Member_2_7966113
asked on
Unable is issue command in Azure Powershell
ASKER
Hi Lawrence,
The full code is as follows:
The full code is as follows:
$cert = new-object System.Security.Cryptography.X509Certificates.X509Certificate2 $keysPath, $passwordEnc
$cert.Thumbprint
Hi,
Is the purpose of the whole script is to load in a .pfx file with password and then to retrieve the thumbprint?
If that's the case you can use this:
You can change the flag "Exportable" to one of, or combination of the followings:
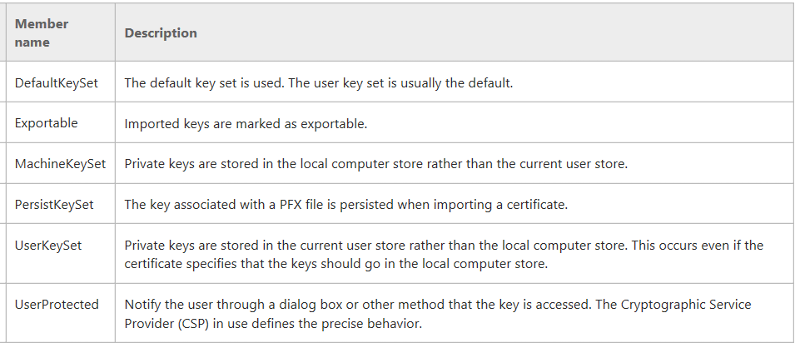
Reference:
https://msdn.microsoft.com/en-us/library/system.security.cryptography.x509certificates.x509keystorageflags(v=vs.110).aspx
Cheers.
Is the purpose of the whole script is to load in a .pfx file with password and then to retrieve the thumbprint?
If that's the case you can use this:
$cert=New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$cert.Import("YourPFXFilePath.pfx", "password", [System.Security.Cryptography.X509Certificates.X509KeyStorageFlags]"Exportable")You can change the flag "Exportable" to one of, or combination of the followings:
Reference:
https://msdn.microsoft.com/en-us/library/system.security.cryptography.x509certificates.x509keystorageflags(v=vs.110).aspx
Cheers.
ASKER
Hi Lawrence,
So, in light of your suggestions, I thought I would start from scratch.
I entered the following commands:
ResourceGroupName : mykevaultrg
Location : westus
ProvisioningState : Succeeded
Tags :
ResourceId : /subscriptions/zxxx.xxxxx.
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> New-AzureRmKeyVault -VaultName $vaultName -resourceGroup $resourceGroup -Location $location -EnabledForDeployment -EnabledForTemplateDeploym
Vault Name : mykevaultname
Resource Group Name : mykevaultrg
Location : WestUS
Resource ID : /subscriptions/xxxx.xxxxx.
providers/Microsoft.KeyVau
Vault URI : https://mykevaultname.vault.azure.net
Tenant ID : xxxxx.xxx.xxxx.xxxx.xxxxxx
Enabled For Template Deployment? : True
Enabled For Disk Encryption? : False
Soft Delete Enabled? :
Access Policies :
Tenant ID :
xxxxxxxxxxxxxxxxxx.xxxxxxx
Object ID :
6a451291-3b03-4255-98e3-99
Application ID :
Display Name : Carlton Patterson
(cpatte7372_outlook.com#EX
Permissions to Keys : get, create, delete, list,
update, import, backup, restore, recover
Permissions to Secrets : get, list, set, delete, backup,
restore, recover
Permissions to Certificates : get, delete, list, create,
import, update, deleteissuers, getissuers, listissuers, managecontacts,
manageissuers, setissuers, recover
Permissions to (Key Vault Managed) Storage : delete, deletesas, get, getsas,
list, listsas, regeneratekey, set, setsas, update
Tags :
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> $keypath = "c:\certs\$keyname.pfx"
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> $passwordEnc = ConvertTo-SecureString -String $password -AsPlainText -Force
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> $bytes = [System.IO.File]::ReadAllB
The script is still looking for c:\azurekeys\.pfx even though I didn't specify above, see error below
Exception calling "ReadAllBytes" with "1" argument(s): "Could not find file 'c:\azurekeys\.pfx'."
At line:1 char:1
+ $bytes = [System.IO.File]::ReadAllB
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : FileNotFoundException
Thanks for the additional information, but can you help resolve the above before I implement the rest of your suggestion.
Cheers
So, in light of your suggestions, I thought I would start from scratch.
I entered the following commands:
ResourceGroupName : mykevaultrg
Location : westus
ProvisioningState : Succeeded
Tags :
ResourceId : /subscriptions/zxxx.xxxxx.
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> New-AzureRmKeyVault -VaultName $vaultName -resourceGroup $resourceGroup -Location $location -EnabledForDeployment -EnabledForTemplateDeploym
Vault Name : mykevaultname
Resource Group Name : mykevaultrg
Location : WestUS
Resource ID : /subscriptions/xxxx.xxxxx.
providers/Microsoft.KeyVau
Vault URI : https://mykevaultname.vault.azure.net
Tenant ID : xxxxx.xxx.xxxx.xxxx.xxxxxx
Enabled For Template Deployment? : True
Enabled For Disk Encryption? : False
Soft Delete Enabled? :
Access Policies :
Tenant ID :
xxxxxxxxxxxxxxxxxx.xxxxxxx
Object ID :
6a451291-3b03-4255-98e3-99
Application ID :
Display Name : Carlton Patterson
(cpatte7372_outlook.com#EX
Permissions to Keys : get, create, delete, list,
update, import, backup, restore, recover
Permissions to Secrets : get, list, set, delete, backup,
restore, recover
Permissions to Certificates : get, delete, list, create,
import, update, deleteissuers, getissuers, listissuers, managecontacts,
manageissuers, setissuers, recover
Permissions to (Key Vault Managed) Storage : delete, deletesas, get, getsas,
list, listsas, regeneratekey, set, setsas, update
Tags :
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> $keypath = "c:\certs\$keyname.pfx"
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> $passwordEnc = ConvertTo-SecureString -String $password -AsPlainText -Force
PS C:\Users\Carlton\Google Drive\AZURE\Service Fabric> $bytes = [System.IO.File]::ReadAllB
The script is still looking for c:\azurekeys\.pfx even though I didn't specify above, see error below
Exception calling "ReadAllBytes" with "1" argument(s): "Could not find file 'c:\azurekeys\.pfx'."
At line:1 char:1
+ $bytes = [System.IO.File]::ReadAllB
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : FileNotFoundException
Thanks for the additional information, but can you help resolve the above before I implement the rest of your suggestion.
Cheers
If possible please post your screen captures during step by step execution from very beginning (please remove your personal sensitive data), I can read them through and give you some suggestion if I can.
Cheers.
Cheers.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi Lawrence,
Great answer. I have applied your suggestion and I have managed to get past the problem with keySpath.
However, the script now fails at
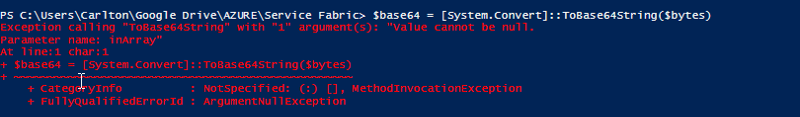
I get the following error message, see image:
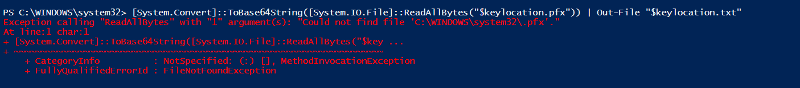
Can you assist?
I have attached the script again:
Great answer. I have applied your suggestion and I have managed to get past the problem with keySpath.
However, the script now fails at
[System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes("$keylocation.pfx")) | Out-File "$keylocation.txt"I get the following error message, see image:

Can you assist?
I have attached the script again:
$subscriptionId = 'xxxx.xxxxx.xxxxxx.xxxxxx'; #Pre Production
$resourceGroup = 'mykevaultrg'
$location = 'WestUS'
$vaultName = 'mykevault'
$keyname = 'mykevaultname'
$password = 'Patters0n'
Select-AzureRmSubscription -SubscriptionId $subscriptionId
Set-AzureRmContext -SubscriptionId $subscriptionId
if(Get-AzureRmResourceGroup -Name $resourceGroup){
Write-Output "Deleteing Resource Group $resourceGroup"
Remove-AzureRmResourceGroup -Name $resourceGroup -Force
}
else
{
Write-Output 'No Resource Group found'
}
New-AzureRmResourceGroup -Name $resourceGroup -Location $location
New-AzureRmKeyVault -VaultName $vaultName -resourceGroup $resourceGroup -Location $location -EnabledForDeployment -EnabledForTemplateDeployment
Import-Module "$THIS_SCRIPTS_DIRECTORY\ServiceFabricRPHelpers.psm1"
$keypath = "c:\azurekeys\$keyname.pfx"
$passwordEnc = ConvertTo-SecureString -String $password -AsPlainText -Force
$bytes = [System.IO.File]::ReadAllBytes($keypath)
$base64 = [System.Convert]::ToBase64String($bytes)
$jsonBlob = @{
data = $base64
dataType = 'pfx'
password = $password
} | ConvertTo-Json
$contentBytes = [System.Text.Encoding]::UTF8.GetBytes($jsonBlob)
$content = [System.Convert]::Tobase64String($contentBytes)
$secretValue = ConvertTo-SecureString -String $content -AsPlainText –Force
Set-AzureKeyVaultSecret -VaultName $vaultName -Name $keyname -SecretValue $secretValue
$cert = new-object System.Security.Cryptography.X509Certificates.X509Certificate2 $keysPath, $passwordEnc
$cert.Thumbprint
#Create Self Signed Cert
Invoke-AddCertToKeyVault -SubscriptionId $subscriptionId -resourceGroup $resourceGroup -Location $location -VaultName $vaultName -CertificateName $keyname -Password $pwd -CreateSelfSignedCertificate -DnsName 'cds-pp-02-careersvc.westeurope.cloudapp.azure.com' -OutputPath 'C:\certs\'
#Use existing cert
#Invoke-AddCertToKeyVault -SubscriptionId $subscriptionId -resourceGroup $resourceGroup -Location $location -VaultName $vaultName -CertificateName cds-prd-01-careersvc -Password $pwd -UseExistingCertificate -ExistingPfxFilePath $keypath
[System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes("$keylocation.pfx")) | Out-File "$keylocation.txt"
Get-PfxCertificate -FilePath $keypath\NameOfCert.pfxASKER
Hi Experts,
Any more thoughts on this?
Any more thoughts on this?
ASKER
This fixed the problem. Thanks Lawrence
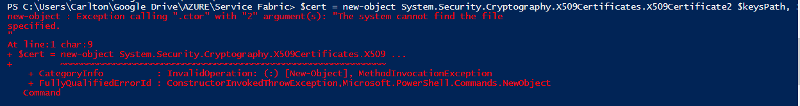
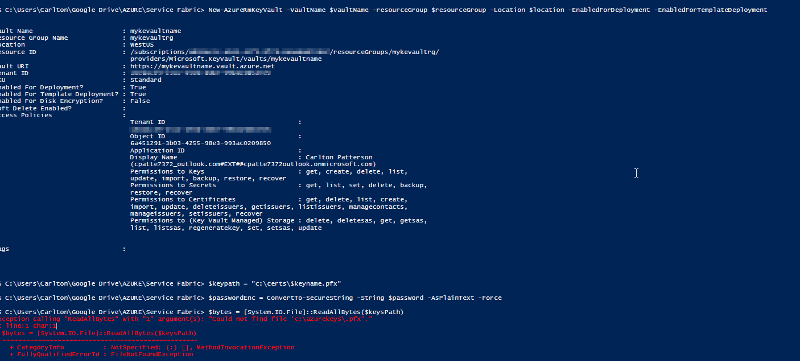
Open in new window
Cheers.