Mike Schneider
asked on
Connect 2 offices that have their own WAN with public statics. To share Wan's and a NAS at Main office. With failsafe for main office.
The goal is to connect the Main & Seed Office That have a city street and a railroad between them. via the point to point wireless to be able to share the higher speed
Of the Charter cable along with giving the Seed office access to the NAS.
But I need to have a failsafe if the wireless goes down for any reason that the Main office
Would not lose their internet connection all together. Just fall back to the 10 m Fiber
What do you think the best route would be for this setup.
Running any cable from the feed mill to the seed office is not an option with the railroad tracks
And a city street in the way.
Thanks in advance.
Of the Charter cable along with giving the Seed office access to the NAS.
But I need to have a failsafe if the wireless goes down for any reason that the Main office
Would not lose their internet connection all together. Just fall back to the 10 m Fiber
What do you think the best route would be for this setup.
Running any cable from the feed mill to the seed office is not an option with the railroad tracks
And a city street in the way.
Thanks in advance.
If you cannot connect by Ethernet cable, you will need to hook up a high strength wireless transmitter / receiver to do the job.
ASKER
Yes i forgot to put that part in there this is the one i was thinking about.
http://a.co/fyeXQc2
Thanks
Mike
http://a.co/fyeXQc2
Thanks
Mike
Since you cannot use cable, that is the only other way.
ASKER
That part i understand the part i am not sure of is how to configure the SonicWALL to handle it?
You would have to configure the WAN on your router to talk to the receiving point. It would not likely be automatic.
High power won't help much of there isn't line of sight for the antennas to see one another.....
What's in between besides trains now and then?
What's in between besides trains now and then?
ASKER
There is a line of sight as there is a large tower platform that it can be connected to on the Feed Mill The height of the other building and trains won't be an issue.
ASKER
Sorry I did not realize that the overview did not upload before. FEE-Network-Plan.pdf is the name.
ASKER
I just uploaded a picture from Google earth the new Feed mill is not in the picture the towers on the Feed mill are as tall or taller than the existing grain elevator in the picture so getting it high enough to get a clear line of sight.
Hi Mike,
First I'd strongly recommend getting a new SonicWALL...like at least a TZ300 (but you'd need to size this to the specific requirements of the network accordingly). The one you have, TZ180, is 4 generations old - to say its EOL (End of Life) is a severe understatement. It is plainly not effective nor robust enough to mitigate and protect the network from today's threat landscape nor is it robust enough to configure it to do what you need it to. Then if you can take back the Meraki MX64 I would in a heartbeat its only running SPI (Stateful Packet Inspection) a technology developed in 1996. Procure two SonicWALLs and it will significantly enhance your security, functionality and performance.
So, let's backup a second and think about the architecture logically rather than physically. If the goal is to "...connect the Main & Seed Office...share resources between them" then from your diagram it is alluding me as to why you wouldn't just connect them via a S2S (Site-to-Site) VPN and bypass the Ethernet/Wireless Bridge aka P2P (Point-to-Point) links altogether? The VPN would be as stable as the ISPs and would not introduce multiple points of failure in the network nor the vulnerabilities & insecurities of Wireless. If there is any sensitive data being transmitted it may be a concern since an adversary can literally park their car somewhat near by and hack all day and all night without any detection, prevention or alerting going on with the devices you linked. The Feed Mill appears to be connected to the Main Office so by connecting the Main and Seed Offices you will be able to share all resources in every location if configured properly!
If you should require more resiliency and/or redundancy then you'd want to look into getting another ISP on either or both ends (dual WANs). Then the firewalls should be configured for PBLB (Policy-Based Load Balancing) with fail-over and fail-back based on automatic probe detection. The VPN would be configured to do so as well (PB fail-over & fail-back). I only mentioned this because you talked about redundancy in case the Wireless Bridge were to fail. So again in no way am I suggesting that you should or need to get dual WANs at each location in order to make this work with a S2S VPN.
Although it is not my recommendation to implement a Wireless Bridge here because of the aforementioned, I would like to clear up some things in that regard. Consider the context of line of sight a bit misleading because it doesn't address (calculate) the Fresnel Zones, which are the diameters of the shapes between both points as it relates to radio waves. Radio waves (variable diameters) are not like laser beams (precise, very narrow in diameter). So when people discuss line of sight it is in the context of thinking like they are using a strong laser pointer opposed to accurately understanding the full three dimensional diameters between the two link points (Tx & Rx). When reliability and throughput matter you must always compute the diameter of the Fresnel Zones so you can validate that its actually free from all obstacles. The diameter depends on the distance and the frequency used.
If r=radius in feet, d=distance in miles, and f=frequency in GHz;
then, the formula is r=72.05*[the square root of]d/4f. The image below should help with the visual perception of what I'm saying.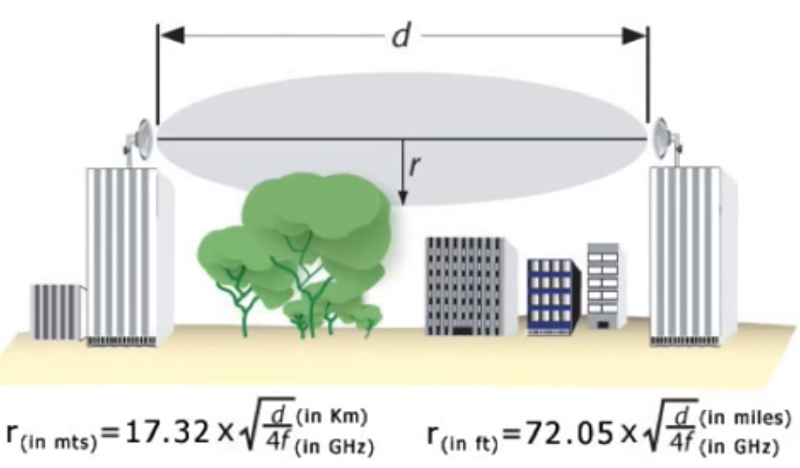
For example, if the distance (d) is 660 ft or an 1/8 of a mile (.125) and the frequency is 5GHz then applying that to the formula would yield a 5.69 ft radius, which would be a 11.4 ft cylinder (if you will) where the line of sight is the center of that cylinder. Now you need to make sure 11.4 ft is clear from obstructions in that path for my example only.
Let me know if you have any questions!
First I'd strongly recommend getting a new SonicWALL...like at least a TZ300 (but you'd need to size this to the specific requirements of the network accordingly). The one you have, TZ180, is 4 generations old - to say its EOL (End of Life) is a severe understatement. It is plainly not effective nor robust enough to mitigate and protect the network from today's threat landscape nor is it robust enough to configure it to do what you need it to. Then if you can take back the Meraki MX64 I would in a heartbeat its only running SPI (Stateful Packet Inspection) a technology developed in 1996. Procure two SonicWALLs and it will significantly enhance your security, functionality and performance.
So, let's backup a second and think about the architecture logically rather than physically. If the goal is to "...connect the Main & Seed Office...share resources between them" then from your diagram it is alluding me as to why you wouldn't just connect them via a S2S (Site-to-Site) VPN and bypass the Ethernet/Wireless Bridge aka P2P (Point-to-Point) links altogether? The VPN would be as stable as the ISPs and would not introduce multiple points of failure in the network nor the vulnerabilities & insecurities of Wireless. If there is any sensitive data being transmitted it may be a concern since an adversary can literally park their car somewhat near by and hack all day and all night without any detection, prevention or alerting going on with the devices you linked. The Feed Mill appears to be connected to the Main Office so by connecting the Main and Seed Offices you will be able to share all resources in every location if configured properly!
If you should require more resiliency and/or redundancy then you'd want to look into getting another ISP on either or both ends (dual WANs). Then the firewalls should be configured for PBLB (Policy-Based Load Balancing) with fail-over and fail-back based on automatic probe detection. The VPN would be configured to do so as well (PB fail-over & fail-back). I only mentioned this because you talked about redundancy in case the Wireless Bridge were to fail. So again in no way am I suggesting that you should or need to get dual WANs at each location in order to make this work with a S2S VPN.
Although it is not my recommendation to implement a Wireless Bridge here because of the aforementioned, I would like to clear up some things in that regard. Consider the context of line of sight a bit misleading because it doesn't address (calculate) the Fresnel Zones, which are the diameters of the shapes between both points as it relates to radio waves. Radio waves (variable diameters) are not like laser beams (precise, very narrow in diameter). So when people discuss line of sight it is in the context of thinking like they are using a strong laser pointer opposed to accurately understanding the full three dimensional diameters between the two link points (Tx & Rx). When reliability and throughput matter you must always compute the diameter of the Fresnel Zones so you can validate that its actually free from all obstacles. The diameter depends on the distance and the frequency used.
If r=radius in feet, d=distance in miles, and f=frequency in GHz;
then, the formula is r=72.05*[the square root of]d/4f. The image below should help with the visual perception of what I'm saying.
For example, if the distance (d) is 660 ft or an 1/8 of a mile (.125) and the frequency is 5GHz then applying that to the formula would yield a 5.69 ft radius, which would be a 11.4 ft cylinder (if you will) where the line of sight is the center of that cylinder. Now you need to make sure 11.4 ft is clear from obstructions in that path for my example only.
Let me know if you have any questions!
Do you have any questions with what I wrote?
ASKER
Blue Street. Sorry, I have been busy I see your point about the VPN with the 10/10 internet at the main office that did not work that great but I was there today and we have a site survey setup with Charter to see about 100/10 service. Then the VPN would work fine. Then I would not have to mess with the P2P wireless. I was not aware of the Meriki security issues I had gotten it with attending the webanair, the SonicWALL has never been my faviorate anyway they are a pain to configure. I am looking at possibly doing a FireIP setup or something from Ubiquiti.
Gotcha. That would be great if they can provide you with a 100x10...that will save a ton of money!
In terms of Security Appliances, its up to you but I prefer SonicWALLs. They have come a loooooong ways since the model you have. They are one of the best defenses you can get in the market today. I could go on and on about them but if you look at the NIST CVE sites they have never been compromised whereas Cisco, and others have not to mention they also have well known backdoors! They virtually cannot leak either because of their patented RFDPI (Reassembly-Free Deep Packet Inspection) technology; there is not HDD, memory or cache to be compromised; its all happening in real-time. In the big NHS ransomware apocalypse, the sites with SonicWALLs remained up because they were able to block zero-day attacks and stopped the ransomeware infections 3-weeks before they were officially recognized. All the NHS sites that had Cisco (enterprise grade gear), Fortinet, Sophos, etc. protecting them went down. If that isn't real-world testimony...I don't know what is! They can block Spectre/Meltdown in unpatched vulnerable systems at the gateway because of another of their patented technologies called RTDMI (Real-Time Deep Memory Inspection). The Spectre/Meltdown vulnerability is back too by the way; there were flaws in the patches. Ask another vendor how they are protecting again fileless malware & ransomware..that's right fileLESS...the attack never touches the disk! SonicWALL is the only one that I know of protecting against this. When you are shopping for security products the very mininum requirement is DPI (Deep Packet Inspection)...if they aren't forget about them they are worthless against today's threat landscape.
Ubiquity have very solid wireless products; they last and they are dependable but that is where they start and end. Their firewalls are junk, SPI only again. The only negative I have with Ubiquity is they have a cheesy "wireless survey" built into their app that gives people false ideas of what really is needed to perform a proper wireless survey. Another issue is on the security side - you are very limited to what you can do with them opposed to something like SonicPoints where they can actually find and block rogue WAPs, and run the full SecStack on the wireless.
FireIP is a private proxy service not a firewall/UTM. It is something you'd do as an addition to but not a complete solution. SonicWALL already has multiple private proxies build-in so there would be no need if you went that route.
In terms of Security Appliances, its up to you but I prefer SonicWALLs. They have come a loooooong ways since the model you have. They are one of the best defenses you can get in the market today. I could go on and on about them but if you look at the NIST CVE sites they have never been compromised whereas Cisco, and others have not to mention they also have well known backdoors! They virtually cannot leak either because of their patented RFDPI (Reassembly-Free Deep Packet Inspection) technology; there is not HDD, memory or cache to be compromised; its all happening in real-time. In the big NHS ransomware apocalypse, the sites with SonicWALLs remained up because they were able to block zero-day attacks and stopped the ransomeware infections 3-weeks before they were officially recognized. All the NHS sites that had Cisco (enterprise grade gear), Fortinet, Sophos, etc. protecting them went down. If that isn't real-world testimony...I don't know what is! They can block Spectre/Meltdown in unpatched vulnerable systems at the gateway because of another of their patented technologies called RTDMI (Real-Time Deep Memory Inspection). The Spectre/Meltdown vulnerability is back too by the way; there were flaws in the patches. Ask another vendor how they are protecting again fileless malware & ransomware..that's right fileLESS...the attack never touches the disk! SonicWALL is the only one that I know of protecting against this. When you are shopping for security products the very mininum requirement is DPI (Deep Packet Inspection)...if they aren't forget about them they are worthless against today's threat landscape.
Ubiquity have very solid wireless products; they last and they are dependable but that is where they start and end. Their firewalls are junk, SPI only again. The only negative I have with Ubiquity is they have a cheesy "wireless survey" built into their app that gives people false ideas of what really is needed to perform a proper wireless survey. Another issue is on the security side - you are very limited to what you can do with them opposed to something like SonicPoints where they can actually find and block rogue WAPs, and run the full SecStack on the wireless.
FireIP is a private proxy service not a firewall/UTM. It is something you'd do as an addition to but not a complete solution. SonicWALL already has multiple private proxies build-in so there would be no need if you went that route.
we have a site survey setup with Charter to see about 100/10 service. Then the VPN would work fine.If 10 "down" isn't good enough then 100 "up" isn't going to help that one bit. Perhaps I didn't understand but here is what I mean:
When you operate a VPN, every packet has to go both "up" at one end AND "down" at the other. That means that the smaller rate will dominate. So, 10/10 is just as good as 100/10 for a VPN. Just maybe not "good enough".
ASKER
Fred Marshall now that I think about it the last time I had the VPN going the main office had 3 down 3 up Frame Relay and the seed office had like 8 down 1 up. DSL Currently, the seed office has 100 down 10 up and the main office has dedicated fiber 10 down 10 up @ $890 a Month with CenturyLink which is insane and there level of service is very Poor we looked at the contract and it's a 36-month contract and they are like 16 months in. If I read it right the eft if 6 months of service. Which is a lot But it could still be about a 6k savings vs finishing out the contract.
It's hard to comment on that because so many organizations have unbalanced speed needs. Otherwise, it would appear that 1Mbps speed is good enough in view of your successful use of 8 down / 1 up. But 1Mbps is SO much lower than what people are now used to having that it's likely to cause frustration. How long ago did the 8down/1up work well?
That is why I said it would save a ton of money. In terms of feasibility, it all depends on the data sizes that are being transmitted on the VPN. 100x10 could totally work...it all depends on overall bandwidth required.
The only way to know if this will work is to do the math on it! Run the calculations. What are they doing now to get data between the locations? Do you know the data sample size roughly? What type of data is going to be sent over?
Depending on their budget you could look into WXA (WAN Acceleration) & optimizers or SD-WAN solutions. With the former you are caching content which allows for greater throughput to be achieved and with the latter you are essentialy bundling a mixture of WAN connections together and through software forming one aggregate pipe of bandwidth.
The only way to know if this will work is to do the math on it! Run the calculations. What are they doing now to get data between the locations? Do you know the data sample size roughly? What type of data is going to be sent over?
Depending on their budget you could look into WXA (WAN Acceleration) & optimizers or SD-WAN solutions. With the former you are caching content which allows for greater throughput to be achieved and with the latter you are essentialy bundling a mixture of WAN connections together and through software forming one aggregate pipe of bandwidth.
You should call in the Centurylink rep to discuss your options. They probably have dedicated point to point services.
You also need an updated UTM (firewall) appliance.
A VPN is a good option if the bandwidth supports your needs. Otherwise not so much. If you are running a Terminal Server (Remote Desktop), then even a 10Mbps/10Mbps should work for a small remote office. As Fred stated, the weakest link is the upload speed, and limits the potential. So 100Mbps is a meaningless number for the VPN.
You also need an updated UTM (firewall) appliance.
A VPN is a good option if the bandwidth supports your needs. Otherwise not so much. If you are running a Terminal Server (Remote Desktop), then even a 10Mbps/10Mbps should work for a small remote office. As Fred stated, the weakest link is the upload speed, and limits the potential. So 100Mbps is a meaningless number for the VPN.
ASKER
Blue Street the bandwidth requirements are not the high, mostly just spreadsheets and small documents.
We are trying to get away from Centurylink as there level of service is going downhill fast.
I am looking at the SonicWalls TZ300 the basic one is like $450 but the one with the better security for 3 years is like $1300 may be a toughf sell to them. I am also looking at OPNsense & CloudOS for UTM soulutions. The 10 up should be fine where we ran into problems is with the less than 1 on dsl.
We are trying to get away from Centurylink as there level of service is going downhill fast.
I am looking at the SonicWalls TZ300 the basic one is like $450 but the one with the better security for 3 years is like $1300 may be a toughf sell to them. I am also looking at OPNsense & CloudOS for UTM soulutions. The 10 up should be fine where we ran into problems is with the less than 1 on dsl.
Blue Street the bandwidth requirements are not the high, mostly just spreadsheets and small documents.Then bandwidth should not matter nearly as much...office documents are tiny. Are they running AD DS between the two sites or anything else that may be more bandwidth intensive?
We are trying to get away from Centurylink as there level of service is going downhill fast.Good, check their agreement, it may have provisions that would allow you to break it early without penalty.
I am looking at the SonicWalls TZ300 the basic one is like $450 but the one with the better security for 3 years is like $1300 may be a toughf sell to them. I am also looking at OPNsense & CloudOS for UTM soulutions. The 10 up should be fine where we ran into problems is with the less than 1 on dsl.I sent a DM.
ASKER
Blue Street No they are not running an AD.
I started running JD Speedtest. "JackDinn" Set it to check every 30 minutes so far not really good for being a circuit.
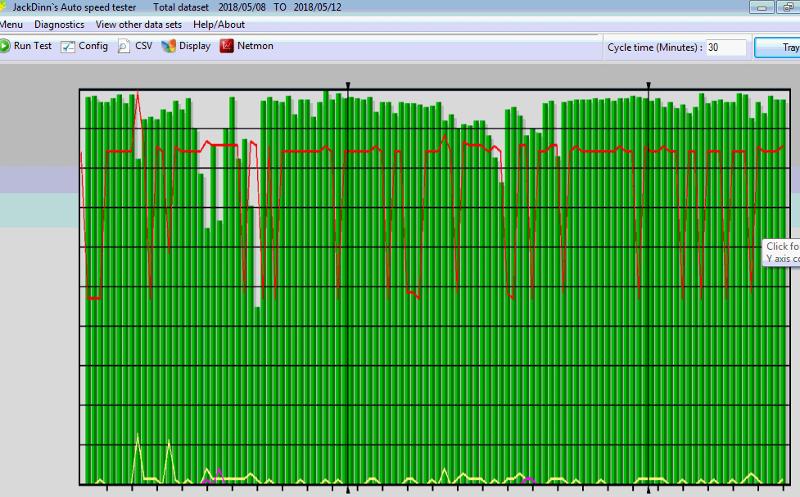 I was looking over the agreement the other day it's 85 pages long any idea of what section that might be in? That would be wonderful to be able to get out of it without an ETF.
I was looking over the agreement the other day it's 85 pages long any idea of what section that might be in? That would be wonderful to be able to get out of it without an ETF.
I started running JD Speedtest. "JackDinn" Set it to check every 30 minutes so far not really good for being a circuit.
 I was looking over the agreement the other day it's 85 pages long any idea of what section that might be in? That would be wonderful to be able to get out of it without an ETF.
I was looking over the agreement the other day it's 85 pages long any idea of what section that might be in? That would be wonderful to be able to get out of it without an ETF.
ASKER
Blue Street I don't see the DM do they hide it with me being a free member?
I was looking over the agreement the other day it's 85 pages long any idea of what section that might be in? That would be wonderful to be able to get out of it without an ETF.Yes, look for the Termination section. From there you should see Termination By or Cause for Termination as sub sections. Also, if they have an SLA (Service Level Agreement) it should be short and have the level of service they are guaranteeing and what will occur when they violate it.
ASKER
Very cool. I am going to E-mail him now for a copy of it.
ASKER
OK
My head hurts after trying to figure out this t&c But then i came across this part.
"(b) All Service Types—Cancellation After the Start of Service Date. If a Service is canceled by Customer other than for Cause, or by CenturyLink
for Cause, before the conclusion of its Initial Service Term, Customer will pay a “Cancellation Charge” equal to: (i) 100% of the balance of the MRCs
that otherwise would have become due for the unexpired portion of the first 12 months of the Initial Service Term, if any, plus (ii) 35% of the balance of
the MRCs that otherwise would have become due for the unexpired portion, if any, of the Initial Service Term beyond the first 12 months."
I read that to say if you are past the first 12 months then it's 35% or the remaining months MRC which would be about $311 a month for about 16 months left so about $4984.
The SLA is very short and not sure how to peruse the discounts from that or using it as a way out.
v70.pdf
CenturyLink-IQ-Networking-SLA.pdf
My head hurts after trying to figure out this t&c But then i came across this part.
"(b) All Service Types—Cancellation After the Start of Service Date. If a Service is canceled by Customer other than for Cause, or by CenturyLink
for Cause, before the conclusion of its Initial Service Term, Customer will pay a “Cancellation Charge” equal to: (i) 100% of the balance of the MRCs
that otherwise would have become due for the unexpired portion of the first 12 months of the Initial Service Term, if any, plus (ii) 35% of the balance of
the MRCs that otherwise would have become due for the unexpired portion, if any, of the Initial Service Term beyond the first 12 months."
I read that to say if you are past the first 12 months then it's 35% or the remaining months MRC which would be about $311 a month for about 16 months left so about $4984.
The SLA is very short and not sure how to peruse the discounts from that or using it as a way out.
v70.pdf
CenturyLink-IQ-Networking-SLA.pdf
ASKER
it's a 36 month agreement
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.