New Exchange server 2013 not allowing Outlook to connect
I have been in this business now for 15 years. I have admin'd multiple Exchange servers over the years but I have never set one up for production from scratch. This makes me a semi-noob. I have been fighting an issue for 2 weeks now and need help!
A new Exchange 2013 installation on a dedicated Microsoft Server 2012. I have purchased and attached a registered SSL cert for the mail server. Exchange itself is running fine. I have created multiple email boxes for users and email works perfectly. Each user can log in to OWA and the mail works as it should. They can all send and receive with no problems or delays. This holds true from inside OR outside the office.
I am not able to connect Outlook to any mailbox though.
When using Microsoft Remote Connectivity Analyzer, I get mixed results each time I run the various parts.
When I run Exchange Activesync Autodiscover, I get Connectivity Test Successful with Warnings.
When I run Exchange Activesync, I get Connectivity Test Successful with Warnings.
When I run Outlook Autodiscover, I get Connectivity Test Successful with Warnings.
When I run Outlook Connectivity, I get
"Certificate name validation failed.
Additional Details
Host name mail1.domain.com doesn't match any name found on the server certificate CN=mail.domain.com, OU=PositiveSSL Multi-Domain, OU=Domain Control Validated.
Elapsed Time: 0 ms."
I have a multi domain cert and 3 domains listed so far: domain.com, mail.domain.com, and autodiscover.domain.com. I am not sure if this really is a cert issue, or if there is something I missed in the install.
If I ignore all of this, and try to configure Outlook, after putting in the information asked during setup, Outlook appears to take 3 steps:
1. Establish network connection
2. Searching for "mailbox" settings
3. Logging on to the mail server.
The first two steps work fine and I get the green checkmark. The third step fails however and throws the error "The action cannot be completed. The connection to Microsoft Exchange is unavailable. Outlook must be online to connected to complete this action."
I get the same error no matter in the office or out.
Can anyone help? My head hurts from pounding it against the desk!
A new Exchange 2013 installation on a dedicated Microsoft Server 2012. I have purchased and attached a registered SSL cert for the mail server. Exchange itself is running fine. I have created multiple email boxes for users and email works perfectly. Each user can log in to OWA and the mail works as it should. They can all send and receive with no problems or delays. This holds true from inside OR outside the office.
I am not able to connect Outlook to any mailbox though.
When using Microsoft Remote Connectivity Analyzer, I get mixed results each time I run the various parts.
When I run Exchange Activesync Autodiscover, I get Connectivity Test Successful with Warnings.
When I run Exchange Activesync, I get Connectivity Test Successful with Warnings.
When I run Outlook Autodiscover, I get Connectivity Test Successful with Warnings.
When I run Outlook Connectivity, I get
"Certificate name validation failed.
Additional Details
Host name mail1.domain.com doesn't match any name found on the server certificate CN=mail.domain.com, OU=PositiveSSL Multi-Domain, OU=Domain Control Validated.
Elapsed Time: 0 ms."
I have a multi domain cert and 3 domains listed so far: domain.com, mail.domain.com, and autodiscover.domain.com. I am not sure if this really is a cert issue, or if there is something I missed in the install.
If I ignore all of this, and try to configure Outlook, after putting in the information asked during setup, Outlook appears to take 3 steps:
1. Establish network connection
2. Searching for "mailbox" settings
3. Logging on to the mail server.
The first two steps work fine and I get the green checkmark. The third step fails however and throws the error "The action cannot be completed. The connection to Microsoft Exchange is unavailable. Outlook must be online to connected to complete this action."
I get the same error no matter in the office or out.
Can anyone help? My head hurts from pounding it against the desk!
OK,, few steps.
Open IIS Admin
Make sure that autodiscover.domain.com is bind to port 443 and certificate in IIS
Make sure that email.domain.com is bind to port 443 and certificate in IIS
Run Exchange Powershell
Restart server or, IIS service and Transport service
Make sure there is A record for your autodiscover.domain.com in local and external DNS, for local DNS should point to internal emailserver IP.
Open IIS Admin
Make sure that autodiscover.domain.com is bind to port 443 and certificate in IIS
Make sure that email.domain.com is bind to port 443 and certificate in IIS
Run Exchange Powershell
Get-ClientAccessServer | Set-ClientAccessServer –AutoDiscoverServiceInternalUri https://autodiscover.company.com/autodiscover/autodiscover.xmlRestart server or, IIS service and Transport service
Make sure there is A record for your autodiscover.domain.com in local and external DNS, for local DNS should point to internal emailserver IP.
ASKER
I do not do much with Powershell so I didn't change anything before running the script. The results were almost promising I think.
For easy server info mail1.internal.local is internal server inside domain. mail.domain.com is external name...
Source: says I am running Exchange 2007 with a release date but it I know I am running Exchange 2013 so that is the first thing wrong.
Getting Client Access Information
AutodiscoverServiceInterna
Getting web services Info
InternalUrl : https://mail.domain.com/ews/exchange.asmx
ExternalUrl is the same which is correct
Geting Outlook Web Access OWA Info
InternalUrl : https://mail.domain.com/owa
ExternalUrl is the same
Getting Exchange Control Panel ECP Info
InternalUrl : https://owa.domain.com/ecp
ExternalUrl is the same. Not sure if it works because I usually connect using https://mail.domain.com/ecp and it works fine
Getting MAPI Info
InternalUrl : https://mail1.internal.local/mapi
ExternalUrl : (is blank)
Getting Powershell Virtual Directory
InternalUrl : https://main.domain.com/powershell
ExternalUrl is the same
For easy server info mail1.internal.local is internal server inside domain. mail.domain.com is external name...
Source: says I am running Exchange 2007 with a release date but it I know I am running Exchange 2013 so that is the first thing wrong.
Getting Client Access Information
AutodiscoverServiceInterna
Getting web services Info
InternalUrl : https://mail.domain.com/ews/exchange.asmx
ExternalUrl is the same which is correct
Geting Outlook Web Access OWA Info
InternalUrl : https://mail.domain.com/owa
ExternalUrl is the same
Getting Exchange Control Panel ECP Info
InternalUrl : https://owa.domain.com/ecp
ExternalUrl is the same. Not sure if it works because I usually connect using https://mail.domain.com/ecp and it works fine
Getting MAPI Info
InternalUrl : https://mail1.internal.local/mapi
ExternalUrl : (is blank)
Getting Powershell Virtual Directory
InternalUrl : https://main.domain.com/powershell
ExternalUrl is the same
Make sure you have external domain forward zone in your internal DNS and autodiscover.externaldomai
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Well the source of that is the web page on the technet
https://technet.microsoft.com/en-us/library/hh135098%28v=exchg.150%29.aspx?f=255&MSPPError=-2147217396
I really doubt it is wrong.
I'd do is to set all the internals and externals to the mail.domain.com
Create in the internal dns the zone "domain.com" if it doesn't exists and create 4 records:;
A to internal mail.domain.com,
CNAME to internal mail.domain.com
A to www => web page IP (type A)
A "empty dns record" to the same ip (domain.com).
And set up all the internals and externals url to mail.domain.com
script.ps1 -set -urlpath "https://mail.domain.com"
Make sure that your certificate counts with mail.domain.com and autodiscover.domain.com
https://technet.microsoft.com/en-us/library/hh135098%28v=exchg.150%29.aspx?f=255&MSPPError=-2147217396
I really doubt it is wrong.
I'd do is to set all the internals and externals to the mail.domain.com
Create in the internal dns the zone "domain.com" if it doesn't exists and create 4 records:;
A to internal mail.domain.com,
CNAME to internal mail.domain.com
A to www => web page IP (type A)
A "empty dns record" to the same ip (domain.com).
And set up all the internals and externals url to mail.domain.com
script.ps1 -set -urlpath "https://mail.domain.com"
Make sure that your certificate counts with mail.domain.com and autodiscover.domain.com
ASKER
So the default website bindings look like this
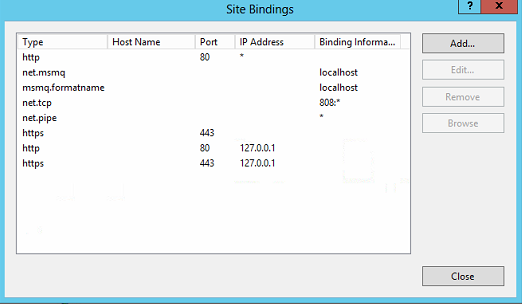
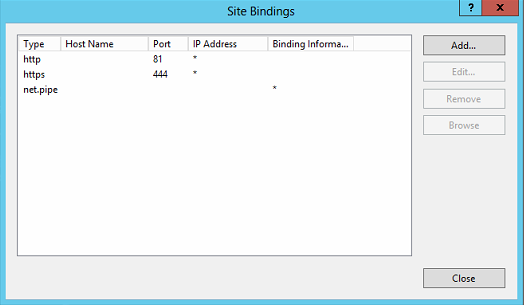
The Exchange backend bindings are
So you are saying I need to add the missing 443 bindings similar to what you are showing in your images?
The way I setup DNS was to add a new Forward lookup zone. I named it domain.com. In the records, I added 2 A records; 1 for autodiscover and the other for mail and pointed them both to the internal IP of the server.

The Exchange backend bindings are

So you are saying I need to add the missing 443 bindings similar to what you are showing in your images?
The way I setup DNS was to add a new Forward lookup zone. I named it domain.com. In the records, I added 2 A records; 1 for autodiscover and the other for mail and pointed them both to the internal IP of the server.
Let's see the existing setup please: (mask all the real info, replace with domain.com, paste results as code)
Get-OabVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Get-WebServicesVirtualDirectory | fl server, Name,ExternalURL, InternalURL, *auth*
Get-EcpVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Get-ActiveSyncVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Get-OutlookAnywhere | fl server, Name, *hostname*, *auth*
Get-OwaVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Get-ClientAccessService | fl Name,OutlookAnywhereEnabled, AutodiscoverServiceInternalUri
Get-ExchangeCertificate | fl FriendlyName, Subject, CertificateDomains, Thumbprint, Services, Issuer, *not*
Get-MapiVirtualDirectory | fl server, Name,ExternalURL,InternalURL, *auth*
Get-OrganizationConfig | fl *mapi*
Get-ExchangeServer | fl *version*ASKER
>Get-OabVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Server : MAIL1
Name : OAB (Default Web Site)
ExternalUrl : https://mail.domain.com/OAB
InternalUrl : https://mail.domian.com/OAB
BasicAuthentication : False
WindowsAuthentication : True
OAuthAuthentication : True
InternalAuthenticationMethods : {WindowsIntegrated, OAuth}
ExternalAuthenticationMethods : {WindowsIntegrated, OAuth}
>Get-WebServicesVirtualDirectory | fl server, Name,ExternalURL, InternalURL, *auth*
Server : MAIL1
Name : EWS (Default Web Site)
ExternalUrl : https://mail.domain.com/ews/exchange.asmx
InternalUrl : https://mail.domain.com/ews/exchange.asmx
CertificateAuthentication :
InternalAuthenticationMethods : {Ntlm, WindowsIntegrated, WSSecurity, OAuth}
ExternalAuthenticationMethods : {Ntlm, WindowsIntegrated, WSSecurity, OAuth}
LiveIdNegotiateAuthentication :
WSSecurityAuthentication : True
LiveIdBasicAuthentication : False
BasicAuthentication : False
DigestAuthentication : False
WindowsAuthentication : True
OAuthAuthentication : True
AdfsAuthentication : False
>Get-EcpVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Server : MAIL1
Name : ecp (Default Web Site)
ExternalUrl : https://owa.domain.com/ecp
InternalUrl : https://owa.domain.com/ecp
InternalAuthenticationMethods : {Basic, Fba}
BasicAuthentication : True
WindowsAuthentication : False
DigestAuthentication : False
FormsAuthentication : True
LiveIdAuthentication : False
AdfsAuthentication : False
OAuthAuthentication : False
ExternalAuthenticationMethods : {Fba}
>Get-ActiveSyncVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Server : MAIL1
Name : Microsoft-Server-ActiveSync (Default Web Site)
ExternalUrl : https://mail.domain.com/Microsoft-Server-ActiveSync
InternalUrl : https://mail.domain.com/Microsoft-Server-ActiveSync
MobileClientCertificateAuthorityURL :
BasicAuthEnabled : True
WindowsAuthEnabled : False
ClientCertAuth : Ignore
InternalAuthenticationMethods : {}
ExternalAuthenticationMethods : {}
>Get-OutlookAnywhere | fl server, Name, *hostname*, *auth*
Server : MAIL1
Name : Rpc (Default Web Site)
ExternalHostname :
InternalHostname : mail1.domain.com
ExternalClientAuthenticationMethod : Negotiate
InternalClientAuthenticationMethod : Ntlm
IISAuthenticationMethods : {Basic, Ntlm, Negotiate}
>Get-OwaVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
Server : MAIL1
Name : owa (Default Web Site)
ExternalUrl : https://mail.domain.com/owa
InternalUrl : https://mail.domain.com/owa
ClientAuthCleanupLevel : High
InternalAuthenticationMethods : {Basic, Fba}
BasicAuthentication : True
WindowsAuthentication : False
DigestAuthentication : False
FormsAuthentication : True
LiveIdAuthentication : False
AdfsAuthentication : False
OAuthAuthentication : False
ExternalAuthenticationMethods : {Fba}
>Get-ClientAccessService | fl Name,OutlookAnywhereEnabled, AutodiscoverServiceInternalUri
Get-ClientAccessService : The term 'Get-ClientAccessService' is not recognized as the name of a cmdlet, function,
script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is
correct and try again.
At line:1 char:1
+ Get-ClientAccessService | fl Name,OutlookAnywhereEnabled, AutodiscoverServiceInt ...
+ ~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (Get-ClientAccessService:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
>Get-ExchangeCertificate | fl FriendlyName, Subject, CertificateDomains, Thumbprint, Services, Issuer, *not*
FriendlyName : MDC2
Subject : CN=mail.domain.com, OU=PositiveSSL Multi-Domain, OU=Domain Control Validated
CertificateDomains : {mail.domain.com, AutoDiscover.domain.com, domain.com}
Thumbprint : 9D2A738EFC47E0E46F0097E5D513EF6F0CAAAF80
Services : IMAP, POP, IIS, SMTP
Issuer : CN=COMODO RSA Domain Validation Secure Server CA, O=COMODO CA Limited, L=Salford, S=Greater
Manchester, C=GB
NotAfter : 11/20/2020 6:59:59 PM
NotBefore : 11/30/2017 7:00:00 PM
FriendlyName : Microsoft Exchange Server Auth Certificate
Subject : CN=Microsoft Exchange Server Auth Certificate
CertificateDomains : {}
Thumbprint : 2348C3313A4C3DECE012F37F44F6CE60C164CCCC
Services : SMTP
Issuer : CN=Microsoft Exchange Server Auth Certificate
NotAfter : 9/18/2022 7:32:00 PM
NotBefore : 10/14/2017 7:32:00 PM
FriendlyName : Microsoft Exchange
Subject : CN=MAIL1
CertificateDomains : {MAIL1, MAIL1.internal.local}
Thumbprint : 9E099202960CE740910675C2454F1DB59D1AAFB9
Services : IIS, SMTP
Issuer : CN=MAIL1
NotAfter : 10/14/2022 7:30:32 PM
NotBefore : 10/14/2017 7:30:32 PM
FriendlyName : WMSVC
Subject : CN=WMSvc-MAIL1
CertificateDomains : {WMSvc-MAIL1}
Thumbprint : 26526325AEDBF42A77A8B926A924B92B8267D7D3
Services : None
Issuer : CN=WMSvc-MAIL1
NotAfter : 10/12/2027 6:15:08 PM
NotBefore : 10/14/2017 6:15:08 PM
>Get-MapiVirtualDirectory | fl server, Name,ExternalURL,InternalURL, *auth*
Server : MAIL1
Name : mapi (Default Web Site)
ExternalUrl :
InternalUrl : https://mail1.internal.local/mapi
IISAuthenticationMethods : {Ntlm, OAuth, Negotiate}
InternalAuthenticationMethods : {Ntlm, OAuth, Negotiate}
ExternalAuthenticationMethods : {Ntlm, OAuth, Negotiate}
>Get-OrganizationConfig | fl *mapi*
MapiHttpEnabled : False
>Get-ExchangeServer | fl *version*
AdminDisplayVersion : Version 15.0 (Build 1347.2)
ExchangeVersion : 0.1 (8.0.535.0)SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Out of the 4 lines of code, the 1st failed but the last 3 were fine. Here is what was returned:
>Set-OutlookAnywhere -Identity "Rpc (Default Web Site)" -ExternalHostname mail.domain.com -InternalHostname mail.domain.com -ExternalClientAuthenticationMethod Negotiate -InternalClientAuthenticationMe
thod NTLM -IISAuthenticationMethods Basic,NTLM,Negotiate
To configure the Outlook Anywhere feature with an ExternalHostname you must also specify the ExternalClientsRequireSsl parameter to indicate whether SSL is required.
+ CategoryInfo : InvalidArgument: (MAIL1\Rpc (Default Web Site):ADObjectId) [Set-OutlookAnywhere], ArgumentException
+ FullyQualifiedErrorId : [Server=MAIL1,RequestId=73e6501c-d315-40e3-a353-b38069cded69,TimeStamp=12/2/2017 8:23:21 AM] [FailureCategory=Cmdlet-ArgumentException] 9C5AAB75,Microsoft.Exchange.Management.SystemConfigurationTasks.SetRpcHttp
+ PSComputerName : mail1.internal.local
Here I can see
Get-EcpVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
ExternalUrl : https://owa.domain.com/ecp
InternalUrl : https://owa.domain.com/ecp
but it should be
ExternalUrl : https://mail.domain.com/ecp
InternalUrl : https://mail.domain.com/ecp
also
Get-MapiVirtualDirectory | fl server, Name,ExternalURL,InternalU
Server : MAIL1
Name : mapi (Default Web Site)
ExternalUrl :
InternalUrl : https://mail1.internal.local/mapi
Your External Url is missing !!!
Get-EcpVirtualDirectory | fl server, Name, ExternalURL, InternalURL, *auth*
ExternalUrl : https://owa.domain.com/ecp
InternalUrl : https://owa.domain.com/ecp
but it should be
ExternalUrl : https://mail.domain.com/ecp
InternalUrl : https://mail.domain.com/ecp
also
Get-MapiVirtualDirectory | fl server, Name,ExternalURL,InternalU
Server : MAIL1
Name : mapi (Default Web Site)
ExternalUrl :
InternalUrl : https://mail1.internal.local/mapi
Your External Url is missing !!!
And bindings is missing for internal and external addresses in you IIS.
Please take a moment and compare to mine, and make corrections
Please take a moment and compare to mine, and make corrections
Yeah, I thought it might not work, try this:
Set-OutlookAnywhere -Identity "Rpc (Default Web Site)" -ExternalHostname mail.domain.com -InternalHostname mail.domain.com -ExternalClientAuthenticationMethod NTLM -InternalClientAuthenticationMe
thod NTLM -IISAuthenticationMethods Basic,NTLM,NegotiateSet-MapiVirtualDirectory -Identity "mapi (Default Web Site)" -InternalUrl https://mail.domain.com/mapi -IISAuthenticationMethods Ntlm,Negotiate,OAuthASKER
So I ran the 2 lines of code Ronin said and the first one returned error messages.
I also updated my default website bindings. Here is what I made them
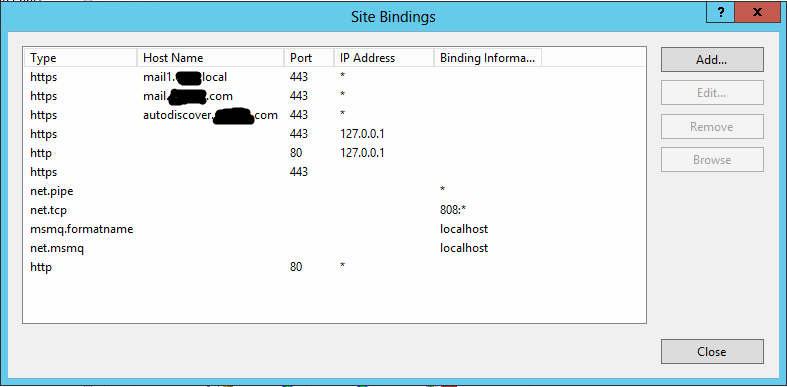
To see if anything has helped up until now, I tried to connect Outlook to this Exchange server. Here is the error I get:
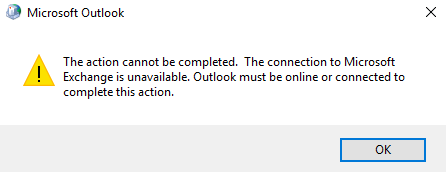
To configure the Outlook Anywhere feature with an ExternalHostname you must also specify the ExternalClientsRequireSsl parameter to indicate whether SSL is required.
+ CategoryInfo : InvalidArgument: (MAIL1\Rpc (Default Web Site):ADObjectId) [Set-OutlookAnywhere], ArgumentException
+ FullyQualifiedErrorId : [Server=MAIL1,RequestId=e3a92d75-0847-4ede-b60d-fa06daa4c92e,TimeStamp=12/5/2017 11:01:09 PM] [FailureCategory=Cmdlet-ArgumentException] 9E71919F,Microsoft.Exchange.Management.SystemConfigurationTasks.SetRpcHttp
+ PSComputerName : mail1.cpm.localI also updated my default website bindings. Here is what I made them

To see if anything has helped up until now, I tried to connect Outlook to this Exchange server. Here is the error I get:

Ok, here's an updated command:
You don't need to host names. This is how the ideal config should look like:
The cert defined on the 443 port, for the 127.0.0.1 and *. That is it.
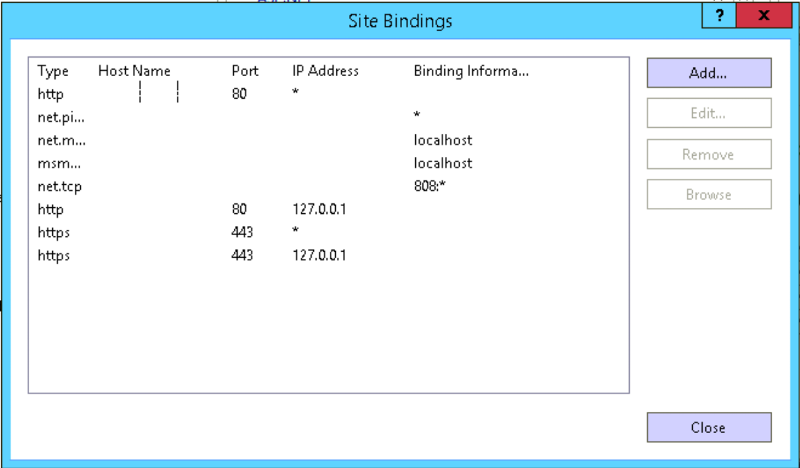
Set-OutlookAnywhere -Identity "Rpc (Default Web Site)" -ExternalHostname mail.domain.com -InternalHostname mail.domain.com -ExternalClientAuthenticationMethod NTLM -ExternalClientsRequireSsl $true -InternalClientAuthenticationMethod NTLM -IISAuthenticationMethods Basic,NTLM,NegotiateYou don't need to host names. This is how the ideal config should look like:
The cert defined on the 443 port, for the 127.0.0.1 and *. That is it.

ASKER
I restarted the mail server and now outlook can connect. I am not sure which part fixed it, but thank you guys so much for your help!
Run this script with the option "( -get)" to get all the internal and externals URLs that uses your environment
https://gallery.technet.microsoft.com/office/Script-to-configure-the-5a58558b
if you see that internal AND external address needs set up or have something like "mail.domain.local" that won't match your "mail.domain.com" so the certificate will bring errors.
Just reset using the same script with the option (-set -urlpath "https://mail.yourdomain.com") and it will update all the internal registry. Also, make sure that internally and externally the "mail.yourdomain.com" is accessible. Let me know if it worked for your or if you have anything else going on
jose