Domain controller keeps issuing itself a certificate daily
I have a domain controller that I am using with a onesign appliance for ldap synchronization using TLS. I recently began having problems with this synchronization and I had to synch manually. When I went to sync, the onesign appliance would complain that the certificate was not issued by a trusted ca and do I want to use it. The certificate has the current date and expires a year from that date. If you click Yes, the certificate is imported into onesign and the sync happens fine. The next day, it happens again ... it complains about the certificate and shows it as being valid from today's date to a year down the road. I checked on the domain controller in the local certificate store, Personal and I see the certificate there. It changes every day which breaks my onesign synchronization again.
Why is the DC issuing itself a new certificate each day at 4:58am? I can't think of any changes to the environment that would have caused this to happen.
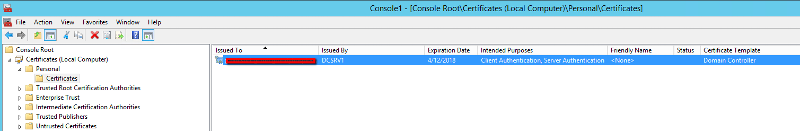
Why is the DC issuing itself a new certificate each day at 4:58am? I can't think of any changes to the environment that would have caused this to happen.

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
in fact expired certificate will not be used even if they remain stored. They have been been replaced with the existing new certificate in the same store, so those expired ones can be deleted. Just to share, even when a certificate is deleted, the corresponding private key is not deleted. Seems that the only solution is to manually delete files from %appdata%\Microsoft\Crypto
ASKER
This seems to have worked well. Thanks.
ASKER
certs.txt