Nick Jameson
asked on
AD Security
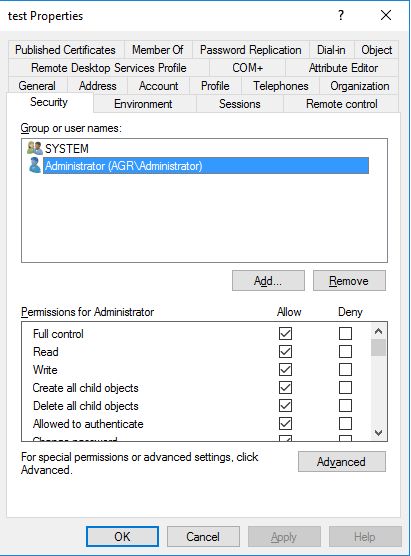
Please tell me why any account in admin groups can change security data while there is only me and "administrator" account in "Allowed" list?
I can log in under user that in "domain admins" group and can set up any rights/permissions for my account.
I can log in under user that in "domain admins" group and can set up any rights/permissions for my account.
What allowed list? Can you offer a screen shot?
ASKER
can log in under another admin accountThat is the purpose of an admin account and why you should limit members
https://www.experts-exchange.com/articles/29596/Securing-Active-Directory-Administrators-Groups.html
You have disabled AD user object inheritance and then removed all but administrator
In that case another user though it is member of domain admins, he should not get any accesss to user account
I just checked quickly in my lab and it is working as expected
I believe the test user you created previously must be part of high privileged AD group such as domain admins and hence its security descriptor must be getting set to default value every hour and thus getting other admins access to it. This is because admincount is set to 1
Try below
Create new AD user
disable its inheritance
remove all but administrator
now logon with another admin account and check if you are able to do any changes, I believe you will not
In that case another user though it is member of domain admins, he should not get any accesss to user account
I just checked quickly in my lab and it is working as expected
I believe the test user you created previously must be part of high privileged AD group such as domain admins and hence its security descriptor must be getting set to default value every hour and thus getting other admins access to it. This is because admincount is set to 1
Try below
Create new AD user
disable its inheritance
remove all but administrator
now logon with another admin account and check if you are able to do any changes, I believe you will not
You can learn about the best practices of securing active directory in following guides.
https://www.beyondtrust.com/wp-content/uploads/wp-best-practices-auditing-active-directory.pdf?1464831369
http://www.paramountdefenses.com/active-directory-security/guides.html
https://www.beyondtrust.com/wp-content/uploads/wp-best-practices-auditing-active-directory.pdf?1464831369
http://www.paramountdefenses.com/active-directory-security/guides.html
Why is there no feedback on Mahesh's suggestion? It's the only possible explanation.
I think I got the issue
Though you have removed all admin account except one from ACL, account owner is by default "domain admins"
As a fact other admin account can make changes to acl as it is also part of domain admins group
If you want to check, you can remove "domain admins" from ownership and add any other account (say x) there
now if other admin user logged on (say y) , he would not be able to make security permission changes unless he take account ownership
This is same like standard NTFS ACL rule
I don't want to object the question however if you could keep this question open and try above you will get the answer
Though you have removed all admin account except one from ACL, account owner is by default "domain admins"
As a fact other admin account can make changes to acl as it is also part of domain admins group
If you want to check, you can remove "domain admins" from ownership and add any other account (say x) there
now if other admin user logged on (say y) , he would not be able to make security permission changes unless he take account ownership
This is same like standard NTFS ACL rule
I don't want to object the question however if you could keep this question open and try above you will get the answer
Sara, the author did not answer his own question, that is why I object.
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
https://technet.microsoft.com/en-us/library/cc700835.aspx?f=255&MSPPError=-2147217396
Group Policy: Administrator Rights for Specific Users on Specific Computers:
https://serverfault.com/questions/79614/group-policy-administrator-rights-for-specific-users-on-specific-computers
Keeping your Active Directory secure when delegating privileges to users:
https://www.lepide.com/blog/keeping-your-active-directory-secure-when-delegating-privileges-to-users/
Hope this helps!