Cisco Switch Security
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
What I am saying is if a user plugs a Switch to the Network , let 's say unmanageable Switch, what can this cause as damage ?
See my comments above.
ASKER
I don't get it..
Regarding man in the middle attack, I do not think it applies here.
The user PC is connected to the Switch with or without the Unmanaged switched.
I just want to know when a scenario like the one shown in the topology above, where SW port e0/0 will have 2 Mac Addresses in its table. What is the Security breach there ?
Regarding man in the middle attack, I do not think it applies here.
The user PC is connected to the Switch with or without the Unmanaged switched.
I just want to know when a scenario like the one shown in the topology above, where SW port e0/0 will have 2 Mac Addresses in its table. What is the Security breach there ?
People invite attacks in (dodgy links)
Secure routers keep uninvited attacks out.
Those are the two main items
Secure routers keep uninvited attacks out.
Those are the two main items
Either H1 or H2 can sniff packets on the wire that do not belong to them. They can craft packets to implement a MiTM attack.
Unless you configure switchport security to restrict MAC addresses learned on a specific interface, you should not have problems with MACs.
Unless you configure switchport security to restrict MAC addresses learned on a specific interface, you should not have problems with MACs.
I do not see this much at all . Inside clients behave themselves and outside attackers are kept.
Do not rely only on technology to secure yourself
Do not rely only on technology to secure yourself
ASKER
Either H1 or H2 can sniff packets on the wire that do not belong to them. They can craft packets to implement a MiTM attack.
Cannot users on H1 and H2 sniff packets if they are connected directly to the switch (separate ports) without the Unmanaged switch in the middle ?
Yes, but the unmanaged device acts like a hub. The managed switch can be configured with private vlan edging to prevent such sniffs.
ASKER
Yes, but the unmanaged device acts like a hub
I do not think this has security violation. Probably users will not have the desired performance, as both PCs will be connected to one single Switch port , but I do not see from security standpoint what can be impacted.
Make sure you have a commercial router as the way in. Update the firmware on this and keep it updated.
No operating systems lower than Windows 7 and then update BIOS and Chipset on all machines. Keep Windows Up to Date.
Train users not to open emails from strangers or click on dodgy links.
Have top notch spam control.
This will control the vast majority of your problems.
No operating systems lower than Windows 7 and then update BIOS and Chipset on all machines. Keep Windows Up to Date.
Train users not to open emails from strangers or click on dodgy links.
Have top notch spam control.
This will control the vast majority of your problems.
Your refusal to see the impact does not negate the possibility. I think I have clarified the possible attack vectors possible with the setup. You may proceed with what you desire.
Yes, but the unmanaged device acts like a hubNot true. Unmanaged switches behave the same way as managed switches, but missing some other options that managed devices have. Only hubs ack like hubs. ;) It has nothing to do with managed or unmanaged.
ASKER
OK, I probably understand where the security fear is :
---- scenario 1:
I have each Computer is connected to one separate Port on the Switch (Cisco Managed Switch), this is most common in every environment.
2 separate ports means 2 separate broadcast domains.
Traffic can be secure .
Scenario 2:
I have each computer (let's take 2 PCs) is connected to non-managed switch, and the non-managed switch is connected to Cisco Switch( Cisco Managed Switch)
Why Scenario 2 is not recommended?
I see the performance could be degraded as one link serves 2 PCs
I see there could be one user sniffing the traffic of the other, since when the traffic gets to the Non-managed switch it stays unseparated.(one Broadcast domain).
---- scenario 1:
I have each Computer is connected to one separate Port on the Switch (Cisco Managed Switch), this is most common in every environment.
2 separate ports means 2 separate broadcast domains.
Traffic can be secure .
Scenario 2:
I have each computer (let's take 2 PCs) is connected to non-managed switch, and the non-managed switch is connected to Cisco Switch( Cisco Managed Switch)
Why Scenario 2 is not recommended?
I see the performance could be degraded as one link serves 2 PCs
I see there could be one user sniffing the traffic of the other, since when the traffic gets to the Non-managed switch it stays unseparated.(one Broadcast domain).
I see this as well, and did see it. But you need compromised machines inside, an insecure network entrance and a skilled hacker outside.
Secure all your stuff and such attacks as described are much less likely.
Secure all your stuff and such attacks as described are much less likely.
2 separate ports means 2 separate broadcast domains.No. Two separate ports means separate collision domains. If ports are in the same VLAN (on unmanaged switch that would always be the case) ports belong to the same broadcast domain, however, unmanaged switch (like any other switch) maintaining MAC table, so unicast traffic destined to host with some specific MAC address will be forwarded only to that port. Traffic sniffing can only happen if MAC overflow attack is successfully issued and switch starts to act like hub (it does not matter is switch managed or unamanaged).
Why Scenario 2 is not recommended?That can be part of security requirements or security policies, but, generally it is still switch and there is no problem by itself. But the problem is - you can't control that switch and check what is going on that specific switch - trust boundary in that case is moved to upstream switch.
JustinCase, you seem to be going back on what you stated earlier - " Only hubs ack like hubs. ;) It has nothing to do with managed or unmanaged. "
The question about security begins with an assumption that you are compromised. An unmanaged switch is an easy prey for compromise, and was at the forefront of my thoughts as stated above.
The question about security begins with an assumption that you are compromised. An unmanaged switch is an easy prey for compromise, and was at the forefront of my thoughts as stated above.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you all Guys for your insights
Thanks. Good luck!
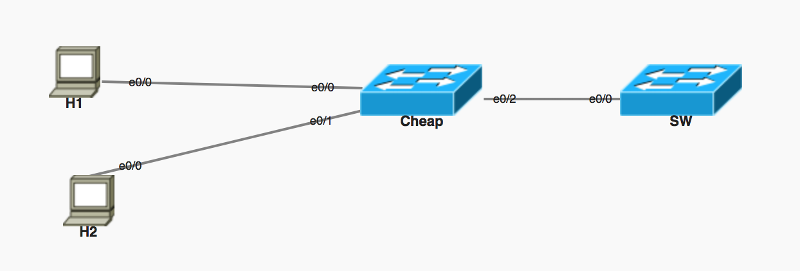
I do not use cheap switches for quality reasons.