Router Configuration for web site
I have a web site on my IIS server, which was accessible on the LAN. I have two initial goals:
1) put the IIS server in a DMZ
2) configure the router so that the web site is accessible from the outside world
I moved the IIS server from the LAN port on my router to the DMZ port. The router initially had firewall rules allowing access to the DMZ for all traffic from Any to Any. I created a rule that denies access to the DMZ for all traffic from Any to Any, and then created a rule that allows access to the DMZ for HTTP requests from Any to Any.
I then created a port forwarding rule to forward HTTP/ port 80 to the internal IP address of the server.
I still can't access the web site externally. And I can't access or ping the server from the LAN.
Ideas on what I need to change here?
Cisco RV325 router

1) put the IIS server in a DMZ
2) configure the router so that the web site is accessible from the outside world
I moved the IIS server from the LAN port on my router to the DMZ port. The router initially had firewall rules allowing access to the DMZ for all traffic from Any to Any. I created a rule that denies access to the DMZ for all traffic from Any to Any, and then created a rule that allows access to the DMZ for HTTP requests from Any to Any.
I then created a port forwarding rule to forward HTTP/ port 80 to the internal IP address of the server.
I still can't access the web site externally. And I can't access or ping the server from the LAN.
Ideas on what I need to change here?
Cisco RV325 router


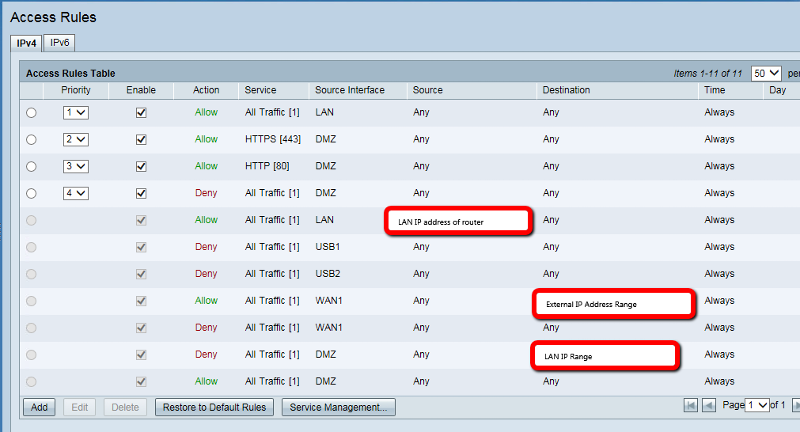
rule order is important,
In general the order is:
- Deny Specific if needed
- Allow specific if needed
- Allow generic or Deny generic depending on security model.
A variance for the last can be
Deny specific without log
Deny generic with log
To not log several known cases, but do log ( & thus inspect the logs) for unknown cases.
During setup of e new set the last ones can be
Allow Specific
Allow generic with logging
To not disrupt any running services and then later fine tune the filters before closing up the holes.
Also in most cases you need to allow traffic the the internal address.....
Mostly the router is in the middle... Dest NAT has been performed, while sournat will bedone on transmission.
so the Filter rules should match Original source and Destination AFTER Portforward NAT has been performed...
So don't use the EXternal address of your server, but the internal address of you server.....
In case you are not shure, add bot with logging and see which one hits.
In general the order is:
- Deny Specific if needed
- Allow specific if needed
- Allow generic or Deny generic depending on security model.
A variance for the last can be
Deny specific without log
Deny generic with log
To not log several known cases, but do log ( & thus inspect the logs) for unknown cases.
During setup of e new set the last ones can be
Allow Specific
Allow generic with logging
To not disrupt any running services and then later fine tune the filters before closing up the holes.
Also in most cases you need to allow traffic the the internal address.....
Mostly the router is in the middle... Dest NAT has been performed, while sournat will bedone on transmission.
so the Filter rules should match Original source and Destination AFTER Portforward NAT has been performed...
So don't use the EXternal address of your server, but the internal address of you server.....
In case you are not shure, add bot with logging and see which one hits.
ASKER
The rules that don't have a priority are the router's default ones, and I'm unable to move them around. According to Cisco, the rules are applied IN ORDER, from the TOP. The first match found will be the only rule that's applied.
But I also pulled all of the custom rules and set the rules back to the default (the ones at the bottom, without a priority), and that did not resolve the problem. I'm able to ping the external IP of the DMZ port, but not telnet to port 80.
And to answer the earlier question about multiple IP addresses: I have multiple external IP addresses. At the moment, one address is assigned to WAN1, and the other to DMZ.
I would prefer NOT to use DMZ host because I want the IIS server separated from the LAN computers. DMZ Host is a software firewall. I want a hardware firewall, which is why I have a router with a DMZ port.
@noci - I'm not sure I follow what you're saying about allowing traffic to the internal address.
But I also pulled all of the custom rules and set the rules back to the default (the ones at the bottom, without a priority), and that did not resolve the problem. I'm able to ping the external IP of the DMZ port, but not telnet to port 80.
And to answer the earlier question about multiple IP addresses: I have multiple external IP addresses. At the moment, one address is assigned to WAN1, and the other to DMZ.
I would prefer NOT to use DMZ host because I want the IIS server separated from the LAN computers. DMZ Host is a software firewall. I want a hardware firewall, which is why I have a router with a DMZ port.
@noci - I'm not sure I follow what you're saying about allowing traffic to the internal address.
Rumour has it that the RV325 needs to have a dedicated IP address for the DMZ port.
In your scenario you are using the same hardware for the DMZ, so creating a new VLAN for the IIS server (which doesn't have the dedicated IP requirement) will achieve the same thing as the DMZ configuration. You can still protect the IIS server in exactly the same way as you would if it were in a DMZ.
In your scenario you are using the same hardware for the DMZ, so creating a new VLAN for the IIS server (which doesn't have the dedicated IP requirement) will achieve the same thing as the DMZ configuration. You can still protect the IIS server in exactly the same way as you would if it were in a DMZ.
ASKER
I have a dedicated IP for the DMZ port.
To confirm, that's a dedicated public IP from your ISP?
ASKER
Yes. I have a block of several external, static IP addresses from my ISP. I've assigned one to WAN1, and a different one to the DMZ port. In both configs, I'm using the subnet given to me by the ISP, which is 255.255.255.248
I'm not sure if the subnet should be changed, or whether I should just use what the ISP gave me as the subnet.
I'm not sure if the subnet should be changed, or whether I should just use what the ISP gave me as the subnet.
You should be ok as you are.
Have you tried creating a firewall rule that allows all coming in to the DMZ port to get to the real IP of the IIS server?
Have you tried creating a firewall rule that allows all coming in to the DMZ port to get to the real IP of the IIS server?
ASKER
Yes, I've tried that.
I actually think I may have a possible solution. I'll try it on Monday.
Here are the two leads:
First, the post by Sleeman here: http://www.linksysinfo.org/index.php?threads/rv042-dmz-help-needed.849/
Sleeman points out that subnet mask plays an important point. The ISP gave me .17 - .22 with a mask of 255.255.255.248. When I used that .17 address on my DMZ port, the router automatically configured an access rule for WAN from Any -> range .16 - .23
That stuck out to me, and I couldn't make sense of it. Until I read Sleeman's post, which reminded me of the subnet masking I learned a LONG time ago.
So, first step on Monday is to change the DMZ config to .20
Second, the answer here : https://www.experts-exchange.com/questions/27327908/DMZ-INternet-Port-on-Cisco-RV042.html
It says that the web server needs to be given an EXTERNAL ip address. In my case, I believe I need to give it the .20 address I've assigned to my DMZ port. And, I think the Gateway on that server needs to be set to .16 ???
I'll post more on Monday once I've tried those changes.
I actually think I may have a possible solution. I'll try it on Monday.
Here are the two leads:
First, the post by Sleeman here: http://www.linksysinfo.org/index.php?threads/rv042-dmz-help-needed.849/
Sleeman points out that subnet mask plays an important point. The ISP gave me .17 - .22 with a mask of 255.255.255.248. When I used that .17 address on my DMZ port, the router automatically configured an access rule for WAN from Any -> range .16 - .23
That stuck out to me, and I couldn't make sense of it. Until I read Sleeman's post, which reminded me of the subnet masking I learned a LONG time ago.
So, first step on Monday is to change the DMZ config to .20
Second, the answer here : https://www.experts-exchange.com/questions/27327908/DMZ-INternet-Port-on-Cisco-RV042.html
It says that the web server needs to be given an EXTERNAL ip address. In my case, I believe I need to give it the .20 address I've assigned to my DMZ port. And, I think the Gateway on that server needs to be set to .16 ???
I'll post more on Monday once I've tried those changes.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
yeah, this is definitely an IP related issue. Before I read your last post, I changed the DMZ port config in the router to external IP x.x.x.20, and then changed the IIS Server from an internal IP to that same x.x.x.20 address. I then set the Gateway on the IIS Server to the same Gateway for the WAN1, which is x.x.x.22
My WAN is x.x.x.18
I can now telnet to port 80 and reach my website from the outside world.
Does it matter that the Gateway on the IIS Server is not the address of the WAN (x.x.x.18) ? One reason why I'd prefer to keep it the way I currently have it is because I set up a rule to deny all traffic on the WAN port from Any -> x.x.x.18 .
My WAN is x.x.x.18
I can now telnet to port 80 and reach my website from the outside world.
Does it matter that the Gateway on the IIS Server is not the address of the WAN (x.x.x.18) ? One reason why I'd prefer to keep it the way I currently have it is because I set up a rule to deny all traffic on the WAN port from Any -> x.x.x.18 .
The gateway needs to be whatever the IP on the DMZ port is for routing to work.
ASKER
I currently have the IP of the IIS Server set to the external IP address that I set up for the DMZ port. So both the DMZ port and the IIS Server have address x.x.x.20 (an external IP).
I did that based on the answer I read here: https://www.experts-exchange.com/questions/27327908/DMZ-INternet-Port-on-Cisco-RV042.html
And everything seems to be working ok. I can access the website on the IIS server from the outside world, and I set up an access rule in the firewall to allow traffic to the website's backend database that's on a server on the LAN.
But from what I believe you're saying I should have an internal IP assigned to the server, with Gateway pointing to the external IP address on WAN1 ?
Is there a potential problem with the way I currently have it set up?
I did that based on the answer I read here: https://www.experts-exchange.com/questions/27327908/DMZ-INternet-Port-on-Cisco-RV042.html
And everything seems to be working ok. I can access the website on the IIS server from the outside world, and I set up an access rule in the firewall to allow traffic to the website's backend database that's on a server on the LAN.
But from what I believe you're saying I should have an internal IP assigned to the server, with Gateway pointing to the external IP address on WAN1 ?
Is there a potential problem with the way I currently have it set up?
No two devices should have the same IP, but if it's working and it's stable I'd see how it goes.
It's interesting that the other answer you mentioned says to clear the ARP cache as that implies that traffic is being sent to the wrong device sometimes (as per an IP conflict).
It's interesting that the other answer you mentioned says to clear the ARP cache as that implies that traffic is being sent to the wrong device sometimes (as per an IP conflict).
ASKER
I will give your suggestion a try, and assign an internal IP to the server, and change the Gateway to the address of WAN1.
I was saying that the gateway should be the address of the DMZ port.
Try moving all of the allow rules to be ahead of the deny rules.
But also, you need multiple public IP addresses for the normal DMZ option. How many public IP addresses do you have? However you can utilize the DMZ host option which may work out better for you.