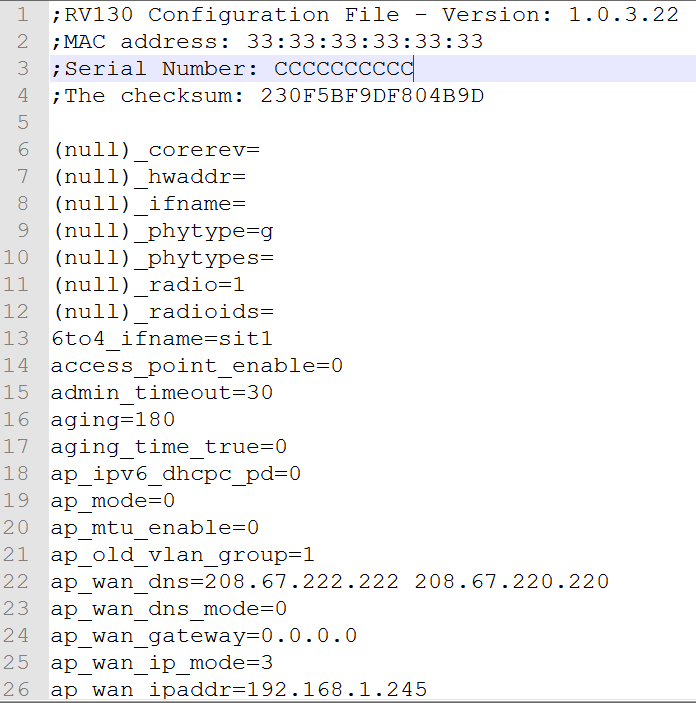
What type of checksum is used for Cisco/Linksys RV router configurations?
I'm trying to find how the checksum is calculated for a RV130 config file. I assume it's the same as for the RV180 series.
It's 16 hex digits. Does not look like MD5 or SHA1.
I want to be able to modify the config and recalculate the checksum so it can be imported in a different router.
Thank you.
;The checksum: 6DDA3C3F5C8C9402
;The checksum: 48E26F2F11BB4DB3It's 16 hex digits. Does not look like MD5 or SHA1.
I want to be able to modify the config and recalculate the checksum so it can be imported in a different router.
Thank you.
where did you see the checksum? can you please upload a screenshot here?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
OK, great.
The problem is that a MD5 hash is 128 bit long (32 hex digits) and the hash in the file is only 64 bit long.
Already tried to compute the MD5 hash of the file and take only half of the digits, but no dice.
The RV130 is Cisco only in name. The RV line used to be called Linksys.
It's basically a stripped BSD box with no CLI and an old version of OpenSwan on it.
The problem is that a MD5 hash is 128 bit long (32 hex digits) and the hash in the file is only 64 bit long.
Already tried to compute the MD5 hash of the file and take only half of the digits, but no dice.
The RV130 is Cisco only in name. The RV line used to be called Linksys.
It's basically a stripped BSD box with no CLI and an old version of OpenSwan on it.
must be crc64.
As per the admin guide
MD5 is 16 bytes (128 bits) as per the stated . Same for RV180 http://abson.com.ua/upload/Cisco/rv180x_administration_guide.pdf
Firmware MD5 Checksum—The message-digest algorithm used to verify the integrity of files.http://www.cisco.com/c/dam/en/us/td/docs/routers/csbr/rv130w/admin_guide/en/rv130w_admin_en.pdf
MD5 is 16 bytes (128 bits) as per the stated . Same for RV180 http://abson.com.ua/upload/Cisco/rv180x_administration_guide.pdf
But this config checksum is 8 bytes, not MD5.
Thanks. Since it differs on the understanding from the config, what is the original factory reset ("Administration > Restore Factory Defaults") checksum config and if is also not MD5 hash as stated here?
Also what is the Checksum shown in the RV actual "Status > System Summary" to view its details of the device properties?
What is the error message for verifying MD5 checksum e.g.
Also what is the Checksum shown in the RV actual "Status > System Summary" to view its details of the device properties?
What is the error message for verifying MD5 checksum e.g.
http://www.cisco.com/c/en/us/about/security-center/ios-image-verification.html#12
Using the Image Verification Cisco IOS verify Command
Network administrators can also use the verify privileged EXEC command, originally introduced for the "MD5 File Validation" feature and updated by the "Image Verification" feature, to verify the integrity of image files that are stored locally on a device. The following example demonstrates how to use the updated verify command on a Cisco IOS device:
router#verify disk0:c7301-jk9s-mz.124-10.bin
Verifying file integrity of disk0:c7301-jk9s-mz.124-10.bin
.....<output truncated>.....Done!
Embedded Hash MD5 : 0C5BE63C4E339707EFB7881FDE7D5324
Computed Hash MD5 : 0C5BE63C4E339707EFB7881FDE7D5324
CCO Hash MD5 : AD9F9C902FA34B90DE8365C3A5039A5B
Signature Verified
router#
ASKER
I could not find any documentation on how to enable CLI on the RV130. That would of solved my problem...
The checksum for the software is MD5:
Firmware Version: 1.0.3.22
CPU Model: Cavium CNS3410
Firmware MD5 checksum: 722118dacc236e0508f22450f3
A sample config backup is attached, with the public IPs edited. The checksums for the default config on 2 different RV130 routers are different, probably because the MAC are different.
RV130_startup.txt
The checksum for the software is MD5:
Firmware Version: 1.0.3.22
CPU Model: Cavium CNS3410
Firmware MD5 checksum: 722118dacc236e0508f22450f3
A sample config backup is attached, with the public IPs edited. The checksums for the default config on 2 different RV130 routers are different, probably because the MAC are different.
RV130_startup.txt
Setting checksum to 0 may disable checksum checking...
ASKER
Tried that. Set it to 0, nothing, "", deleted the line.
The result is always error on importing.
The result is always error on importing.
When you download IOS from Cisco they provide the MD5 hash so you can verify the image doesn't get corrupt during the download.
Once you transfer the image to flash, you should verify it again on the router.
Otherwise may be good to go through the upgrade process again..
https://supportforums.cisco.com/document/12318721/firmwarelanguage-upgrade-rv130-and-rv130w-using-web-interface
Note that the verify command is to be run at privileged EXEC mode. E.g. Router> enable.
The file verify auto command enables image verification globally; that is, all images that are to be copied (via the copy command) or reloaded (via the reload command) are automatically verified. If you have enabled image verification by default but prefer to disable verification for a specific image copy or reload, the /noverify keyword, along with either the copy or the reload command, will override the file verify auto command.
Once you transfer the image to flash, you should verify it again on the router.
Otherwise may be good to go through the upgrade process again..
https://supportforums.cisco.com/document/12318721/firmwarelanguage-upgrade-rv130-and-rv130w-using-web-interface
Note that the verify command is to be run at privileged EXEC mode. E.g. Router> enable.
The file verify auto command enables image verification globally; that is, all images that are to be copied (via the copy command) or reloaded (via the reload command) are automatically verified. If you have enabled image verification by default but prefer to disable verification for a specific image copy or reload, the /noverify keyword, along with either the copy or the reload command, will override the file verify auto command.
ASKER
@btan: that's absolutely correct, for routers that run IOS.
The RV130 is running some form of BSD, judging by the variable names. No CLI, no exec mode, no verify command.
Just a web interface and the option of saving and restoring the config, like any $100 router.
The RV130 is running some form of BSD, judging by the variable names. No CLI, no exec mode, no verify command.
Just a web interface and the option of saving and restoring the config, like any $100 router.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Yes, that totally works for RV120, RV180, etc. Any router that has configs with lines starting with
systemConfig[1]
On RV130 (the replacement of RV120) Cisco changed the type of config. Now the lines are no longer associative arrays, just simple
variable=value
It may well be that I need to put a value that will force the router to ignore the checksum. But 0 does not work, "" does not work, empty space does not work.
systemConfig[1]
On RV130 (the replacement of RV120) Cisco changed the type of config. Now the lines are no longer associative arrays, just simple
variable=value
It may well be that I need to put a value that will force the router to ignore the checksum. But 0 does not work, "" does not work, empty space does not work.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
The reasons why I needed that:
1. create the config offsite, then send it to the local site to be imported. For 15 sites, that's quite some time gained.
2. see if I can convince the router to accept "any" on the right side of the OpenSwan config. Right now you cannot use a domain as the right side of the VPN (test.example.com), since the router expects the other side of the tunnel to send test.example.com as identification, instead of the IP.
Sadly, no can do.
I'll split the points for effort.
1. create the config offsite, then send it to the local site to be imported. For 15 sites, that's quite some time gained.
2. see if I can convince the router to accept "any" on the right side of the OpenSwan config. Right now you cannot use a domain as the right side of the VPN (test.example.com), since the router expects the other side of the tunnel to send test.example.com as identification, instead of the IP.
Sadly, no can do.
I'll split the points for effort.
ASKER
Thanks for trying.