Grant drive/folder change permissions to VPN user
A Server 2012 Datacenter user needs full control access in a Server 2012 R2 NTFS folder. The servers are set up via a site-to-site VPN and are in different workgroups. Active Directory for a domain is not involved and won't be. How can I allow the user full rights to the NTFS folder?
Visual of situation:
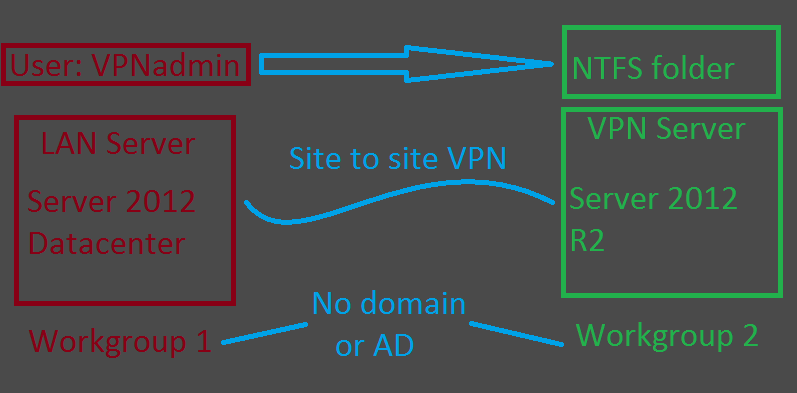
Visual of situation:

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
password you need to place in BAT or CMD file so someone can read it
ASKER
Understood. I have admin rights to both so I can enter it myself. I will test and let you know.
Is it working for you ?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER