Create a LAN to LAN VPN Juniper SSG-140
I am using an SSG-140 Firewall at our rack in our data centre. Behind the firewall are several VMWare host servers which house a bunch of VP Servers, one of which hosts several 3CX VOIP PBXes for our customers.
I'm wanting to setup VPN tunnels for each customer so that we can do away with the SBC that 3CX demands we use if remote.
Can someone tell me how to set up a VPN connection to the firewall for our "test" customer (me!) so I can check it works? I'm using the WEB interface on the Juniper as I'm not too clued up with the CLI at this point on the unit.
The VPN tunnel should be ALWAYS UP, LAN to LAN and STATIC IP to STATIC IP.
Any help gratefully accepted.
Cheers
Chris
I'm wanting to setup VPN tunnels for each customer so that we can do away with the SBC that 3CX demands we use if remote.
Can someone tell me how to set up a VPN connection to the firewall for our "test" customer (me!) so I can check it works? I'm using the WEB interface on the Juniper as I'm not too clued up with the CLI at this point on the unit.
The VPN tunnel should be ALWAYS UP, LAN to LAN and STATIC IP to STATIC IP.
Any help gratefully accepted.
Cheers
Chris
ASKER
Hi Sanga
Thanks as always for coming to the rescue. I'll have a look at that KB article sometime this afternoon and will let you know how I get on. I have to be extremely careful as the firewall is "live" and if I mess up I could have 43 servers suddenly go missing and a lynch party after me! :)
Cheers
Chris
Thanks as always for coming to the rescue. I'll have a look at that KB article sometime this afternoon and will let you know how I get on. I have to be extremely careful as the firewall is "live" and if I mess up I could have 43 servers suddenly go missing and a lynch party after me! :)
Cheers
Chris
ASKER
Ah! A question already - is "route-based" better than "policy-based"? I want the connection(s) to all be permanently up and with our "little" router firewalls I think we usually set up route-based but could be wrong. What do you think, Sanga?
Cheers
Chris
Cheers
Chris
ASKER
Hi Sanga
Does this help unravel the question as to how we are set up? (see embedded screenshot)
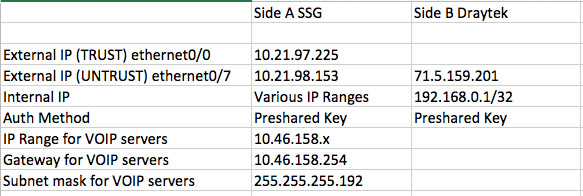
The SSG appears to have two interfaces (one trust and one untrust).
The Internal IPs on the SSG side are static IPs and we run 43 servers of various types on about 4 IP ranges (legacy setup)
VOIP IP range - each IP will be a VOIP VPS running Debian. For the test I'll be using a server with IP 10.46.158.223
On the remote side of the equation will be a Draytek 2820n router
It's external IP address will be 71.5.159.201
Internal (NAT) IPs all 192.168.0.x with /32 netmask
I'm kind-of OK with setting up the Draytek but the Juniper setup is driving me nuts. The Firmware version of the Juniper is 6.1.0r3.0 (Firewall + VPN)
All the best
Chris
Does this help unravel the question as to how we are set up? (see embedded screenshot)

The SSG appears to have two interfaces (one trust and one untrust).
The Internal IPs on the SSG side are static IPs and we run 43 servers of various types on about 4 IP ranges (legacy setup)
VOIP IP range - each IP will be a VOIP VPS running Debian. For the test I'll be using a server with IP 10.46.158.223
On the remote side of the equation will be a Draytek 2820n router
It's external IP address will be 71.5.159.201
Internal (NAT) IPs all 192.168.0.x with /32 netmask
I'm kind-of OK with setting up the Draytek but the Juniper setup is driving me nuts. The Firmware version of the Juniper is 6.1.0r3.0 (Firewall + VPN)
All the best
Chris
For this situation, route based VPN would be more suitable than a policy based VPN.
From your setup, one thing that sticks out as strange is having an External IP in the TRUST Zone. If you have access to the command line. Can you post the results of the following commands:
get int
get route
This will display how the interfaces on the juniper are configured and how traffic is routed. We can then determine what steps to take next. ( you can also post screen shots of the interface table and route table from the webUI if you cant get to the CLI.
When building a route based VPN. on the Juniper side, you need the following.
VPN > Autokey Advanced > Gateway -> External interface IP on draytek, prehsared key, outgoing interface, security level
VPN > AutKey IKE > Gateway from above, security level, tunnel interface, vpn monitor.
THe instructions in the link are for Juniper <-> juniper VPN, but we can modify to connect to any device.
From your setup, one thing that sticks out as strange is having an External IP in the TRUST Zone. If you have access to the command line. Can you post the results of the following commands:
get int
get route
This will display how the interfaces on the juniper are configured and how traffic is routed. We can then determine what steps to take next. ( you can also post screen shots of the interface table and route table from the webUI if you cant get to the CLI.
When building a route based VPN. on the Juniper side, you need the following.
VPN > Autokey Advanced > Gateway -> External interface IP on draytek, prehsared key, outgoing interface, security level
VPN > AutKey IKE > Gateway from above, security level, tunnel interface, vpn monitor.
THe instructions in the link are for Juniper <-> juniper VPN, but we can modify to connect to any device.
ASKER
Hi Sanga
I've changed the initial IP numbers to protect the IP addresses of the various items of the network. If you'd like me to send you the actual I can do that with pleasure. Let me know and let me have an Email if you do?
All the best
Chris
JuniperRouteBased-3.jpg
JuniperRouteBased-4.jpg
I've changed the initial IP numbers to protect the IP addresses of the various items of the network. If you'd like me to send you the actual I can do that with pleasure. Let me know and let me have an Email if you do?
All the best
Chris
JuniperRouteBased-3.jpg
JuniperRouteBased-4.jpg
Hope you had a great holiday and are ready for the new year!!
I just went over the post again. And I think I see where your issue might be. Is tunnel.2 the Tunnel interface you created for the test? If so, It should be in the Trust zone. If you do not want it in trust zone, you should create a custom zone in the "Trust-VR". You can call it Voip-zone or something descriptive.
Here are the exact steps i follow when creating a route based VPN
1. custom zone: I create a simple custom zone called 'vpn-zone' and virtual router name = 'trust-vr'
2. tunnel interface: zone(vr) = 'vpn-zone (trust-vr)', unnumbered = checked, interface = eth0/0
3. Remote gateway: Give it a name, and enter remote public static IP.
> advanced: enter the Preshared Key, the outgoing interface (in your case eth0/7) and the security level.
*** This is critical. The phase 1 proposal must match the phase 1 at the remote device. I use standard if Juniper <-> juniper, but you may have to choose something different that matches the draytek offerings.
> for mode i choose Main(ID protection)
4. AutoKey IKE: Give it a name, and choose the predefined remote gateway from step 3.
> advanced: This is where you choose the phase2 proposal that matches the offerings from the remote device.
Bind to will be the new tunnel interface you created. And lastly I enable VPN monitor and rekey.
This will bring you to a completed VPN. If succesful you will be able to got to VPNs > monitor status and see that the VPN is up. Below is an example of my home VPN ssg connecting to my head office ssg
VPN Name SA ID Policy ID Peer Gateway IP Type SA Status Link
vpn-5@fac-office 0000000b -1/-1 x.80.x.242 AutoIKE Active Up
If you get to this point and all is working. the next step will be setting up routing and finally the security policy to allow the traffic.
5. Routing: Each remote LAN will need to have its own entry in the Destination rout table.So for your draytek you will need
IP Address/Netmask 192.168.0.0 / 24 * this will be 192.168.0.1 - 254, if you use 192.168.0.1/32 you will only be able to hit 1 ip
Next Hop = gateway
interface = tunnel.2
gateway IP = 192.168.0.1 (the lan IP of remote network)
Ofcourse on the draytek side you will also need route statements pointing back to your VOIP servers.
6. Security Policy: two will be needed if you want traffic both ways.
from ssg to draytek = from trust to vpn-zone
from draytek to ssg = from vpn-zone to trust
You can specify specific services and IP addresses that you want to allow using these policies when its time to lock them down.
I am sure you will have more questions, so please do not hesitate to post.
Thanks!
I just went over the post again. And I think I see where your issue might be. Is tunnel.2 the Tunnel interface you created for the test? If so, It should be in the Trust zone. If you do not want it in trust zone, you should create a custom zone in the "Trust-VR". You can call it Voip-zone or something descriptive.
Here are the exact steps i follow when creating a route based VPN
1. custom zone: I create a simple custom zone called 'vpn-zone' and virtual router name = 'trust-vr'
2. tunnel interface: zone(vr) = 'vpn-zone (trust-vr)', unnumbered = checked, interface = eth0/0
3. Remote gateway: Give it a name, and enter remote public static IP.
> advanced: enter the Preshared Key, the outgoing interface (in your case eth0/7) and the security level.
*** This is critical. The phase 1 proposal must match the phase 1 at the remote device. I use standard if Juniper <-> juniper, but you may have to choose something different that matches the draytek offerings.
> for mode i choose Main(ID protection)
4. AutoKey IKE: Give it a name, and choose the predefined remote gateway from step 3.
> advanced: This is where you choose the phase2 proposal that matches the offerings from the remote device.
Bind to will be the new tunnel interface you created. And lastly I enable VPN monitor and rekey.
This will bring you to a completed VPN. If succesful you will be able to got to VPNs > monitor status and see that the VPN is up. Below is an example of my home VPN ssg connecting to my head office ssg
VPN Name SA ID Policy ID Peer Gateway IP Type SA Status Link
vpn-5@fac-office 0000000b -1/-1 x.80.x.242 AutoIKE Active Up
If you get to this point and all is working. the next step will be setting up routing and finally the security policy to allow the traffic.
5. Routing: Each remote LAN will need to have its own entry in the Destination rout table.So for your draytek you will need
IP Address/Netmask 192.168.0.0 / 24 * this will be 192.168.0.1 - 254, if you use 192.168.0.1/32 you will only be able to hit 1 ip
Next Hop = gateway
interface = tunnel.2
gateway IP = 192.168.0.1 (the lan IP of remote network)
Ofcourse on the draytek side you will also need route statements pointing back to your VOIP servers.
6. Security Policy: two will be needed if you want traffic both ways.
from ssg to draytek = from trust to vpn-zone
from draytek to ssg = from vpn-zone to trust
You can specify specific services and IP addresses that you want to allow using these policies when its time to lock them down.
I am sure you will have more questions, so please do not hesitate to post.
Thanks!
ASKER
Hi Sanga - yes you're correct. It should have been in the "Trust" zone. I've changed that but now not sure how that affects your list of instructions. Could you have a look over them and change if needed. Apologies for the slip. I didn't realise that I hadn't created tunnel.2 in the Trust zone.
Many thanks
Chris
Many thanks
Chris
If you keep the tunnel in the trust zone instead of a custom zone, all you have to do is replace everywhere I have vpn-zone with trust zone.
The finally policy will also need to be from trust to trust since the Tunel and LAN interfaces are both in trust zone.
The finally policy will also need to be from trust to trust since the Tunel and LAN interfaces are both in trust zone.
ASKER
Hi Sanga - it gets worse! heh heh
I've set up as close as I can to what you've put above. The Draytek is just continuing to try and connect and the SSG is returning lots of moaning and groaning because I've not set it up right. Error messages in the SSG log are:
IKE 71.5.159.201 Phase 2 msg ID 2b5b7300: Negotiations have failed.
IKE 71.5.159.201 Phase 2 msg ID 2b5b7300: Responded to the peer's first message.
IKE 71.5.159.201 Phase 2: No policy exists for the proxy ID received: local ID (10.46.158.192/255.255.255
Rejected an IKE packet on ethernet0/7 from 71.5.159.201:500 to 10.21.98.153:500 with cookies a7fc27bd896f635d and 80bd294e402fe90c because The peer sent a proxy ID that did not match the one in the SA config.
This is looping again and again in the logs on the SSG.
It appears that the P1 is working but that the P2 is failing for some reason. Also, I'm not 100% sure what I should be putting into the Draytek in the networking section. I have the following:
My WAN IP
0.0.0.0
Remote Gateway IP
0.0.0.0
Remote Network IP
10.46.158.223 (I picked this IP basically because it's the IP of the VOIP PBX server in use)
Remote Network Mask
255.255.255.192 (this is the actual network mask of this segment)
Local Network IP
192.168.1.1 (This is the NAT network behind the Draytek)
Local Network Mask
255.255.255.0
I hate being so dumb but VPN between anything and our SSG has always been a large problem for me. Appreciate the help you're giving, Sanga.
All the best
Chris
I've set up as close as I can to what you've put above. The Draytek is just continuing to try and connect and the SSG is returning lots of moaning and groaning because I've not set it up right. Error messages in the SSG log are:
IKE 71.5.159.201 Phase 2 msg ID 2b5b7300: Negotiations have failed.
IKE 71.5.159.201 Phase 2 msg ID 2b5b7300: Responded to the peer's first message.
IKE 71.5.159.201 Phase 2: No policy exists for the proxy ID received: local ID (10.46.158.192/255.255.255
Rejected an IKE packet on ethernet0/7 from 71.5.159.201:500 to 10.21.98.153:500 with cookies a7fc27bd896f635d and 80bd294e402fe90c because The peer sent a proxy ID that did not match the one in the SA config.
This is looping again and again in the logs on the SSG.
It appears that the P1 is working but that the P2 is failing for some reason. Also, I'm not 100% sure what I should be putting into the Draytek in the networking section. I have the following:
My WAN IP
0.0.0.0
Remote Gateway IP
0.0.0.0
Remote Network IP
10.46.158.223 (I picked this IP basically because it's the IP of the VOIP PBX server in use)
Remote Network Mask
255.255.255.192 (this is the actual network mask of this segment)
Local Network IP
192.168.1.1 (This is the NAT network behind the Draytek)
Local Network Mask
255.255.255.0
I hate being so dumb but VPN between anything and our SSG has always been a large problem for me. Appreciate the help you're giving, Sanga.
All the best
Chris
VPN between anything and SSG is a large problem for everyone :D!!
Not to worry, you are very close. In the AUtoKey IKE in the row for your new entry. There is a link labled 'Proxy_ID'
If you click on that you can then setup the IP address of your Local network, and the IP address of the remote network. THe zone will be trust for both entries since your LAN and Tunnel interface are in the trust zone. The service should be set to 'ANY' for testing then locked down once its working.
As far as the draytek, The remote network IP should be either be the IP address remote LAN
Not to worry, you are very close. In the AUtoKey IKE in the row for your new entry. There is a link labled 'Proxy_ID'
If you click on that you can then setup the IP address of your Local network, and the IP address of the remote network. THe zone will be trust for both entries since your LAN and Tunnel interface are in the trust zone. The service should be set to 'ANY' for testing then locked down once its working.
As far as the draytek, The remote network IP should be either be the IP address remote LAN
ASKER
Hey Sanga
The local network is a segment with a /192 netmask. There are not many "free" IP addresses in the segment. This is where I'm getting confused. When we set up Draytek to Draytek it's fairly simple. In the network settings on the Draytek, these are my options:
My WAN IP
0.0.0.0
Remote Gateway IP
0.0.0.0
Remote Network IP
10.46.158.223 (I picked this IP basically because it's the IP of the VOIP PBX server in use)
Remote Network Mask
255.255.255.192 (this is the actual network mask of this segment)
Local Network IP
192.168.1.1 (This is the NAT network behind the Draytek)
Local Network Mask
255.255.255.0
What would you suggest I enter into the Proxy settings on the SSG and what would you enter into the Draytek (above) settings?
Cheers
Chris
The local network is a segment with a /192 netmask. There are not many "free" IP addresses in the segment. This is where I'm getting confused. When we set up Draytek to Draytek it's fairly simple. In the network settings on the Draytek, these are my options:
My WAN IP
0.0.0.0
Remote Gateway IP
0.0.0.0
Remote Network IP
10.46.158.223 (I picked this IP basically because it's the IP of the VOIP PBX server in use)
Remote Network Mask
255.255.255.192 (this is the actual network mask of this segment)
Local Network IP
192.168.1.1 (This is the NAT network behind the Draytek)
Local Network Mask
255.255.255.0
What would you suggest I enter into the Proxy settings on the SSG and what would you enter into the Draytek (above) settings?
Cheers
Chris
ASKER
Hi there - apologies for the long delay getting this resolved. I've had to purchase another Draytek router to see whether we are able to resolve the problem and also want to upgrade the firmware on the Juniper. Please keep this question open as the resolution will help others get this resolved.
ASKER
Hi Folks
Sincere apologies for the delays. We've had all kinds of issues including sickness in the office which has delayed everything. We should be able able to set up the next step so that Sanga can help advise and as soon as we have that in place, I'll post again.
Cheers
Chris
Sincere apologies for the delays. We've had all kinds of issues including sickness in the office which has delayed everything. We should be able able to set up the next step so that Sanga can help advise and as soon as we have that in place, I'll post again.
Cheers
Chris
ASKER
@Sanga - We are planning to get out to the Data Center this evening if possible and will restart the actions for this question. Apologies again for the delay.
Cheers
Chris
Cheers
Chris
sounds good. Keep me posted of your progress.
Thanks!
Thanks!
ASKER
Hey Sanga - still haven't had a chance to get to the data center. Will update you as soon as I get that opportunity. The woes of running your own business - no time to get out and do some of the stuff that so needs doing.
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
https://kb.juniper.net/InfoCenter/index?page=content&id=KB14330&actp=METADATA
If you get stuck at any part let us know and we'll get you unstuck.