Watchguard Firewall X750e - Cannot ping internal lan on watchguard from TPG IPVPN
Recently we added a new TPG IPVPN Connection (MPLS Network with Hosted Firewall) to eth2 on our watchguard but cant get it to work properly (see attached picture)
For some reason i cannot ping any Sydney LAN IP Addresses (on 10.50.2.0/24 network) from QLD Office to Sydney Office.
What do i need to enable / configure on the wathguard so i can ping internal lan addresses from qld office ?
QLD Office LAN is on 10.4.26.0/24 network.
Sydney office LAN is on 10.50.2.0/24 network
From QLD office I can ping 210.10.228.14,210.10.228.1
Sydney Office Watchguard Configuration is as follows:
I have 3 interfaces setup on my Watchguard x750e firewall with following parameters:
Eth0: IP: 210.10.228.14 (External) - This is connected to a ISP Managed Cisco 1900 Series Router. This is a routed subnet services TPG NBN Conneciton.
Gateway: 210.10.228.13
NetMask:255.255.255.252
Eth1: IP: 10.50.2.90 (Trusted)
Netmask: 255.255.255.0
Eth2: IP: 10.252.0.6 (External) - This is connected to a TPG NTU and is a IPVPN Connection. This also requires RIPv2 and has dynamic routing setup.
Gateway: 10.252.0.5
Netmask: 255.255.255.252
Dynamic Routing Configuration:
1. Enabled Dynamic Routing is enabled.
2. Enable RIP is enabled
Rip Configuration :
router rip
network 10.252.0.4/30
network 10.252.0.5/30
network 10.252.0.6/30
network 10.252.0.7/30
Routing Table of Watchguard looks like this:
**
** Routes
**
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
202.10.2.20 10.252.0.5 255.255.255.255 UGH 0 0 0 eth2
210.10.228.12 0.0.0.0 255.255.255.252 U 0 0 0 eth0
10.252.0.4 0.0.0.0 255.255.255.252 U 0 0 0 eth2
10.252.0.8 10.252.0.5 255.255.255.252 UG 0 0 0 eth2
10.252.0.12 10.252.0.5 255.255.255.252 UG 0 0 0 eth2
172.50.1.88 10.252.0.5 255.255.255.248 UG 0 0 0 eth2
192.168.113.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
10.50.2.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
10.4.26.0 10.252.0.5 255.255.255.0 UG 0 0 0 eth2
127.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 lo
TPG Network Diagram
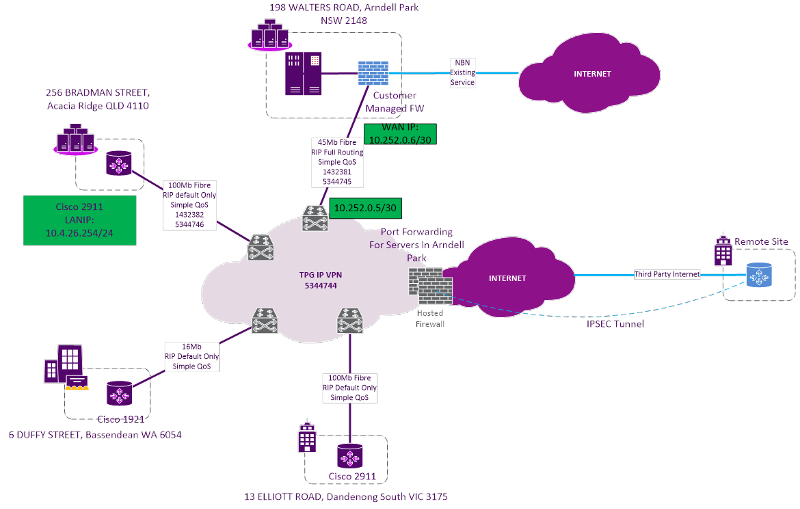
For some reason i cannot ping any Sydney LAN IP Addresses (on 10.50.2.0/24 network) from QLD Office to Sydney Office.
What do i need to enable / configure on the wathguard so i can ping internal lan addresses from qld office ?
QLD Office LAN is on 10.4.26.0/24 network.
Sydney office LAN is on 10.50.2.0/24 network
From QLD office I can ping 210.10.228.14,210.10.228.1
Sydney Office Watchguard Configuration is as follows:
I have 3 interfaces setup on my Watchguard x750e firewall with following parameters:
Eth0: IP: 210.10.228.14 (External) - This is connected to a ISP Managed Cisco 1900 Series Router. This is a routed subnet services TPG NBN Conneciton.
Gateway: 210.10.228.13
NetMask:255.255.255.252
Eth1: IP: 10.50.2.90 (Trusted)
Netmask: 255.255.255.0
Eth2: IP: 10.252.0.6 (External) - This is connected to a TPG NTU and is a IPVPN Connection. This also requires RIPv2 and has dynamic routing setup.
Gateway: 10.252.0.5
Netmask: 255.255.255.252
Dynamic Routing Configuration:
1. Enabled Dynamic Routing is enabled.
2. Enable RIP is enabled
Rip Configuration :
router rip
network 10.252.0.4/30
network 10.252.0.5/30
network 10.252.0.6/30
network 10.252.0.7/30
Routing Table of Watchguard looks like this:
**
** Routes
**
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
202.10.2.20 10.252.0.5 255.255.255.255 UGH 0 0 0 eth2
210.10.228.12 0.0.0.0 255.255.255.252 U 0 0 0 eth0
10.252.0.4 0.0.0.0 255.255.255.252 U 0 0 0 eth2
10.252.0.8 10.252.0.5 255.255.255.252 UG 0 0 0 eth2
10.252.0.12 10.252.0.5 255.255.255.252 UG 0 0 0 eth2
172.50.1.88 10.252.0.5 255.255.255.248 UG 0 0 0 eth2
192.168.113.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
10.50.2.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
10.4.26.0 10.252.0.5 255.255.255.0 UG 0 0 0 eth2
127.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 lo
TPG Network Diagram

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ended up replacing Watchguard Firewall with Hosted Firewall Solution