PROACTIVETG
asked on
Active Directory User Account gets locked out daily.
Active Directory User Account gets locked out daily.
I have a user who get's his active directory account locked out once a day. He changed his password last week and it has been happening every day since. Obviously, there's something trying to login to his account using his old credentials which locks his account. I'm not sure why it only happens once a day or what the device could be.
They have an on-site exchange server. His account only shows 3 Activesync devices, all of which he said he has the new password in. He said he's never logged into another computer on the domain and no one else has access to his mailbox in their outlook.
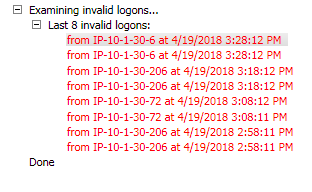
The main issue I'm having is figuring out the event logs for the lockout. I find the event that locks it out (and attached a screen shot), but the "Caller Computer Name" says IP-10-1-30-72. That IP isnt part of their network IP scheme, so it cant be coming from the internal Lan.
It looks like the failed logins come from the same couple IPs on the same network
I have a user who get's his active directory account locked out once a day. He changed his password last week and it has been happening every day since. Obviously, there's something trying to login to his account using his old credentials which locks his account. I'm not sure why it only happens once a day or what the device could be.
They have an on-site exchange server. His account only shows 3 Activesync devices, all of which he said he has the new password in. He said he's never logged into another computer on the domain and no one else has access to his mailbox in their outlook.
The main issue I'm having is figuring out the event logs for the lockout. I find the event that locks it out (and attached a screen shot), but the "Caller Computer Name" says IP-10-1-30-72. That IP isnt part of their network IP scheme, so it cant be coming from the internal Lan.
It looks like the failed logins come from the same couple IPs on the same network

Any 10.0.0.0/8 IP address is local. Public routers won't route that private subnet. So it's on your network *somewhere.* And can reach the server, which means some sort of router has rules in place to move traffic between that subnet and one of your subnets.
Looks like you are using the Netwrix account lockout examiner, which is good. But as the previous expert commented, it's coming from a machine on the network, or perhaps a VPN or WAN machine somewhere.
For the 3 Activesync devices, check each one for any stored credentials by looking in Credential Manager. Also, the user indicated he has not logged into any other machines, but double check with him that he also didnt use a Remote Desktop connection to a machine and left it in disconnect state as this can cause this issue.
Regards
For the 3 Activesync devices, check each one for any stored credentials by looking in Credential Manager. Also, the user indicated he has not logged into any other machines, but double check with him that he also didnt use a Remote Desktop connection to a machine and left it in disconnect state as this can cause this issue.
Regards
Worth checking, of course. But mobile devices would usually have a public IP. And with three UPS logged, he would've has to have forgotten all 3. This feels like it's something... Different.
Is Activesync mobile only? Yeah that may be the case.
So it really is down to locating the 10.1.30.X machines and check for saved credentials and/or disconnected sessions.
So it really is down to locating the 10.1.30.X machines and check for saved credentials and/or disconnected sessions.
Hello,
I agree with the companions.
The block should also come directly from your machine.
Validate the credential manager and remove all credentials that are stored.
Also the user must leave his account logged on another computer with the previous password, it is worth validating again.
If you have VPN, and you connect from another computer, validate the credential manager and delete the stored credentials.
regards...
I agree with the companions.
The block should also come directly from your machine.
Validate the credential manager and remove all credentials that are stored.
Also the user must leave his account logged on another computer with the previous password, it is worth validating again.
If you have VPN, and you connect from another computer, validate the credential manager and delete the stored credentials.
regards...
ASKER
This is quite hard to figure out.
The site has a flat network of 10.1.1.0/24. No VLAN, no layer 3 switches, all devices on same 10.1.1.X network.
Things I've done to try and stop it:
The office is closed for the night so no activesync devices are currently in the office.
I rebooted all workstaions/server incase one of them had something open that was using his old credentials.
I limited his username to only be able to log into his workstation in AD.
I temporarily disabled his OWA web access incase there was some brute-force going on.
I did a packet capture on the Sonicwall for any traffic with 10.1.30.X and nothing was being captured for it.
Added measure, I even blocked any Lan>Lan traffic on the sonicwall that comes from the 10.1.30.X subnet.
Cant ping the 10.1.30.X address from the firewall, workstation, servers, wireless access points.
After all this, it's still happening, and from the same 3 IPs:
10.1.30.217
10.1.30.72
10.1.30.237
I'll take another look tomorrow.
The site has a flat network of 10.1.1.0/24. No VLAN, no layer 3 switches, all devices on same 10.1.1.X network.
Things I've done to try and stop it:
The office is closed for the night so no activesync devices are currently in the office.
I rebooted all workstaions/server incase one of them had something open that was using his old credentials.
I limited his username to only be able to log into his workstation in AD.
I temporarily disabled his OWA web access incase there was some brute-force going on.
I did a packet capture on the Sonicwall for any traffic with 10.1.30.X and nothing was being captured for it.
Added measure, I even blocked any Lan>Lan traffic on the sonicwall that comes from the 10.1.30.X subnet.
Cant ping the 10.1.30.X address from the firewall, workstation, servers, wireless access points.
After all this, it's still happening, and from the same 3 IPs:
10.1.30.217
10.1.30.72
10.1.30.237
I'll take another look tomorrow.
If you are AD domain admin then use Account lockout tool and see where it shows account getting locked.
https://www.microsoft.com/en-in/download/details.aspx?id=18465
Check the credential managers in those servers and delete any old credentials stored.
https://www.microsoft.com/en-in/download/details.aspx?id=18465
Check the credential managers in those servers and delete any old credentials stored.
There may be many causes for account locked out.
->user's account in stored user name and passwords
->user's account tied to persistent mapped drive
->user's account as a service account
->user's account used as an IIS application pool identity
->user's account tied to a scheduled task
->un-suspending a virtual machine after a user's pw as changed
->A SMARTPHONE!!!
For more refer KB article:http://technet.microsoft.com/en-us/library/cc773155(WS.10).aspx
check if the computer is infected by viruses, Read this KB about Win32/Conficker worm: http://support.microsoft.com/kb/962007
Download and install the Account Lockout and Management Tools, this will help you pinpoint the location of the failed auth attempts: https://www.microsoft.com/en-in/download/details.aspx?id=18465
Try the following tool to find out account lockout.
https://www.netwrix.com/account_lockout_troubleshooting.html
https://www.jijitechnologies.com/jiji-account-lockout-tool.aspx
->user's account in stored user name and passwords
->user's account tied to persistent mapped drive
->user's account as a service account
->user's account used as an IIS application pool identity
->user's account tied to a scheduled task
->un-suspending a virtual machine after a user's pw as changed
->A SMARTPHONE!!!
For more refer KB article:http://technet.microsoft.com/en-us/library/cc773155(WS.10).aspx
check if the computer is infected by viruses, Read this KB about Win32/Conficker worm: http://support.microsoft.com/kb/962007
Download and install the Account Lockout and Management Tools, this will help you pinpoint the location of the failed auth attempts: https://www.microsoft.com/en-in/download/details.aspx?id=18465
Try the following tool to find out account lockout.
https://www.netwrix.com/account_lockout_troubleshooting.html
https://www.jijitechnologies.com/jiji-account-lockout-tool.aspx
Troubleshooting account lockout the PSS way:
https://blogs.technet.microsoft.com/instan/2009/09/01/troubleshooting-account-lockout-the-pss-way/
Since the account lockout issue could be caused by many factors. Here is an article which explore what are the common root causes of account lockouts and how resolve them: https://www.lepide.com/blog/what-are-the-common-root-causes-of-account-lockouts-and-do-i-resolve-them/
How to track and troubleshoot User Account Lockouts with LepideAuditor:
https://www.lepide.com/how-to/track-and-troubleshoot-user-account-lockouts-with-lepideauditor.html
How to Troubleshoot Account Lockout in Active Directory:
http://expert-advice.org/active-directory/how-to-troubleshoot-account-lockout-in-active-directory/
https://blogs.technet.microsoft.com/instan/2009/09/01/troubleshooting-account-lockout-the-pss-way/
Since the account lockout issue could be caused by many factors. Here is an article which explore what are the common root causes of account lockouts and how resolve them: https://www.lepide.com/blog/what-are-the-common-root-causes-of-account-lockouts-and-do-i-resolve-them/
How to track and troubleshoot User Account Lockouts with LepideAuditor:
https://www.lepide.com/how-to/track-and-troubleshoot-user-account-lockouts-with-lepideauditor.html
How to Troubleshoot Account Lockout in Active Directory:
http://expert-advice.org/active-directory/how-to-troubleshoot-account-lockout-in-active-directory/
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thanks everyone