managedsol
asked on
Unknown rogue SSL certificate being installed on domain machines
Hi All,
We have a wireless network that is secured by SSL. However, we’re having many domain member laptops unable to connect to the wireless network due to an unknown SSL certificate that is appearing on all domain machines, including domain servers.
The certificate presents itself published to an alpha numeric-ID, by another alpha numeric ID. There is no additional information that indicates the certificates purpose or origin.
I have uploaded a screenshot of the local computer personal cert. store.
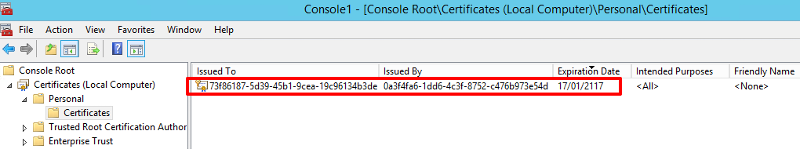
We have checked Group Policy and confirmed that the certificate is not being deployed using policy. Instead, it appears to be installed automatically on all domain member computers and servers.
If the certificate is removed, it appears again after the computer/server is restarted.
We believe it might be related to ADFS or Azure ADsync although we haven’t been able to locate those roles on any servers. We’ve seen a similar certificate on other client sites that use those services.
Does any one know a way in which we might be able to remove this certificate from being published / installed on the domain computer members?
We have a wireless network that is secured by SSL. However, we’re having many domain member laptops unable to connect to the wireless network due to an unknown SSL certificate that is appearing on all domain machines, including domain servers.
The certificate presents itself published to an alpha numeric-ID, by another alpha numeric ID. There is no additional information that indicates the certificates purpose or origin.
I have uploaded a screenshot of the local computer personal cert. store.

We have checked Group Policy and confirmed that the certificate is not being deployed using policy. Instead, it appears to be installed automatically on all domain member computers and servers.
If the certificate is removed, it appears again after the computer/server is restarted.
We believe it might be related to ADFS or Azure ADsync although we haven’t been able to locate those roles on any servers. We’ve seen a similar certificate on other client sites that use those services.
Does any one know a way in which we might be able to remove this certificate from being published / installed on the domain computer members?
ASKER
Thanks Dr Klahn. I've updated the question with the imbedded image. I had thought I had uploaded the screenshot as an attachment. But the screenshot is there now.
Re - Event logs. I've cleared the logs, removed the certificate from an affected machine. Restarted and reviewed, but cannot find any mention of the installation. Is there a particular event that I can filter by?
Re - Event logs. I've cleared the logs, removed the certificate from an affected machine. Restarted and reviewed, but cannot find any mention of the installation. Is there a particular event that I can filter by?
You did not include all the columns. Can you export and paste as text?
What is under details tab?
What is under details tab?
ASKER
There is no additional data in the remaining columns, which is why I didn't include them. However, this is a screenshot from another machine, as the original one wasn't available. The same certificate which contains same "issued by" and properties, exists on all the domain machines, so I don't think it will matter that the example isn't taken from the original machine as in my original post.
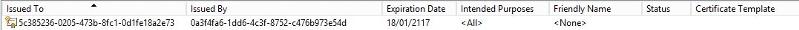
The text of the certificate properties is below.
The text of the certificate properties is below.
X509 Certificate:
Version: 1
Serial Number: f1c042eef153bc8148702ced5073c820
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=0a3f4fa6-1dd6-4c3f-8752-c476b973e54d
Name Hash(sha1): 49a5eabcd831b1b6ebe368d046250280c6e2dd55
Name Hash(md5): 708ecca574f5688438a99ae73b356b88
NotBefore: 18/01/2017 2:33 AM
NotAfter: 18/01/2117 3:33 AM
Subject:
CN=5c385236-0205-473b-8fc1-0d1fe18a2e73
Name Hash(sha1): 3cafe55ee495c207b1a590fe212cf559f01b14f6
Name Hash(md5): c9662dff95af5e32c5c1ea16fae5f1a5
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 b0 de de 8c a2 8c 2b
0010 18 10 93 b5 76 20 38 a9 19 26 d6 4e 9a 08 f8 c0
0020 2b cb d9 67 6e 18 2b 90 b5 1d 4d 62 4d 5a c8 e5
0030 f0 81 71 52 6f 09 7e 3f f9 f7 7b 8a de f1 b3 79
0040 ba 36 de 03 0f b8 c1 4e 1b 1a 84 7a f2 e0 93 e0
0050 e3 1f e4 a6 55 c8 7e ab 9b 0f 22 35 a2 f2 cd 06
0060 e3 ba 1c 37 47 30 44 de e6 aa 4f c0 4a 1b 8d 5d
0070 7b 77 a4 24 f6 1a 23 f4 b2 dc 29 63 65 fb c2 e0
0080 b4 9c ed f0 c0 f4 2a c1 be 78 df c9 89 8c 70 41
0090 f8 77 b8 ff d5 b0 0d b1 8a 9e 3d 78 0c 94 81 d8
00a0 f5 50 ab a1 1a 3e 79 1a 85 f4 d6 c9 a3 88 79 65
00b0 1e 01 5b 9d 33 19 2b 01 de d4 89 50 dc d6 0e 9e
00c0 2c 2d b4 4b f2 42 d8 44 51 b9 31 0b 82 62 a6 f6
00d0 0d f6 a5 80 f3 46 9b af f8 dd f4 33 c8 a9 13 2e
00e0 3e ef 57 2f e5 04 03 0f 8b 0a 75 4b 25 5c e2 91
00f0 7b e6 53 ac fe ef cb ce b2 ad 75 9e 38 6d 66 00
0100 43 fb f8 f4 e2 fa 08 7a d7 02 03 01 00 01
Certificate Extensions: 0
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 57 96 d6 99 9f 49 26 c6 01 2c 2c 5b b7 9e 81 d7
0010 5e 5a f6 95 ee d5 22 63 0b b6 57 a9 1e db c2 f9
0020 86 4c 1e 0e af 2a ca 9f be be 08 a5 7a f3 88 74
0030 5c a1 17 62 a1 d7 99 2d 6a b5 29 1d f0 03 e0 72
0040 0c ea 00 f1 58 d0 f0 d6 67 a8 d4 85 89 c4 97 67
0050 89 c2 0e 6f 8a 04 d9 9f 9a bd b0 48 46 9a f7 70
0060 72 a4 4b 9b e4 51 a6 03 17 20 0d 6d 22 4b 39 7a
0070 c6 ca 84 b8 06 f5 3e aa 71 24 0c f8 64 d8 56 74
0080 f9 7b 89 df 50 ac 59 61 e6 3a ae a7 1a 9e b9 97
0090 c8 a4 f3 10 fc cd ba 2e aa 6f e5 a6 f4 85 fa 3c
00a0 f8 63 2d dc 5d 6a a2 01 7e 52 c4 e4 d3 73 50 78
00b0 ab fd 8d c6 c6 7e f0 40 18 2e 26 d3 cf 99 78 9d
00c0 5d 65 10 e1 07 00 a1 f9 9d be bb d4 fe 30 85 e6
00d0 dd 7e 4f 74 d5 5b 31 b5 15 c1 a0 0a 40 73 ee c3
00e0 36 73 0b 32 ae 45 12 c1 ef 89 e5 8b 35 bd 9c 39
00f0 d3 84 70 1f 27 f9 13 4b fa 0a 1f ab 7d 94 2d 58
Non-root Certificate
Key Id Hash(rfc-sha1): 5f 5b 7c 0b 1b c2 ec 76 b1 4f 08 ff cc 87 6c 79 8c 63 03 5c
Key Id Hash(sha1): b3 3f 18 01 47 90 e4 73 2f 32 15 6b 3a 12 a2 03 a7 82 54 3c
Key Id Hash(md5): 1685beda26c016bfbcb3d2d721a6f47b
Key Id Hash(sha256): f5ee97403c63f0f6edfc300dd19ed417b5c0252c9c88f512372048fcbe3c3273
Cert Hash(md5): 0e c8 a5 bc 64 c9 c8 17 e3 e5 4a bf 73 e8 9b 07
Cert Hash(sha1): b2 09 d5 f0 cc 08 f5 21 eb 36 db 0c 1b dc 56 40 3a e4 3e 4c
Cert Hash(sha256): be9f01aaf298e469a102c3395948f7f6cc711c178e3f4559b5581a96724d59ff
Signature Hash: 1ff70cbe7147b000b4b895243d5147db4b6ccc9da6ecafaf2b7e81d912831118
CertUtil: -dump command completed successfully.ASKER
No suggestions?
Is there a way of identifying how this certificate is being deployed? In AD?
Is there a way of identifying how this certificate is being deployed? In AD?
You can check RSOP etc. with the process in this article
https://www.experts-exchange.com/articles/29415/How-to-find-Active-Directory-Group-Policy-GPO-that-applies-a-particular-setting.html
https://www.experts-exchange.com/articles/29415/How-to-find-Active-Directory-Group-Policy-GPO-that-applies-a-particular-setting.html
ASKER
Thanks Shaun Vermaak.
The certificate isn't being deployed by group policy. I've performed rsop and gpresult, and reviewed. I've also manually checked the GPO's linked to the OU's that contain the machine accounts.
I've tried creating new OU's without any linked GPO's except Default Domain Policy and moving affected machines into it. Removed the certificate, rebooted the machine, and the certificate appears after the reboot.
It's driving me nuts.
The certificate isn't being deployed by group policy. I've performed rsop and gpresult, and reviewed. I've also manually checked the GPO's linked to the OU's that contain the machine accounts.
I've tried creating new OU's without any linked GPO's except Default Domain Policy and moving affected machines into it. Removed the certificate, rebooted the machine, and the certificate appears after the reboot.
It's driving me nuts.
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
Click the "picture" icon between CODE and ? at the top of the text window and use that to upload the image.
Is there an Event Log entry indicating when the certificate was installed? If so, the complete entry may indicate who installed it.