protect against ransomware with access policy to limit programs that can write to data files
Greetings,
For all the programming and brainpower that goes into protecting systems today, anti-virus programs are always going to be desperately playing catch-up when it comes to zero-day attacks, I would like to create an access policy through Windows that looks something like this:
Name: Block access to *.doc except for winword and other allowed programs
Processes to include: * (all)
Exceptions: winword.exe, chrome.exe, adobe.exe, explorer.exe (there are more to include, this is just an example)
File/folder name to bloc: *.DOC
Actions to block" Write access to files, New files being created
With the above policy in place, an illegitimate ransomware virus executable, e.g. deathstar.exe, would be unable to write to the data files because the access policy would block their efforts to write to and encrypt the protected data files.
I would want to do this for all main file types, e.g. *.doc/docx, *.xls/xlsx, *.pdf etc.
With what tools can I put these rules into place on a given Windows XP / 8 / 10 PC and/or on a Windows 2008 / 2012 / 2016 server?
Thanks.
jkirman
For all the programming and brainpower that goes into protecting systems today, anti-virus programs are always going to be desperately playing catch-up when it comes to zero-day attacks, I would like to create an access policy through Windows that looks something like this:
Name: Block access to *.doc except for winword and other allowed programs
Processes to include: * (all)
Exceptions: winword.exe, chrome.exe, adobe.exe, explorer.exe (there are more to include, this is just an example)
File/folder name to bloc: *.DOC
Actions to block" Write access to files, New files being created
With the above policy in place, an illegitimate ransomware virus executable, e.g. deathstar.exe, would be unable to write to the data files because the access policy would block their efforts to write to and encrypt the protected data files.
I would want to do this for all main file types, e.g. *.doc/docx, *.xls/xlsx, *.pdf etc.
With what tools can I put these rules into place on a given Windows XP / 8 / 10 PC and/or on a Windows 2008 / 2012 / 2016 server?
Thanks.
jkirman
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Controlled folder access may not allow to specify till file extension like *.docx etx though it can define the folder and whitelisted apps in the rules. Just a note, it won’t protect against malware viewing and making copies of your files. It only protects against malware changing these files. But probably that is good enough so long you have a original copy intact.
https://docs.microsoft.com/en-us/windows/threat-protection/windows-defender-exploit-guard/controlled-folders-exploit-guard
There is an equivalent for server called FSRM, which it can be added via Roles and Features. It would include the mentioned file extension.
https://gallery.technet.microsoft.com/scriptcenter/Protect-your-File-Server-f3722fce
https://docs.microsoft.com/en-us/windows/threat-protection/windows-defender-exploit-guard/controlled-folders-exploit-guard
There is an equivalent for server called FSRM, which it can be added via Roles and Features. It would include the mentioned file extension.
https://gallery.technet.microsoft.com/scriptcenter/Protect-your-File-Server-f3722fce
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Thanks McKnife. FSRM is indeed more of file screening as compared to whitelisting of application or executables. It would have met one if the use case to prevent any overwrite into that same folder another filename (with new extension..)
Question is not really answered since the author looked for methods on all windows OS' and not just win10. Author needs to return with feedback. Thomas' answer applies to all OS' and though not ransomware specific, the tool will at least prevent some malwares from starting.
So my recommendation is: on win10 v1709, test controlled folder access. On other OS' rely on applocker/software restriction policies or other whitelisting apps like Thomas'.
So my recommendation is: on win10 v1709, test controlled folder access. On other OS' rely on applocker/software restriction policies or other whitelisting apps like Thomas'.
ASKER
Greetings,
First and foremost – sincere apologies to all who have submitted answers and comments for my lack of response to date, and many thanks for your thoughts and discussions on the question I submitted. Please note that I was in no way intending to abandon this question, nor to be non-responsive to your postings. In the past I have always received email notifications whenever comments were provided, but I have not received notifications of any kind from Experts Exchange over the last few weeks, so I assumed that no one had yet commented on the question. Unless that’s the new norm (which I doubt) I’ll need to review with a site moderator as to why the notifications haven’t come in. On that note I did check my anti-SPAM server, and the experts-exchange.com domain was whitelisted years ago.
With regards to your responses and thoughts:
btan 42337541
FSRM is clearly a powerful tool, though it involves PS scripting which I’ve very little experience on. Also as McKnife mentioned it appears that its focus is to block creation of certain file types, .XXX for example. Although this can definitely be useful in preventing Ransomware from creating its temporary and related files, I’m looking to screen and control activities and file writes to specific file types from the application side.
McKnife 42337379 and 42337835 Controlled Folder Access
In the case of Controlled folder access, I’m understanding that Windows Defender AV does the evaluation of the app to see if it is safe or threatening, and then either permits or blocks its access to a folder. This defaults to protecting common system folders, and you can specify additional folders as McKnife mentioned using UNC paths. This is more in line with that I’m looking to accomplish. However I’m seeing from some reviews that it may not work well with 3rd party AV tools (Mcafee / Symantec), which I’ve worked with for many years, and I would be very hesitant to stop using. I’ll be reviewing this further to see if it can be tailored to what I need and if there is a workaround from Microsoft as to whether the Windows Defender can somehow work in tandem with existing protection schemes.
by:Thomas Zucker-Scharff D: 42337102 CryptoPrevent
Thomas, I did a brief lookup following your suggestion regarding CryptoPrevent, which the manufacturer says should be used alongside existing protection schemes. It does offer the ability to whitelist programs in protected folder areas, which sounds close to what I’m looking for. I did see a review in PC Mag from May 31st where it didn’t do too well:
https://www.pcmag.com/review/353931/cryptoprevent-premium-8
but perhaps later versions have evaluated better . I will still get a trial and test it out to see how it works with existing protection schemes.
Also, you mentioned greylisting as something to check into. Did you possibly mean application whitelisting instead? I checked into application greylisting and could only find references to spam handling. FWIW I do employ greylisting in my anti-SPAM solutions, which is invaluable as it knocks out 95% or more of SPAM before it even comes into the server. Application whitelisting though sounds again similar to what I’m looking for, since it controls and limits which apps can be run, though I can’t tell at this point if it can be linked to protecting specific file types based on the application. I’ll look to test out a couple of these apps, e.g. Mcafee Application Control and Carbon Black, and see if they can deliver the solution I’m seeking.
So the solutions I’ll be using going forward are:
McKnife 42337379 / 42337835 Controlled Folder Access
and
Thomas Zucker-Scharff D: 42337102 CryptoPrevent
My sincere thanks again to you all for your input, and apologies again for my not checking back on this much sooner.
Cheers
jkirman
First and foremost – sincere apologies to all who have submitted answers and comments for my lack of response to date, and many thanks for your thoughts and discussions on the question I submitted. Please note that I was in no way intending to abandon this question, nor to be non-responsive to your postings. In the past I have always received email notifications whenever comments were provided, but I have not received notifications of any kind from Experts Exchange over the last few weeks, so I assumed that no one had yet commented on the question. Unless that’s the new norm (which I doubt) I’ll need to review with a site moderator as to why the notifications haven’t come in. On that note I did check my anti-SPAM server, and the experts-exchange.com domain was whitelisted years ago.
With regards to your responses and thoughts:
btan 42337541
FSRM is clearly a powerful tool, though it involves PS scripting which I’ve very little experience on. Also as McKnife mentioned it appears that its focus is to block creation of certain file types, .XXX for example. Although this can definitely be useful in preventing Ransomware from creating its temporary and related files, I’m looking to screen and control activities and file writes to specific file types from the application side.
McKnife 42337379 and 42337835 Controlled Folder Access
In the case of Controlled folder access, I’m understanding that Windows Defender AV does the evaluation of the app to see if it is safe or threatening, and then either permits or blocks its access to a folder. This defaults to protecting common system folders, and you can specify additional folders as McKnife mentioned using UNC paths. This is more in line with that I’m looking to accomplish. However I’m seeing from some reviews that it may not work well with 3rd party AV tools (Mcafee / Symantec), which I’ve worked with for many years, and I would be very hesitant to stop using. I’ll be reviewing this further to see if it can be tailored to what I need and if there is a workaround from Microsoft as to whether the Windows Defender can somehow work in tandem with existing protection schemes.
by:Thomas Zucker-Scharff D: 42337102 CryptoPrevent
Thomas, I did a brief lookup following your suggestion regarding CryptoPrevent, which the manufacturer says should be used alongside existing protection schemes. It does offer the ability to whitelist programs in protected folder areas, which sounds close to what I’m looking for. I did see a review in PC Mag from May 31st where it didn’t do too well:
https://www.pcmag.com/review/353931/cryptoprevent-premium-8
but perhaps later versions have evaluated better . I will still get a trial and test it out to see how it works with existing protection schemes.
Also, you mentioned greylisting as something to check into. Did you possibly mean application whitelisting instead? I checked into application greylisting and could only find references to spam handling. FWIW I do employ greylisting in my anti-SPAM solutions, which is invaluable as it knocks out 95% or more of SPAM before it even comes into the server. Application whitelisting though sounds again similar to what I’m looking for, since it controls and limits which apps can be run, though I can’t tell at this point if it can be linked to protecting specific file types based on the application. I’ll look to test out a couple of these apps, e.g. Mcafee Application Control and Carbon Black, and see if they can deliver the solution I’m seeking.
So the solutions I’ll be using going forward are:
McKnife 42337379 / 42337835 Controlled Folder Access
and
Thomas Zucker-Scharff D: 42337102 CryptoPrevent
My sincere thanks again to you all for your input, and apologies again for my not checking back on this much sooner.
Cheers
jkirman
ASKER
Question closed and thanks again.
Hi jkirkman.
1st: about the notifications - those come in very reliable (I get dozens per day and I can verify that these are of the same number as the on-site notifications behind the "bell"-icon), so I would recheck your SPAM settings. The expert comment notification mails would originate from noreply@experts-exchange.c
2nd you write "However I’m seeing from some reviews that it may not work well with 3rd party AV tools (Mcafee / Symantec)" - could you please link what you are referring to? I'd like to review that.
1st: about the notifications - those come in very reliable (I get dozens per day and I can verify that these are of the same number as the on-site notifications behind the "bell"-icon), so I would recheck your SPAM settings. The expert comment notification mails would originate from noreply@experts-exchange.c
2nd you write "However I’m seeing from some reviews that it may not work well with 3rd party AV tools (Mcafee / Symantec)" - could you please link what you are referring to? I'd like to review that.
ASKER
McKnife,
Regarding my not getting email notifications, turns out that I hadn't checked my Experts email settings in a while. I had my old email address as the primary and the current one as secondary. I haven't used the old email address in ages, as it got very unreliable at one point several years ago, but it was still working for Experts notifications, and this is one of those situations where as long as something works, you don't have reason to look at it. I guess sometime in the last few months something began blocking the Experts notifications that were sent to the old address from getting through, and I only now found out about it. So the old address has been removed from the notification settings, and Experts notifications are now coming in as they should.
With regards to Windows Defender not working well with 3rd party AV tools, I was basing this on several user reviews. Here are a couple of the the articles I came across:
https://community.mcafee.com/thread/99068?tstart=0
https://answers.microsoft.com/en-us/protect/forum/all/can-windows-10-run-windows-defender-mcafee/8304b24f-0331-4801-8990-a375cdc4a0c8
From what I've both read and seen from my own experience, having 2 full AV products operating at the same time has a good probability of typing the system up in knots at some point. All you need is both AV processes to try and lock or scan the same file or process at the same time, and you have a possible embrace of death or at least a very long lock period until one times out. CPU usage can also spike much higher for the same reasons. Occasionally a client calls and says their PC is operating at a painfully slow pace, and when I check in the PC, I see they've installed 2 or 3 antimalware (or a freebie AV) programs, which are literally strangling the PC out of available CPU. Additionally, when I've installed Mcafee on any Win 7 system, it automatically offers to disable Windows defender. I understand Win 10 is supposed to be engineered to make Defender less obtrusive and less conflicting, but my metaphor on this is that 2 Marine drill sergeants barking differing orders at full blast simultaneously to one soldier is probably too much to handle for the one poor guy. In scanning a few more articles on this question, I am seeing some cases where the 2 programs have operated OK together, but a majority where they haven't. So based on the numbers pro and con regarding mixing them, and on just the nature of the beast itself, I'm going to avoid trying to be a pioneer on this one. All that said, I have had very good results with Mcafee and Malwarebytes operating together, as MWB seems to fill the gap of what Mcafee doesn't cover with respect to Malware. I've seen MWB identify and remove Ransomware / Lockie etc. where Mcafee never even detected it.
Hope the above articles are of use.
Cheers,
jkirman
Regarding my not getting email notifications, turns out that I hadn't checked my Experts email settings in a while. I had my old email address as the primary and the current one as secondary. I haven't used the old email address in ages, as it got very unreliable at one point several years ago, but it was still working for Experts notifications, and this is one of those situations where as long as something works, you don't have reason to look at it. I guess sometime in the last few months something began blocking the Experts notifications that were sent to the old address from getting through, and I only now found out about it. So the old address has been removed from the notification settings, and Experts notifications are now coming in as they should.
With regards to Windows Defender not working well with 3rd party AV tools, I was basing this on several user reviews. Here are a couple of the the articles I came across:
https://community.mcafee.com/thread/99068?tstart=0
https://answers.microsoft.com/en-us/protect/forum/all/can-windows-10-run-windows-defender-mcafee/8304b24f-0331-4801-8990-a375cdc4a0c8
From what I've both read and seen from my own experience, having 2 full AV products operating at the same time has a good probability of typing the system up in knots at some point. All you need is both AV processes to try and lock or scan the same file or process at the same time, and you have a possible embrace of death or at least a very long lock period until one times out. CPU usage can also spike much higher for the same reasons. Occasionally a client calls and says their PC is operating at a painfully slow pace, and when I check in the PC, I see they've installed 2 or 3 antimalware (or a freebie AV) programs, which are literally strangling the PC out of available CPU. Additionally, when I've installed Mcafee on any Win 7 system, it automatically offers to disable Windows defender. I understand Win 10 is supposed to be engineered to make Defender less obtrusive and less conflicting, but my metaphor on this is that 2 Marine drill sergeants barking differing orders at full blast simultaneously to one soldier is probably too much to handle for the one poor guy. In scanning a few more articles on this question, I am seeing some cases where the 2 programs have operated OK together, but a majority where they haven't. So based on the numbers pro and con regarding mixing them, and on just the nature of the beast itself, I'm going to avoid trying to be a pioneer on this one. All that said, I have had very good results with Mcafee and Malwarebytes operating together, as MWB seems to fill the gap of what Mcafee doesn't cover with respect to Malware. I've seen MWB identify and remove Ransomware / Lockie etc. where Mcafee never even detected it.
Hope the above articles are of use.
Cheers,
jkirman
Sure, having two AV products scan for virii is not recommended. However, it might be possible that you can still use defender's folder protection alongside the AV software of your choice as it is a modular scanner, I checked that, and it does work (just did a quick test, though).
ASKER
McKnife,
If you could briefly summarize, what type of protection did you configure for Defender and test per your comment above? I.e. are you able to have Defender block:
- certain programs from any kind of writing to disk
- certain file types from being written to disk e.g. *.CRY
As I haven't used Defender yet I'm trying to get a feel for how to best use it and what it's really capable of doing.
Also please explain what you're referring to when you say that it's a modular scanner. Are you saying that you can disable the antivirus scanning features and only have it do file / application blocking types of activity?
Thanks.
If you could briefly summarize, what type of protection did you configure for Defender and test per your comment above? I.e. are you able to have Defender block:
- certain programs from any kind of writing to disk
- certain file types from being written to disk e.g. *.CRY
As I haven't used Defender yet I'm trying to get a feel for how to best use it and what it's really capable of doing.
Also please explain what you're referring to when you say that it's a modular scanner. Are you saying that you can disable the antivirus scanning features and only have it do file / application blocking types of activity?
Thanks.
Yes, you can block certain programs from writing to certain folders (both configurable).
No, you cannot block the creation of certain file types on a client OS. That is a function of file server resource manager which is a server role.
"Are you saying that you can disable the antivirus scanning features and only have it do file / application blocking types of activity?" - exactly. I'll upload a screenshot:
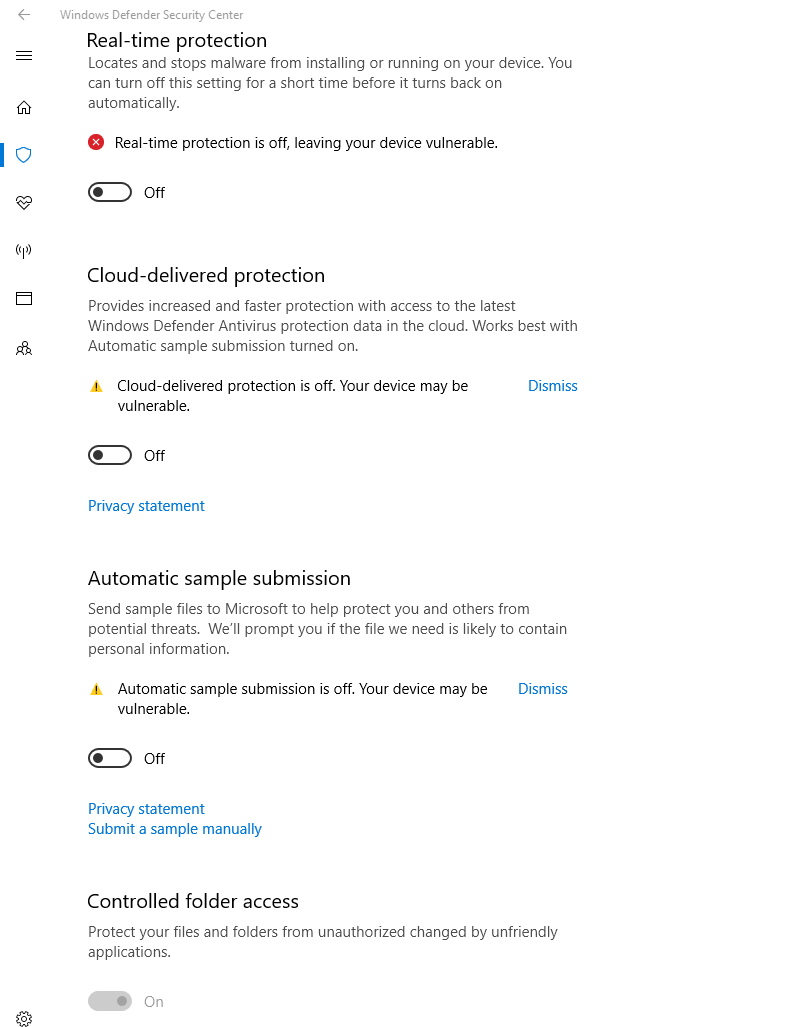
No, you cannot block the creation of certain file types on a client OS. That is a function of file server resource manager which is a server role.
"Are you saying that you can disable the antivirus scanning features and only have it do file / application blocking types of activity?" - exactly. I'll upload a screenshot:
ASKER
McKnife,
Thanks for the full details and screenshots on this. They have provided me with a good understanding of how to use Windows Defender in the modular sense you were describing and will test it out on my system with real-time protection disabled in tandem with McAfee active.
Regards,
jkirman
Thanks for the full details and screenshots on this. They have provided me with a good understanding of how to use Windows Defender in the modular sense you were describing and will test it out on my system with real-time protection disabled in tandem with McAfee active.
Regards,
jkirman
Fine. Please share your experience with it some day here.
New in version v1709.