Cisco autonomous AP SSID mapping with NPS policy
hello experts
i will using Cisco autonomous AP to setup wireless network for users, they will separated with VLAN for wireless they will using different SSID base on different department, i will using NPS as the authentication server, my question is how can i mapping different SSID to different policy on NPS?
on the NPS configuration wizard i noticed that there is a option calling-station-ID and called-station-ID, not sure i can using this option or not, but i don't know how to configure calling called station ID on SSID, please advice.
thank you
i will using Cisco autonomous AP to setup wireless network for users, they will separated with VLAN for wireless they will using different SSID base on different department, i will using NPS as the authentication server, my question is how can i mapping different SSID to different policy on NPS?
on the NPS configuration wizard i noticed that there is a option calling-station-ID and called-station-ID, not sure i can using this option or not, but i don't know how to configure calling called station ID on SSID, please advice.
thank you
ASKER
ASKER
and i just tried it as the screenshot setting, but not works, please advice.
thank you
thank you
Can you post the NPS log?
ASKER
is this fine?
thanks
<Event><Timestamp data_type="4">09/21/2017 15:31:18.418</Timestamp><C
thanks
<Event><Timestamp data_type="4">09/21/2017 15:31:18.418</Timestamp><C
ASKER
hello, any ideas?
thank you
thank you
Can you pull the log from the Windows Custom Logs please, they're easier to interpret?
ASKER
hello Craig
i did try it but i could not find related log from windows log, what i should do to filter such log out?
thank you
i did try it but i could not find related log from windows log, what i should do to filter such log out?
thank you
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
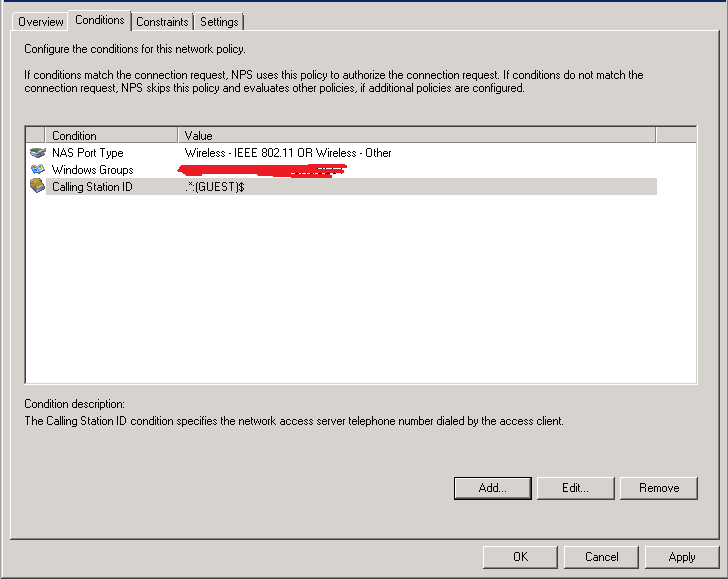
.*:(YOUR_SSID)$