How does java function becomes vulnerable if the order is changed
Hi,
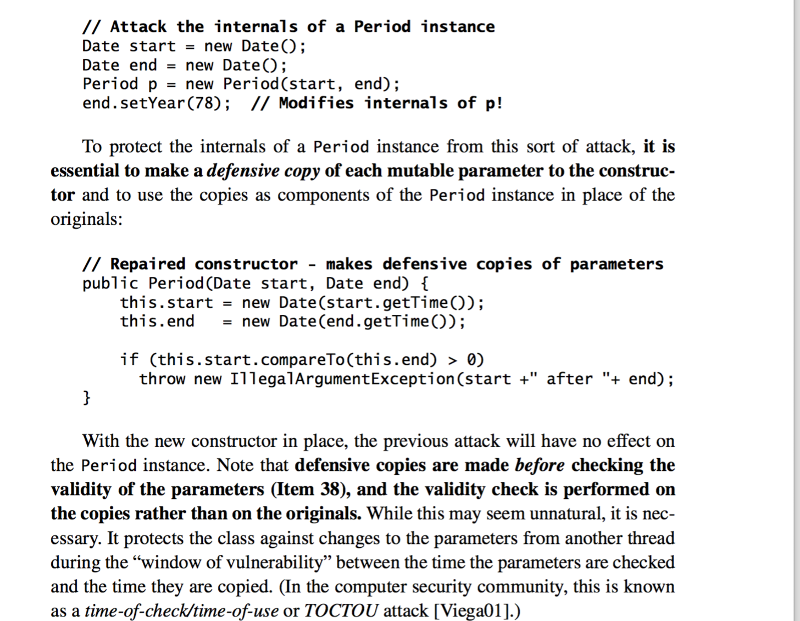
I am attaching a screenshot from a code in effective java book. In this the author says -
 I dont get this window of vulnerability thing. What exactly he is talking about.. Please suggest an example where the check was done before the assignment and due to some multithreaded thing There was an issue.
I dont get this window of vulnerability thing. What exactly he is talking about.. Please suggest an example where the check was done before the assignment and due to some multithreaded thing There was an issue.
Thanks
I am attaching a screenshot from a code in effective java book. In this the author says -
Note that defensive copies are made before checking the validity of the parameters (Item 38), and the validity check is performed on the copies rather than on the originals. While this may seem unnatural, it is nec- essary. It protects the class against changes to the parameters from another thread during the “window of vulnerability” between the time the parameters are checked and the time they are copied. (In the computer security community, this is known as a time-of-check/time-of-use or TOCTOU
 I dont get this window of vulnerability thing. What exactly he is talking about.. Please suggest an example where the check was done before the assignment and due to some multithreaded thing There was an issue.
I dont get this window of vulnerability thing. What exactly he is talking about.. Please suggest an example where the check was done before the assignment and due to some multithreaded thing There was an issue. Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Both comments are correct.