Avoid network collapse
Hello everyone!. I was wondering if anyone could help me with this. At the office, it is the second time the whole network stop working because of external causes. The first time somebody connected a patch core from one wall socket to another and everything collapsed....it took me some hours to realized what was happening...The last time, cleaning personal accidentally moved a switch connected to wall socket and because of it almost all packets were lost, again it took me some time to find it out...
Is there any recommendation or advice in order to prevent future problems like this?. I have dlink switches.
Thanks in advance
Is there any recommendation or advice in order to prevent future problems like this?. I have dlink switches.
Thanks in advance
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
exactly as Sean said. You have a spanning tree loop problem. Its a fundamental feature available on enterprise quality switches and routers. If you do not have STP-capable network equipment then you will need to consider upgrading, because this kind of loop will keep happening if you cannot enable STP.
Physical security.
Why do other people (cleaning people) have access to where the switch is?
Otherwise, it's been a VERY long while but I recall a problem with spanning tree at one of my past clients. It may work fine for you, but another solution is simply NOT activating ports that don't need to be activated. This is also a security technique.
Why do other people (cleaning people) have access to where the switch is?
Otherwise, it's been a VERY long while but I recall a problem with spanning tree at one of my past clients. It may work fine for you, but another solution is simply NOT activating ports that don't need to be activated. This is also a security technique.
Others have stated spanning tree, that is partially correct. What you really want here is BPDUGuard, as it will administratively (err-disable) those ports when it receives a BPDU on any edge port.
What kind of switches? Cisco switches you would do the following:
Additionally, Cisco has another command which enable some more security features:
This macro does the following:
This should be used in conjunction with BPDU guard on your edge ports (ports going towards client computers only)
What kind of switches? Cisco switches you would do the following:
(config-if)# spanning-tree bpduguard enableAdditionally, Cisco has another command which enable some more security features:
(config-if)# switchport hostThis macro does the following:
(config-if)# switchport mode access
(config-if)# spanning-tree portfast
(config-if)# no channel-groupThis should be used in conjunction with BPDU guard on your edge ports (ports going towards client computers only)
ASKER
Thank you all for your replies!. Unfortunately I have DLINK switches....About the question, the cleaning personal had access not to the enterprise switches but to an small little switch that we had to use in order to use more ports than available at that place.
ASKER
BTW, does anyone know how to configure STP on a DLINK 3420-28TC ?
I believe it is just enable stp
The DLink 3420 is a managed switch, there should be an option in the CLI or the web interface to enable STP. It is possible STP is enabled by default and that you just need to enable BPDU Guard (the DLink equivalent that is)
ASKER
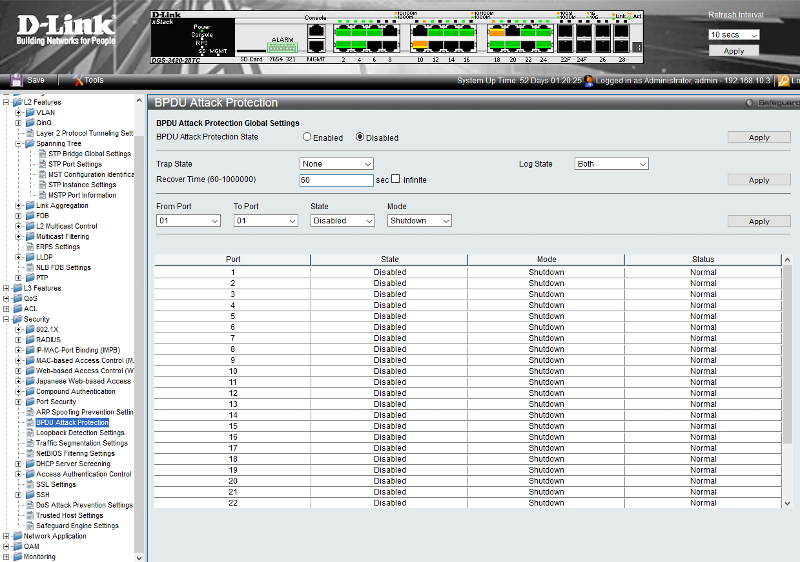
I have these options:
-Security
-BPDU Attack Protection Global Settings
-L2 Features
-Spanning Tree
-STP Bridge Global Settings
-STP Port Settings
-MST Configuration Identification
-STP Instance Settings
-MSTP Port Information
-Security
-BPDU Attack Protection Global Settings
-L2 Features
-Spanning Tree
-STP Bridge Global Settings
-STP Port Settings
-MST Configuration Identification
-STP Instance Settings
-MSTP Port Information
On your web interface you want to enable all the ports that are not trunk ports for the BPDU attack.
at the top of that interface that you posted, select "enabled" to globally set it then click the "apply" button.
If STP is enabled you don't "need" BPDUGuard, but it will help. STP should be enough though.
BPDUGuard will disable a port if a BPDU is received on it. STP will block a port if a loop is detected. If you loop 2 ports on a switch you'll get both a loop and a BPDU. STP alone will deal with that.
BPDUGuard will disable a port if a BPDU is received on it. STP will block a port if a loop is detected. If you loop 2 ports on a switch you'll get both a loop and a BPDU. STP alone will deal with that.
ASKER
So STP is enough then?. Do you know how to enable it?. Because there are lot of options right there.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
If you loop a dumb switch you won't see a BPDU as they don't generate them. You would only see a BPDU if the unmanaged switch had multiple links to the same L2 segment at the managed switch.
You can only really detect an unmanaged switch which is looped at itself by using storm control on the managed switch edge ports.
You can only really detect an unmanaged switch which is looped at itself by using storm control on the managed switch edge ports.
ASKER
Thank you everyone. Summing up...BPDU or STP. Which one would be my best choice?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you everyone!.
No probs but you chose the wrong answer.
Also, if you use BPDU Guard (even though you don't need to) you can automatically recover from it using errdisable recovery once the link is disconnected.
Also, if you use BPDU Guard (even though you don't need to) you can automatically recover from it using errdisable recovery once the link is disconnected.