Cisco ASA blocks some https sites.
ASKER
Do a
tracert 185.79.62.3
on both sides and compare - if you only see stars behind the ASA, you might have to allow the icmp time-exceeded and icmp unreachable on the ASA:
ciscoasa#config t
ciscoasa(config)#access-li
ciscoasa(config)#access-li
ciscoasa(config)#access-li
ciscoasa(config)#policy-ma
ciscoasa(config-pmap)#clas
ciscoasa(config-pmap-c)#
inspect icmp
ciscoasa(config-pmap-c)#
inspect icmp error
ciscoasa(config-pmap-c)#en
ciscoasa(config)#service-p
ciscoasa(config)#access-gr
tracert 185.79.62.3
on both sides and compare - if you only see stars behind the ASA, you might have to allow the icmp time-exceeded and icmp unreachable on the ASA:
ciscoasa#config t
ciscoasa(config)#access-li
ciscoasa(config)#access-li
ciscoasa(config)#access-li
ciscoasa(config)#policy-ma
ciscoasa(config-pmap)#clas
ciscoasa(config-pmap-c)#
inspect icmp
ciscoasa(config-pmap-c)#
inspect icmp error
ciscoasa(config-pmap-c)#en
ciscoasa(config)#service-p
ciscoasa(config)#access-gr
ASKER
The following command raises a warning:
ciscoasa(config)# service-policy global_policy global
WARNING: Policy map global_policy is already configured as a service policy
The ASA must be reloaded or it is not required?
ciscoasa(config)# service-policy global_policy global
WARNING: Policy map global_policy is already configured as a service policy
The ASA must be reloaded or it is not required?
It's just because that is a default configuration line on the ASA - the warning means that the policy map, global_policy is already enabled
how did the traceroutes do?
how did the traceroutes do?
not required with reload
ASKER
I see stars behind tha ASA so I condigured the commands but there is no success.
ASKER
May it be certificate issue?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
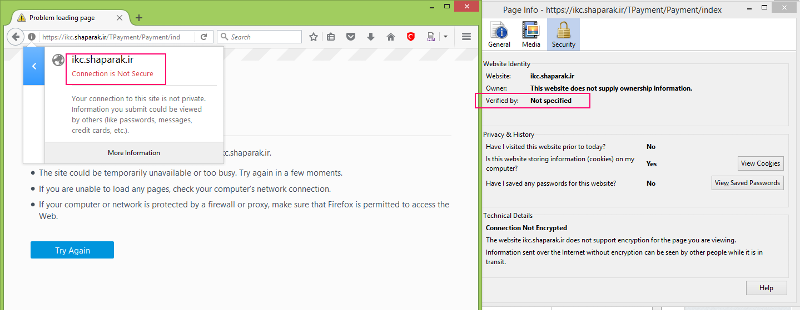
no certificate issue yet, as hosts behind ASA cannot reach the web server at all
Also, the commands I sent about allowing the icmp packages... you used the access list you already had enabled on the outside interface, and not the outside-in as I wrote above, yes?
ASKER
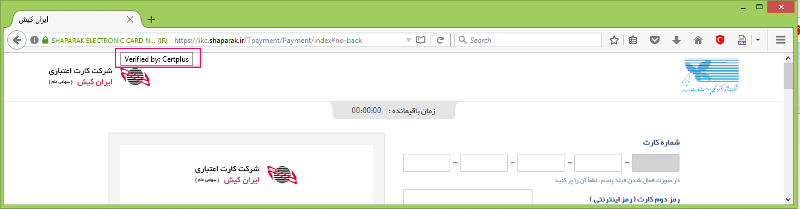
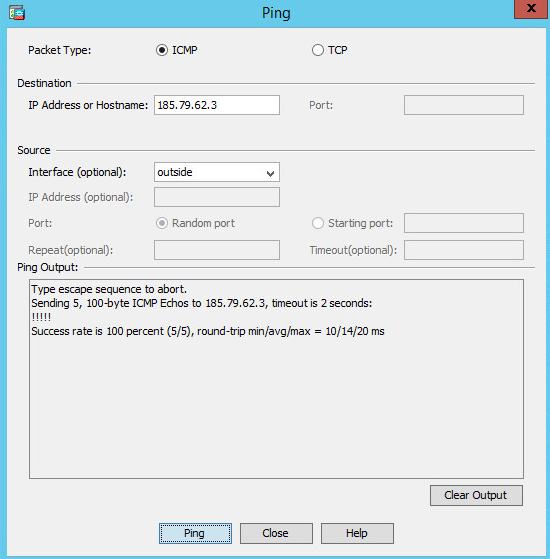
I cannot see the picture.. It is successful?
alright, we have to correct the access-list
in the CLI, do:
show access-list
you should be able to determine which one was used before on the outside interface
then replace the access list with
access-group name-of-access-list in interface outside
alright, we have to correct the access-list
in the CLI, do:
show access-list
you should be able to determine which one was used before on the outside interface
then replace the access list with
access-group name-of-access-list in interface outside
ASKER
I correct outside-in to outside_access_in (real acl) but accessing sites is blocking too.
Great that you corrected
I need to know whether the ping and traceroutes commands were successful or not, while performed from the ASA
I need to know whether the ping and traceroutes commands were successful or not, while performed from the ASA
ASKER
They both are successful from the ASA but til now I cannot be succeed behind that.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I wonder why the lock icon changes to have a red line on it while it trys to connect the ikc.shaparak.ir! because of that I guess may be it is a certificate issue.
ASKER
Other sites, as I know, such as mail.google.com have not such problem.
tuasa# sh run pol
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 4096
policy-map global_policy
class inspection_default
inspect dns
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect ip-options
inspect ipsec-pass-thru
inspect netbios
inspect pptp
inspect rsh
inspect rtsp
inspect sip
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
inspect icmp
inspect icmp error
class http-map1
set connection advanced-options mss-map
policy-map http-map1
class http-map1
set connection advanced-options mss-map
!
and
tuasa# sh run pol
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 4096
policy-map global_policy
class inspection_default
inspect dns
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect ip-options
inspect ipsec-pass-thru
inspect netbios
inspect pptp
inspect rsh
inspect rtsp
inspect sip
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
inspect icmp
inspect icmp error
class http-map1
set connection advanced-options mss-map
policy-map http-map1
class http-map1
set connection advanced-options mss-map
!
tuasa# sh run pol
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 4096
policy-map global_policy
class inspection_default
inspect dns
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect ip-options
inspect ipsec-pass-thru
inspect netbios
inspect pptp
inspect rsh
inspect rtsp
inspect sip
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
inspect icmp
inspect icmp error
class http-map1
set connection advanced-options mss-map
policy-map http-map1
class http-map1
set connection advanced-options mss-map
!
and
tuasa# sh run pol
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 4096
policy-map global_policy
class inspection_default
inspect dns
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect ip-options
inspect ipsec-pass-thru
inspect netbios
inspect pptp
inspect rsh
inspect rtsp
inspect sip
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
inspect icmp
inspect icmp error
class http-map1
set connection advanced-options mss-map
policy-map http-map1
class http-map1
set connection advanced-options mss-map
!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Sorry,
tuasa# sh run access-group
access-group To-IBSng-AAA_access_in in interface outside
access-group outside_access_out out interface outside
access-group To-IBSng-AAA_access_in in interface To-IBSng-AAA
access-group To-IBSng-AAA_access_out out interface To-IBSng-AAA
access-group To-CoreSwitch-int_Backup_a
access-group To-CoreSwitch-int_Backup_a
tuasa#
tuasa# sh run access-group
access-group To-IBSng-AAA_access_in in interface outside
access-group outside_access_out out interface outside
access-group To-IBSng-AAA_access_in in interface To-IBSng-AAA
access-group To-IBSng-AAA_access_out out interface To-IBSng-AAA
access-group To-CoreSwitch-int_Backup_a
access-group To-CoreSwitch-int_Backup_a
tuasa#
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Dear Gammelgaard,
There are alot of entries in these ACLs.
sh-access-list-outside_acc
sh-access-list-To-IBSng-AA
There are alot of entries in these ACLs.
sh-access-list-outside_acc
sh-access-list-To-IBSng-AA
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hooray!!!
It is solved,
Dear Gammelgaard,
Dear ArchiTech89,
I really appreciate your concern and help.
After your affirmation on having access problem, I decide to look for inside access-lists and ... so I monitor traffic for both pinging 4.2.2.4 and 185.79.62.3. I found that destination replies does not return to same source back! 4.2.2.4 replies are to my IP address but 185.79.62.3 returns to another IP (our RAS server! before ASA). However tracert to 185.79.62.3 passes the RAS successfully and this brings me to spend a lot of time for troubleshooting.
I remove the screwy rules and every things are OK now.
Thank you for taking the trouble to help me again.
Zolfaghar
It is solved,
Dear Gammelgaard,
Dear ArchiTech89,
I really appreciate your concern and help.
After your affirmation on having access problem, I decide to look for inside access-lists and ... so I monitor traffic for both pinging 4.2.2.4 and 185.79.62.3. I found that destination replies does not return to same source back! 4.2.2.4 replies are to my IP address but 185.79.62.3 returns to another IP (our RAS server! before ASA). However tracert to 185.79.62.3 passes the RAS successfully and this brings me to spend a lot of time for troubleshooting.
I remove the screwy rules and every things are OK now.
Thank you for taking the trouble to help me again.
Zolfaghar
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
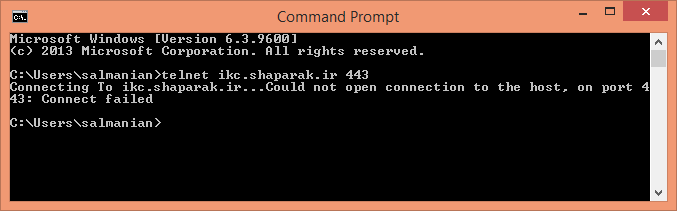
telnet ikc.shaparak.ir 443
If black screen, you are allowed to establish TCP connection with that server.
Check with ping ikc.shaparak.ir gets the same IP address from behind and in front of the ASA - you should do an ipconfig -flushdns before second try if using same PC
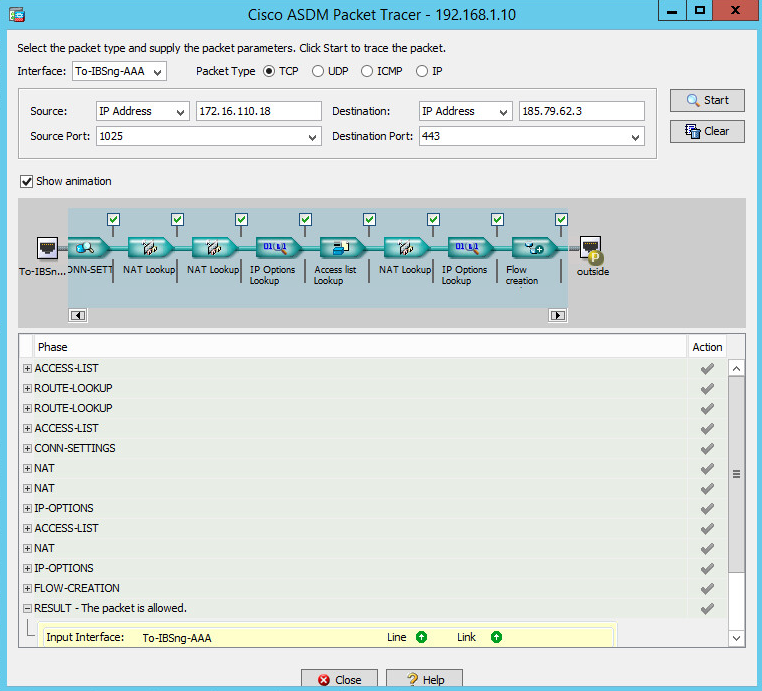
On ASA, use packet tracer to check how it is processing packet:
packet-tracer in inside tcp inside.ip.address 1025 outside.ip.address 443