networking with multiple internet connections
we have a network that has load balancing on a pfsense 8860 router.
We want to add wireless for the guests, and a second SSID for anyone who needs to access the internal network, we were thinking on a separate internet connection for the access points, I am including a diagram of our thought ( at least that is the thought at the moment)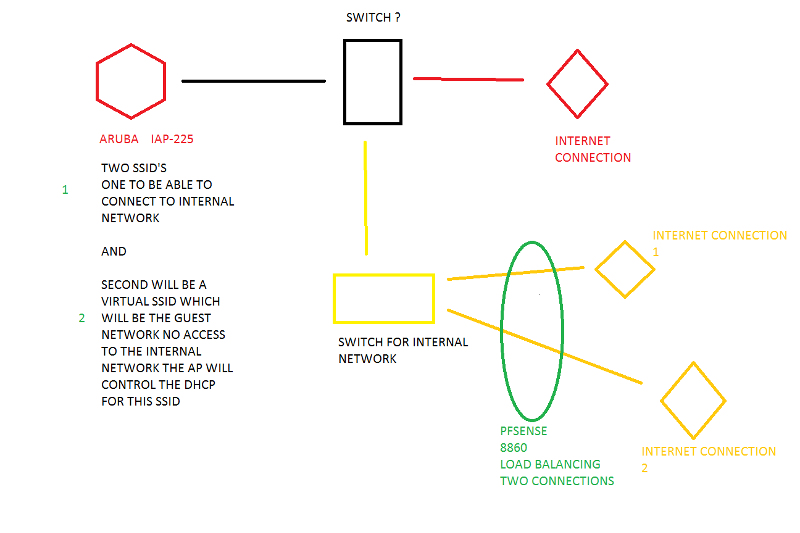 we are going to use Aruba IAP225 access points.
we are going to use Aruba IAP225 access points.
We will create two SSID's one for accessing the internal network and one that is a Virtual Guest SSID which the Aruba AP will control the DHCP of.
We want to make sure that the internal networks data is protected from any of the guests who connect, so that nothing can trickle over.
I had another thought which may not be the most intelligent but I was thinking if the aruba ap's were left on the seperate internet connection and I already have openvpn setup on the PFSESNE for remote connection; could I setup a vpn tunnel for the one ssid's to the PFsense router to access the internal network, would that be the safest way to keep the internal networks data safer?
I am not sure the best way to execute this. If there is an easier and more efficient way please let me know
thanks
We want to add wireless for the guests, and a second SSID for anyone who needs to access the internal network, we were thinking on a separate internet connection for the access points, I am including a diagram of our thought ( at least that is the thought at the moment)
 we are going to use Aruba IAP225 access points.
we are going to use Aruba IAP225 access points.We will create two SSID's one for accessing the internal network and one that is a Virtual Guest SSID which the Aruba AP will control the DHCP of.
We want to make sure that the internal networks data is protected from any of the guests who connect, so that nothing can trickle over.
I had another thought which may not be the most intelligent but I was thinking if the aruba ap's were left on the seperate internet connection and I already have openvpn setup on the PFSESNE for remote connection; could I setup a vpn tunnel for the one ssid's to the PFsense router to access the internal network, would that be the safest way to keep the internal networks data safer?
I am not sure the best way to execute this. If there is an easier and more efficient way please let me know
thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
that can work, as well as setting up a new subnet on a another Lan interface within the pfsense router and connect that interface to and another Access point which would be totally segregated network since you do not understand vlans
ASKER
Excellent
- Implement a secondary layer 3 switch and a firewall, or a router with firewall capabilities with the gateway pointing to your new ISP.
- You may have to create an additional VLAN on your existing layer 3 switch / router depending where it is situated in your network, as you will have to add routing to point to the next hop.
- You can actually utilize your existing DHCP server to serve addresses to this new VLAN.
- When you create your new DHCP scope, you would be putting the gateway of your new ISP router and external DNS addresses.
- Create your secondary SSID for your guest clients, with the gateway of your new router/ISP
This will separate your guest and business traffic. It will also able you to centralize your DHCP server and not have to utilize your AP's DHCP server.
This is a secure and in my opinion best practice way of dividing public traffic from your business network.
Quick network pic attached