Sniff ARP requests in c# or vb.net
I am working on an application where I need to pick up ARP requests.
My train of thought was to put the Network Adapter into promiscuous mode and process packets as they come in. As I've done this previously with syslog and netflow packets, I though it would be straightforward.... NOT!
A quick search finds example code to sniff promiscuously (and there's a few out there). They all seem to use the IP header to say whether the encapsulated is TCP or UDP. This lets you filter by IP address, port etc.
https://www.codeproject.co
An ARP packet doesn't have a destination IP address. It doesn't even have an IP header, it is just 60 bytes as per this link:
http://www.rhyshaden.com/a
My question is:
I don't know how to listen/filter for an arp packet.
If someone could just help me listen for and get the ARP requests, I can work with the packet data to get the information I want.
My train of thought was to put the Network Adapter into promiscuous mode and process packets as they come in. As I've done this previously with syslog and netflow packets, I though it would be straightforward.... NOT!
A quick search finds example code to sniff promiscuously (and there's a few out there). They all seem to use the IP header to say whether the encapsulated is TCP or UDP. This lets you filter by IP address, port etc.
https://www.codeproject.co
An ARP packet doesn't have a destination IP address. It doesn't even have an IP header, it is just 60 bytes as per this link:
http://www.rhyshaden.com/a
My question is:
I don't know how to listen/filter for an arp packet.
If someone could just help me listen for and get the ARP requests, I can work with the packet data to get the information I want.
ASKER
Thanks Predrag for the info. You links are a bit more detailed than the link I posted.
What I need to do though is to listen for arp requests and get the frame data.
I am writing an application to look for unauthorised hosts on my network.
If a new host shows up, to do ANY IP operation such as ping or to speak to a host on the internet, it will need to use ARP to discover the Hardware address of the host (or gateway) it is trying to talk to.
I want to capture these arp broadcasts to detect the machine.
So I need to sniff for Ethernet frames with a hardware type of 1 and a protocol type of 1.
I am able to sniff for IP frames, but I can't sniff for ARP requests as there is no IP header. This is where my knowledge gives way.
I would be very grateful, if someone could help me detect and/or get the payload of an ARP request.
What I need to do though is to listen for arp requests and get the frame data.
I am writing an application to look for unauthorised hosts on my network.
If a new host shows up, to do ANY IP operation such as ping or to speak to a host on the internet, it will need to use ARP to discover the Hardware address of the host (or gateway) it is trying to talk to.
I want to capture these arp broadcasts to detect the machine.
So I need to sniff for Ethernet frames with a hardware type of 1 and a protocol type of 1.
I am able to sniff for IP frames, but I can't sniff for ARP requests as there is no IP header. This is where my knowledge gives way.
I would be very grateful, if someone could help me detect and/or get the payload of an ARP request.
ASKER
Thanks IT_Sage
I really don't want to use third-party libraries, especially as win_PCAP is overkill for what I want.
The example shows how to put a network card into promiscuous mode and sniff IP Packets without using win_pcap:
https://www.codeproject.co
I'd like to use the built in .net classes such as system.net.socket if I could.
surely there must be a way to pick up the arp packets in .net?
I really don't want to use third-party libraries, especially as win_PCAP is overkill for what I want.
The example shows how to put a network card into promiscuous mode and sniff IP Packets without using win_pcap:
https://www.codeproject.co
I'd like to use the built in .net classes such as system.net.socket if I could.
surely there must be a way to pick up the arp packets in .net?
ASKER
I've looked into it further.
Windows sockets work on the IP layer.
ARP is supposed to be a layer 3 protocol, but windows sockets only give what is encapsulated by an IP header.
ARP does not have an IP header. So even though it is a layer 3 protocol, windows sockets are no good in this instance.
So I need to be sniffing at a lower layer
Windows sockets work on the IP layer.
ARP is supposed to be a layer 3 protocol, but windows sockets only give what is encapsulated by an IP header.
ARP does not have an IP header. So even though it is a layer 3 protocol, windows sockets are no good in this instance.
So I need to be sniffing at a lower layer
ARP is not really L3 protocol, that's why it is often referred as L2,5. ;)
It is resolving L3 addresses, but does not have L3 header... so ARP itself is not L3 protocol, but L2.
It is resolving L3 addresses, but does not have L3 header... so ARP itself is not L3 protocol, but L2.
Why invoke promiscuous mode?
ARP packets are either broadcast, or directed to the MAC address in question. Assuming you have a switch in place, as is the norm in 2017, packets that would be allowed only in promiscuous mode generally don't even reach the NIC, so it makes no real difference.
ARP packets are either broadcast, or directed to the MAC address in question. Assuming you have a switch in place, as is the norm in 2017, packets that would be allowed only in promiscuous mode generally don't even reach the NIC, so it makes no real difference.
ASKER
Hi Mal. Thanks for your input.
When a new host joins the network, to do anything, it must send an arp broadcast - These go to the broadcast address FF:FF:FF:FF:FF:FF and I should get them without requiring promiscuous mode.
Responses go directly to the MAC they are sent to, so on a switched network, I'd need a mirror/monitor port setting up on the switch and promiscuous mode setting on the NIC.
I can hear the next question coming... why do I want to sniff responses?
Listening for requests is good for detecting hosts on the LAN, but listening for responses will allow me to detect bad behaviour such as ARP poisoning attempts (multiple hosts saying they have a specific IP address)
I have several uses for this code, but I didn't put them in the question as I wanted to keep it simple - learn a bit more about networking, investigate protocols like HSRP and HRRP, detect hosts on the LAN, Detect bad behaviour on the LAN.
I intend to also extend it to listen for RARP requests and responses
To do this, I need a way to sniff the layer 2 frames and filter for arp/rarp which is really what the question is about.
When a new host joins the network, to do anything, it must send an arp broadcast - These go to the broadcast address FF:FF:FF:FF:FF:FF and I should get them without requiring promiscuous mode.
Responses go directly to the MAC they are sent to, so on a switched network, I'd need a mirror/monitor port setting up on the switch and promiscuous mode setting on the NIC.
I can hear the next question coming... why do I want to sniff responses?
Listening for requests is good for detecting hosts on the LAN, but listening for responses will allow me to detect bad behaviour such as ARP poisoning attempts (multiple hosts saying they have a specific IP address)
I have several uses for this code, but I didn't put them in the question as I wanted to keep it simple - learn a bit more about networking, investigate protocols like HSRP and HRRP, detect hosts on the LAN, Detect bad behaviour on the LAN.
I intend to also extend it to listen for RARP requests and responses
To do this, I need a way to sniff the layer 2 frames and filter for arp/rarp which is really what the question is about.
ASKER
Predrag, I would view things a little different to your comment. I guess it is more about the terminology used.
I would say it is a layer 3 protocol, acting at/for the IP layer, but using layer 2 packets to do this.
This highlights a vague understanding as to the subtleties of what the layers actually are. Is layer 3 for example referring to use and manipulation of IP or is it simply about the packets used to do this? Does every packet used in a layer 3 protocol require an IP header (or I guess IPX) or does it just have to be working on a layer 3 subject (getting the IP address from a MAC)?
I guess I need a concise description of what a layer actually stands for
I would say it is a layer 3 protocol, acting at/for the IP layer, but using layer 2 packets to do this.
This highlights a vague understanding as to the subtleties of what the layers actually are. Is layer 3 for example referring to use and manipulation of IP or is it simply about the packets used to do this? Does every packet used in a layer 3 protocol require an IP header (or I guess IPX) or does it just have to be working on a layer 3 subject (getting the IP address from a MAC)?
I guess I need a concise description of what a layer actually stands for
General, requirement for L3 protocol is that L3 header is present, so traffic can be routable. ARP is not routable since it does not have L3 header. ARP is protocol that is forwarded on L2 and provide information about L3.
ARP just has L2 encapsulation (L2 frame type 0x0806 define frame as ARP). It is broadcasted to all devices since destination is FFFF.FFFF.FFFF. Device that receives L2 frame will check if ARP message is address to it (check IP address inside of ARP message of target device against its own IP address). In Wireshark you will see translation of ARP datagram to English as: " Who has 192.168.0.201? Tell 192.168.0.27"

Packet itself:
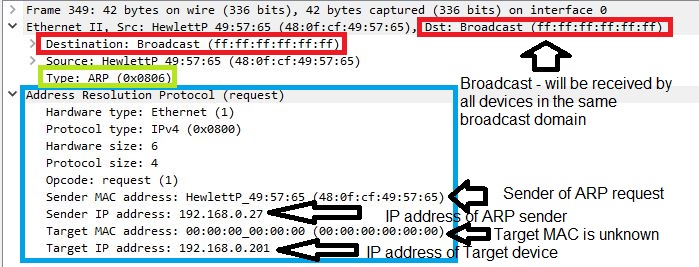 All devices in network segment will receive ARP. Source device knows IP address of Target device, but does not know L2 address. ARP is a message inside L2 frame (light blue) that can be translated as:
All devices in network segment will receive ARP. Source device knows IP address of Target device, but does not know L2 address. ARP is a message inside L2 frame (light blue) that can be translated as:
I am device with IP address 192.168.0.27, my MAC address is 480F.CF49:5765, I am looking for MAC address of device 192.168.0.201. Device 192.168.0.201 send me your MAC address (if there is device with this IP address please respond to this message).
Since all devices are receiving message, if target device 192.168.0.201 is present in network segment and it is permitted to respond to ARP requests, device will send ARP reply and inform sender about its MAC address.
But then again, technically, you can have L3 routing protocol that operates at L2 (e.g. IS-IS), but still I would say that ARP operates at L2 to provide information about L3.
:)
ARP just has L2 encapsulation (L2 frame type 0x0806 define frame as ARP). It is broadcasted to all devices since destination is FFFF.FFFF.FFFF. Device that receives L2 frame will check if ARP message is address to it (check IP address inside of ARP message of target device against its own IP address). In Wireshark you will see translation of ARP datagram to English as: " Who has 192.168.0.201? Tell 192.168.0.27"
Packet itself:
I am device with IP address 192.168.0.27, my MAC address is 480F.CF49:5765, I am looking for MAC address of device 192.168.0.201. Device 192.168.0.201 send me your MAC address (if there is device with this IP address please respond to this message).
Since all devices are receiving message, if target device 192.168.0.201 is present in network segment and it is permitted to respond to ARP requests, device will send ARP reply and inform sender about its MAC address.
But then again, technically, you can have L3 routing protocol that operates at L2 (e.g. IS-IS), but still I would say that ARP operates at L2 to provide information about L3.
:)
ASKER
It looks as if no easy answer will come.
I will need to use a third party library (probably winpcap) to sniff at layer 2.
I did see a promising thread about using a custom NDIS driver, but I've not had time to try that yet.
I will need to use a third party library (probably winpcap) to sniff at layer 2.
I did see a promising thread about using a custom NDIS driver, but I've not had time to try that yet.
ASKER
for any other readers. This is the thread I mentioned.
https://www.codeproject.co
Until I look at this properly, I don't know ihow easy it will be to use compared with winpcap.
I'd prefer to use this instead of relying on a third party library that requires an extra installation and may or may not support future windows versions
https://www.codeproject.co
Until I look at this properly, I don't know ihow easy it will be to use compared with winpcap.
I'd prefer to use this instead of relying on a third party library that requires an extra installation and may or may not support future windows versions
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
http://www.networksorcery.com/enp/protocol/arp.htm
http://www.tcpipguide.com/free/t_ARPMessageFormat.htm
For complete details check RFCs (bottom of the first link).