sbalawajder
asked on
CredSSP encryption oracle remediation
We have not made any changes to our GPOs, however, today upon attempting to remote desktop to a few servers we are getting the following error:
An Authentication error has occurred.
The function requested is not supported.
Remote computer: <servername>
This could be due to CredSSP encryption oracle remediation
Is there a patch I need to install on my servers to fix? Or is there a workaround for this message?
rdperror.png
An Authentication error has occurred.
The function requested is not supported.
Remote computer: <servername>
This could be due to CredSSP encryption oracle remediation
Is there a patch I need to install on my servers to fix? Or is there a workaround for this message?
rdperror.png
well shesh. How will I remotely update the server if I can't RDP to it. Way to go MS
Maybe use an unpatched client? Yet if you patch the server, how will unpatched clients react afterwards - will they be blocked that time around?
Some of our users have Win7 and started to have that issue today. I can tell that KB4103718 was installed earlier today so I truly beleive it is related to that.
However, when I try to uninstall that KB4103718, I get an error saying that it was not successfully uninstalled and it still show in the list of installed updates. Any idea?
However, when I try to uninstall that KB4103718, I get an error saying that it was not successfully uninstalled and it still show in the list of installed updates. Any idea?
If you can't update your servers since it requires a reboot, you could add this to your clients Registry, send it out via GPO and all it takes is that the clients get an reboot:
[HKEY_LOCAL_MACHINE\SOFTWA
[HKEY_LOCAL_MACHINE\SOFTWA
It is better to block those updates from your WSUS server.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
@Ryan Confoy thanks man! your a life saver.
Argh! Can't connect to my Hyper-V servers. That registry key, should that exist already on the clients? I only need to set it on mine for remote admin for now.
Nope, you will need to create both the CredSSP and Parameters , and then create the AllowEncryptionOracle dword and give it a value of 2, worked for me on both win7 and win10 freshly patched computers.
You have to update your windows clients and your AD servers. Make sure you apply this one in your server(s):
May 8, 2018
An update to change the default setting from Vulnerable to Mitigated.
May 8, 2018
An update to change the default setting from Vulnerable to Mitigated.
Also no reboot needed on the client with the Reg change. That is if you only need to accommodate a couple of PCs.
ASKER
Whats strange- I can remote connect to the server via a RDP connection from another server (which happens to be the AD machine)
I will be patching the server in question tonight, will let you know how it goes
I will be patching the server in question tonight, will let you know how it goes
I fired up a VM that didn't had that update installed yet and connected over RDP.
Thanks Ryan, you saved me from a world of pain!
I was having the same issue today (09 MAY 2018).
Uninstalling the latest Windows Update solved the problem. I didn't write down the KB[number], but I know that its not the 4093112.
Windows Update Settings > View Installed Update History > Unistall Updates
Windows 10, x64
Uninstalling the latest Windows Update solved the problem. I didn't write down the KB[number], but I know that its not the 4093112.
Windows Update Settings > View Installed Update History > Unistall Updates
Windows 10, x64
Same issue. Cant get in any of my server via rdp
If uninstalling the problematic client update does not work for you, give the registry key above a shot; I can confirm it worked for me. Thanks again for posting this.
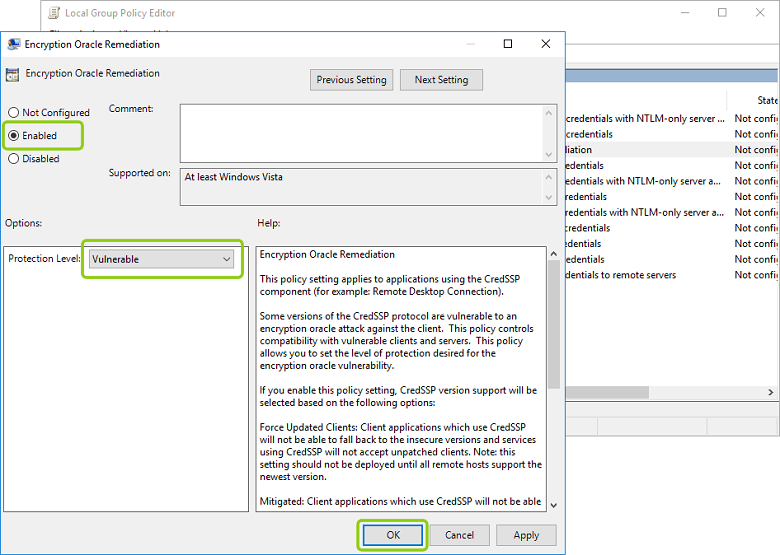
The registry value was not there on my windows 10 machine. I had to go to the following local group policy and apply the change on my client:
Computer Configuration -> Administrative Templates -> System -> Credentials Delegation--Encryption Oracle Remediation
enable and set to 'vulnerable'.
Computer Configuration -> Administrative Templates -> System -> Credentials Delegation--Encryption Oracle Remediation
enable and set to 'vulnerable'.
It typically will not be present if you're having this issue. You have to create the new keys "CredSSP" and "Parameters" in the above-referenced location before creating the DWORD.
Glad the local group policy approach worked for you as well.
Glad the local group policy approach worked for you as well.
My PC was ahead of my Azure server with these patches. I want to apply patches to the server to get it up to date. I have unpatched clients that I could use to access.
If my server is fully patched. Is there a possibility that I might not be able to log in with any client PCs?
Thanks!
If my server is fully patched. Is there a possibility that I might not be able to log in with any client PCs?
Thanks!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Reg Fix worked great. Thank you. Have this as an emergency backup. We have about 100 users that rely on RDS.
Reg Fix worked for us as well. Experts Exchange comes to the rescue again!!!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
this is just fucking bullshit i dont expect in 2018. what about the gateway/server side workaround for non-domain workstations without IT support to resolve? is there a patch that supersedes that can be pushed?
Thanks, this was fast as many of us woke up to this random affected computers nightmare. Thanks @Ryan Confoy
Can someone POST a complete solution for this?
The Remote Desktop App from the MS Store, appears to be un-affected. It's just the traditional Remote Desktop Connection (%windir%\system32\mstsc.e
See the following from Microsoft: Microsoft TechNet Article
I concur with @Mitch P-- This is a hurdle I thought that we had finally cleared with Microsoft and Patch Day. Unbelievable, but believable. Thanks MS.
Thank you for the diagnosis and solutions above, folks.
See the following from Microsoft: Microsoft TechNet Article
I concur with @Mitch P-- This is a hurdle I thought that we had finally cleared with Microsoft and Patch Day. Unbelievable, but believable. Thanks MS.
Thank you for the diagnosis and solutions above, folks.
For those wondering about what to do with machines not on the domain, use the following to create a .REG file (we call it CredSSP.REG):
If using Notepad make sure to name it "CredSSP.REG" with the quotes to keep the extension.
We put ours on a shared OneDrive location that we send the link to for anyone that needs it.
For uses running in Standard User Mode:
1: Click START
2: Type: Regedit
3: Right click and Run As Admin
4: Credential
5: FILE
6: IMPORT
7: Choose the CredSSP.REG file
8: Close the registry editor and reboot
NOTE: This is a mitigation step! Once the servers are up to date remove this registry entry!
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters]
"AllowEncryptionOracle"=dword:00000002If using Notepad make sure to name it "CredSSP.REG" with the quotes to keep the extension.
We put ours on a shared OneDrive location that we send the link to for anyone that needs it.
For uses running in Standard User Mode:
1: Click START
2: Type: Regedit
3: Right click and Run As Admin
4: Credential
5: FILE
6: IMPORT
7: Choose the CredSSP.REG file
8: Close the registry editor and reboot
NOTE: This is a mitigation step! Once the servers are up to date remove this registry entry!
SIDE NOTE: Microsoft released the server-side update two patch cycles ago (2 months) with plenty of warning.
We were bit because we have maintenance windows that span longer than that.
Make sure to update those servers!
We were bit because we have maintenance windows that span longer than that.
Make sure to update those servers!
No I agree, this is bullshit. In the last few months there have been a number of Microsoft Update 'surprise!' days. I still have clients getting a BSOD from KB4088875. Even after removing the update, when some users log out the system blue screens. Microsoft even ended up pulling the patch with no real explanation, and issued a new patch that did nothing to fix the damage caused.
I also experienced this problem from my now-patched Windows 10 x64 workstation. It was a cumulative update
May 8, 2018—KB4103727 (OS Build 16299.431)
https://support.microsoft.com/en-ca/help/4103727/windows-10-update-kb4103727
Another thing about Microsoft Updates - they often link back to link back links, weaving a web of confusion that I simply do not have time to try to decipher. If I had to read through every bulletin on every patch and update released by Microsoft I'd never get any work done.
Having ranted, it's also noted that RDP attacks have been ramping up a lot lately, so at least Microsoft is trying to address vulnerabilities. Always a silver lining somewhere if you look for it.
Personally I'm angling to have all my clients ditch RDP and switch to something more secure.
I also experienced this problem from my now-patched Windows 10 x64 workstation. It was a cumulative update
May 8, 2018—KB4103727 (OS Build 16299.431)
https://support.microsoft.com/en-ca/help/4103727/windows-10-update-kb4103727
Addresses an issue that may cause an error when connecting to a Remote Desktop server. For more information, see CredSSP updates for CVE-2018-0886.
Another thing about Microsoft Updates - they often link back to link back links, weaving a web of confusion that I simply do not have time to try to decipher. If I had to read through every bulletin on every patch and update released by Microsoft I'd never get any work done.
Having ranted, it's also noted that RDP attacks have been ramping up a lot lately, so at least Microsoft is trying to address vulnerabilities. Always a silver lining somewhere if you look for it.
Personally I'm angling to have all my clients ditch RDP and switch to something more secure.
Please Help, I follow the steps using regedit but i could not find CredSSP on HKLM and im using windows 10
Hi Richard, the CredSSP and Parameters keys aren’t actually there yet, you have to create them under the local machine hive. Give @Philip Elder‘s instructions above a shot if you’d rather not manually create the keys (the “folders” in the registry hive are called keys), he’s got it pretty well covered and the paths needed to import the keys are already present in the the file he provides.
Thanks @Ryan
Just remove latest Security update for Microsoft Windows KB4103721
[RDP] This could be due to CredSSP encryption oracle remediation
[RDP] This could be due to CredSSP encryption oracle remediation
Ryan Confoy ,
Greate it's working
Greate it's working
Hi All, the reg fix is working :)
Thanks all.
Thanks all.
ASKER
I ran the updates on my affected servers, and all is working now! I have a few other servers I need to install the updates on, but thats for Friday night
Thanks for your help guys
Thanks for your help guys
https://www.youtube.com/watch?v=hrqESgJaS9M
Just Uninstall Windows update KB4103727 from your Windows 10
Just Uninstall Windows update KB4103727 from your Windows 10
Updating the servers is the best way to resolve if you can restart them during the week. All my client workstations can now connect.
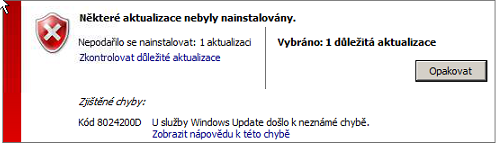
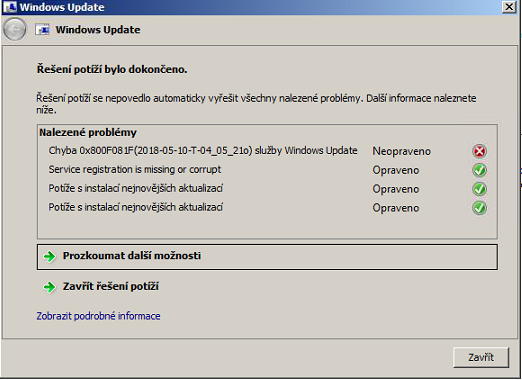
How abou that server cannot install that update. Running Win2k8 R2 standart. After downloading and installing patch I get an error. (ERROR: https://ctrlv.cz/cLcn ). After running windows update helper it gave me this result (result: https://ctrlv.cz/IslY ).
Also tried manual install and installation failed. Any advice?
Also tried manual install and installation failed. Any advice?
Go to this link https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2018-0886
Scroll down till you see the server you want, select "Security Update" to the right.
It will show several downloads. Download the appropriate software and install on the server. Mine was a 2016, installation took an hour for me.
It worked for me.
i tested the work around that was discussed above, creating the registry on the client computer, and it worked as well. I then deleted the registry, and it was back to the error. I installed the update from
the site above on the server, did not put the registry back on the client, and i was able to log on to the server thru RDP.
Scroll down till you see the server you want, select "Security Update" to the right.
It will show several downloads. Download the appropriate software and install on the server. Mine was a 2016, installation took an hour for me.
It worked for me.
i tested the work around that was discussed above, creating the registry on the client computer, and it worked as well. I then deleted the registry, and it was back to the error. I installed the update from
the site above on the server, did not put the registry back on the client, and i was able to log on to the server thru RDP.
Thank you!!!!
Not an IT pro - just a dumb accountant using a remote server....you saved me a LOT of trouble! Appreciate all the smart people out there who share their knowledge.
Not an IT pro - just a dumb accountant using a remote server....you saved me a LOT of trouble! Appreciate all the smart people out there who share their knowledge.
Thank you for your advice. I found security update which worked for me (11MB). Now is RDP working for users who have newest update installed.
But I can't still fully install hole update. Still seeing same errors after installing via windows update.
But I can't still fully install hole update. Still seeing same errors after installing via windows update.
NP,
You said "I found security update which worked for me", then "But I can't still fully install hole update. Still seeing same errors after installing via windows update" so i'm not sure what your saying,( that you can't install whole update on clients computers?)
i didn't have to install any updates on clients computers if that helps.
You said "I found security update which worked for me", then "But I can't still fully install hole update. Still seeing same errors after installing via windows update" so i'm not sure what your saying,( that you can't install whole update on clients computers?)
i didn't have to install any updates on clients computers if that helps.
I am still talking abou win server 2k8 r2 standart. For this machine I found update witch is 11MB but the hole update from Windows Update manager have 200MB+. This update from WU I am still not able to install.
This small update fixed my issue with RDP.
This small update fixed my issue with RDP.
For Windows Server 2016 download the full Cumulative Update and install on the Remote Desktop Session Hosts and Remote Desktop Gateway servers.
For Windows Server 2012 R2 download the latest Monthly Update and install on both RD Role sets.
Both require reboots.
We finished the last of our stragglers last night. No more CredSSP errors for remotely connecting systems.
For Windows Server 2012 R2 download the latest Monthly Update and install on both RD Role sets.
Both require reboots.
We finished the last of our stragglers last night. No more CredSSP errors for remotely connecting systems.
NOTE: There is no excuse for this. Microsoft released the updates on the server side two months ago with plenty of explanations about what was coming. In fact, they released iterative patches to clients as a warning over both months!
Complaining that it's Microsoft's fault that we're caught by the situation is not right.
It's our responsibility to stay on top of our I.T. Thus, we are the ones culpable, or the I.T. orgs supporting our systems are responsible, for keeping things up to date and regression testing all patches so as to be aware of what would blow up where.
Complaining that it's Microsoft's fault that we're caught by the situation is not right.
It's our responsibility to stay on top of our I.T. Thus, we are the ones culpable, or the I.T. orgs supporting our systems are responsible, for keeping things up to date and regression testing all patches so as to be aware of what would blow up where.
From the look at the MB size, it sounds like your talking about the monthly roll out. 2016 didn't have one, just the security update.
Not sure about 2008R2, i'm running several TS's with 2008R2 and haven't had an issue. I've only had a problem with 2016, i don't have 2012.
When you say you can't install, need a little more detail. Are you getting an error, is it saying it's not compatible, it won't open?
Not sure about 2008R2, i'm running several TS's with 2008R2 and haven't had an issue. I've only had a problem with 2016, i don't have 2012.
When you say you can't install, need a little more detail. Are you getting an error, is it saying it's not compatible, it won't open?
Dear Philip Elder
NOTE: There is no excuse for this. Microsoft released the updates on the server side two months ago with plenty of explanations about what was coming. In fact, they released iterative patches to clients as a warning over both months!
WHAT A TOTAL BULLCRAP! Sorry to say. But this is such so deep nonsense.
All of my server are up to date. Patched via wsus and aditionally checked via online search. Still
SOME of the servers wont let my fully patched client throug.
So dont blame any Sysadmin and this protecting microsoft is just so ridiculous.
I m looking since hours to resolve the issue with "patching the servers" and not with the group policy workaround.
On the servers i try to connect i cant find those updates that need to be installed. They are not there but its approved on wsus.
I tried to manually download them via Catalogue - getting the message that the updates is not designed for the system.
This is just absolute bullshit that Microsoft messed up. Sorry to say. But if its working in your environment, doesnt mean it works in others.
Still i followed ALL recommendations from microsoft and hundreds of blogs i actually read about it.
NOTE: There is no excuse for this. Microsoft released the updates on the server side two months ago with plenty of explanations about what was coming. In fact, they released iterative patches to clients as a warning over both months!
WHAT A TOTAL BULLCRAP! Sorry to say. But this is such so deep nonsense.
All of my server are up to date. Patched via wsus and aditionally checked via online search. Still
SOME of the servers wont let my fully patched client throug.
So dont blame any Sysadmin and this protecting microsoft is just so ridiculous.
I m looking since hours to resolve the issue with "patching the servers" and not with the group policy workaround.
On the servers i try to connect i cant find those updates that need to be installed. They are not there but its approved on wsus.
I tried to manually download them via Catalogue - getting the message that the updates is not designed for the system.
This is just absolute bullshit that Microsoft messed up. Sorry to say. But if its working in your environment, doesnt mean it works in others.
Still i followed ALL recommendations from microsoft and hundreds of blogs i actually read about it.
KB4103725 (Windows 8/10)
KB4103727 (Server 2016/2012)
KB4103718 (Windows 7)