wordpress may have virus
I noticed a many new .php files on my shared linux server that I did not create
Some php files had eval command.
I would want to delete this domain but I dont want to ruin the wordpress installation that is already there.
Which files/folders do not belong in a wordpress that has been installed in past year.
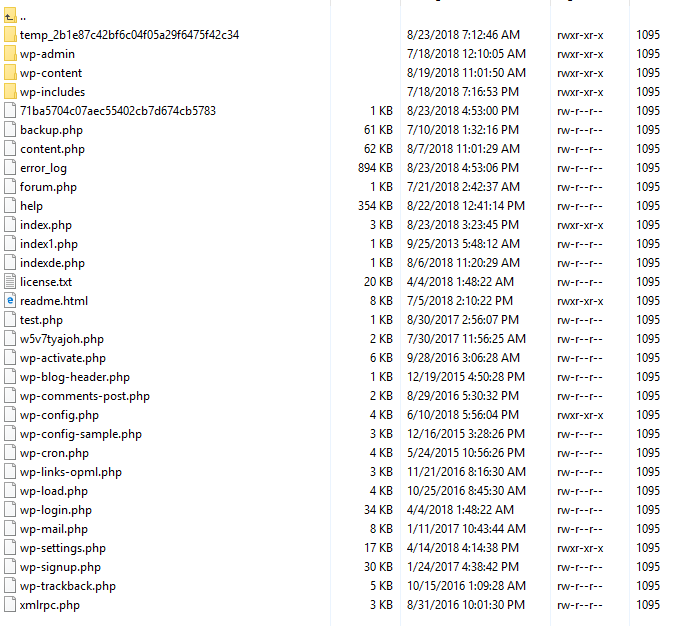
Some php files had eval command.
I would want to delete this domain but I dont want to ruin the wordpress installation that is already there.
Which files/folders do not belong in a wordpress that has been installed in past year.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Terry Woods.