Help with requiring Network Level Authentication for RDP
Hello Experts,
We are working on remediating some security vulnerabilities. One of the low hanging fruit that I thought I would remediate is the requirement to allow RDP connections from computers running Remote Desktop with Network Level Authentication. Below is a screenshot from one of our workstations showing the current setting:
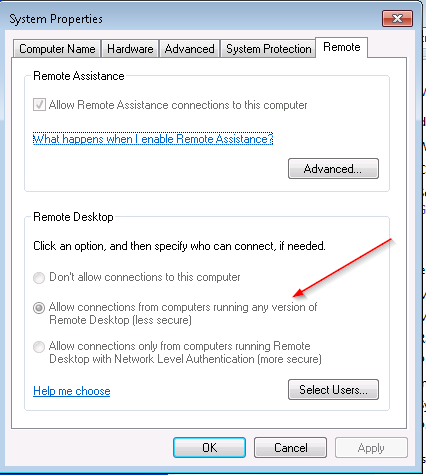
As you can see, we currently allow connections from any version of Remote Desktop.
The setting to require Network Level Authentication had been configured in our default domain policy. It was set to “disabled”. I have changed the setting to “enabled” and applied the change.
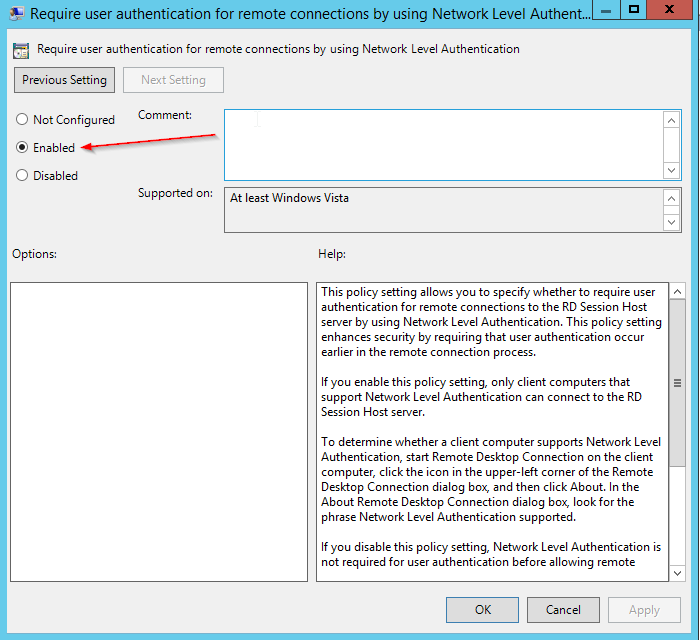
I have saved the GPO and let domain replication take place. When I do a gpupate /force /sync and restart the RDP settings are the same as they were in the first screenshot. What am I missing here?
Thanks in advanced.
Nick
We are working on remediating some security vulnerabilities. One of the low hanging fruit that I thought I would remediate is the requirement to allow RDP connections from computers running Remote Desktop with Network Level Authentication. Below is a screenshot from one of our workstations showing the current setting:

As you can see, we currently allow connections from any version of Remote Desktop.
The setting to require Network Level Authentication had been configured in our default domain policy. It was set to “disabled”. I have changed the setting to “enabled” and applied the change.

I have saved the GPO and let domain replication take place. When I do a gpupate /force /sync and restart the RDP settings are the same as they were in the first screenshot. What am I missing here?
Thanks in advanced.
Nick
Sometimes it takes a little time for the GPO update to hit all of the PCs. Other times, you might need to restart the workstations (or at least log out of them).
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
As a complete aside, I recommend never editing the default domain policy. It is best to create new policies and link them at the domain level instead.
As per the above recommendation, perhaps place this setting it its own policy would be a good start. Then ensure that the policy is deployed to containers with computers with the appropriate security.
Perform a gpresult /r and analyse the results to ensure the policy applied.
Alternately you could so a rsop.msc on the target machine and navigate to the specific NLA setting to ensure it is being set.
Perform a gpresult /r and analyse the results to ensure the policy applied.
Alternately you could so a rsop.msc on the target machine and navigate to the specific NLA setting to ensure it is being set.
ASKER
Good point about not using the default domain policy. I will have to start backing settings out and setting up their own GPOs.