Domain Admin unable to access NTFS Drive
I have a Windows Server 2016 member server that has a C: and a F: drive.
As Part of our standard file server build we remove all permissions from the root of the F: drive except for:
SYSTEM (Full Control)
Administrators (Full Control)
I've created a new domain user 'jakeadmin' and granted it membership of the Domain Admins group.
Domain Admins is a member of the member server's local Administrators group.
When I logon (via RDP) to the member server FILESERVER-01 as the domain user 'jakeadmin' this user cannot access the F: drive. I then tried adding the Domain Admins group with full control to the root of the F: drive but my 'jakeadmin' user still cannot access the F: drive:
If I logon to Fileserver-01 as a local machine administrator I have no trouble accessing the F: drive at all.
Why can't I browse my F: drive, even if I'm in the Administrators group?
I don't see turning off UAC as a solution - It's a terrible idea..
FYI: Effective Permissions below: (As you can see, everything is OK)
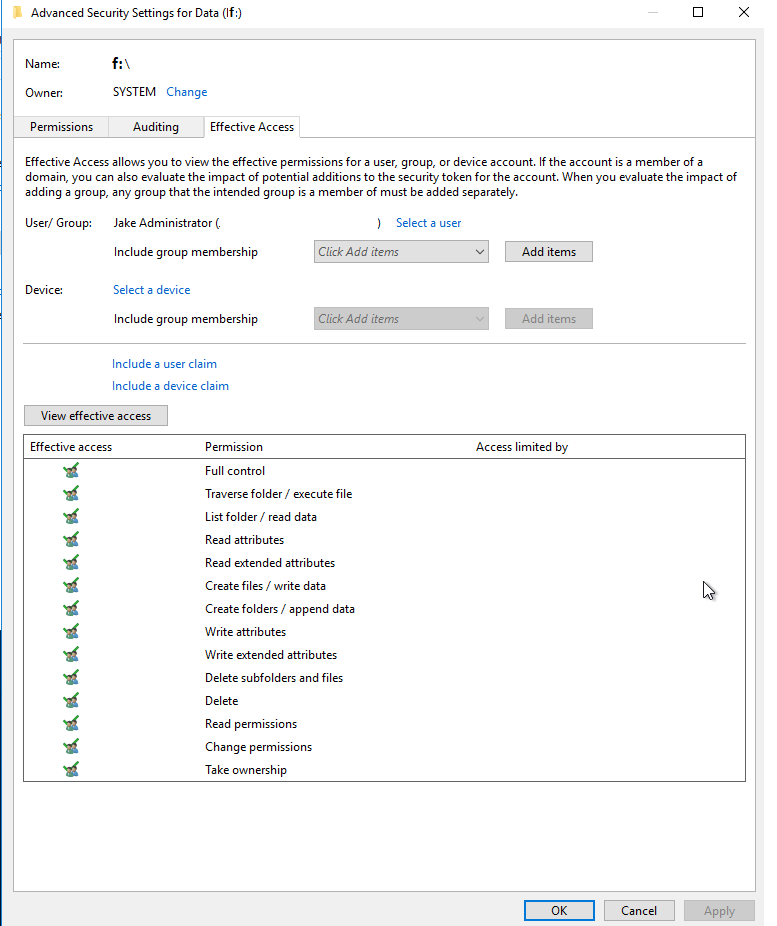
As Part of our standard file server build we remove all permissions from the root of the F: drive except for:
SYSTEM (Full Control)
Administrators (Full Control)
I've created a new domain user 'jakeadmin' and granted it membership of the Domain Admins group.
Domain Admins is a member of the member server's local Administrators group.
When I logon (via RDP) to the member server FILESERVER-01 as the domain user 'jakeadmin' this user cannot access the F: drive. I then tried adding the Domain Admins group with full control to the root of the F: drive but my 'jakeadmin' user still cannot access the F: drive:

If I logon to Fileserver-01 as a local machine administrator I have no trouble accessing the F: drive at all.
Why can't I browse my F: drive, even if I'm in the Administrators group?
I don't see turning off UAC as a solution - It's a terrible idea..
FYI: Effective Permissions below: (As you can see, everything is OK)

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
It was the same since UAC came up and this behavior is normal. If it worked on 2012 then either you used the built-in account "administrator", for which UAC is non-effective or UAC was even off. The registry editing is the best way, else, you will have to use a different explorer like total commander which can be run as administrator by default, or you will need to work with the account "administrator".
ASKER
So if I was to access the server with the built in domain admin account DOMAIN\Administrator I would be able to see the drive?
If that is the case, would be be best practice to create a new group called Data Managers and assign the domain admin group to that? (Or individual members?)
If that is the case, would be be best practice to create a new group called Data Managers and assign the domain admin group to that? (Or individual members?)
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
are you sure jack is indeed an administrator on that server, just in case, can you try to have jack setting up a dummy account or browsing the security event log ?
Author abandoned. Known issue and solution.
ASKER
I have deployed Windows server 2012 file servers in the past and configured them the same yet I am able to browse the drive letter in question.. I'm reluctant to changing registry entries and accessing explorer using the 'Run as' mechanism ..
all administrators should be able to access all aspects of the file server.
Really can't get my head around this one..
Thanks again