Outlook Clients continue to ask for Cert to be installed Exchange 2016
Exchange 2016 CU9 DAG 2 Node
Windows 2016 DataCenter
Outlook 2012/2016 clients.
After installing my DigiCert cert for Exchange my clients still keep asking to install the certificate
I continue to install the cert but every time we restart outlook i asks the same question
any ideas
certissue1.PNG
certissue2.PNG
Windows 2016 DataCenter
Outlook 2012/2016 clients.
After installing my DigiCert cert for Exchange my clients still keep asking to install the certificate
I continue to install the cert but every time we restart outlook i asks the same question
any ideas
certissue1.PNG
certissue2.PNG
ASKER
Tim
It is installed on the exchange server correctly the helped me on the phone as I created the cert.
If client gets a different message
Some get the red x on the top message others get that as a green check
The second line all have green check
The third line some have a green check and other have a red check
Thoughts
Tom
It is installed on the exchange server correctly the helped me on the phone as I created the cert.
If client gets a different message
Some get the red x on the top message others get that as a green check
The second line all have green check
The third line some have a green check and other have a red check
Thoughts
Tom
oh ok. if this was done during business hours just allow time for outlook to pick up the new cert.
ASKER
Tim
This have been going on for several weeks now
How long does it take outlook to pick up the cert?
I even tried manually added the cert to the desktop using MMC
It shows cert is installed
I am thinking it is something else?
Thanks
Tom
This have been going on for several weeks now
How long does it take outlook to pick up the cert?
I even tried manually added the cert to the desktop using MMC
It shows cert is installed
I am thinking it is something else?
Thanks
Tom
have you assigned the services to the certs. it doesnt take that long.
also do you have multiple exchange servers did you add the cert to all of the servers, and did you delete the old expired cert?
ASKER
Tim
Yes two Exchanges Servers this is a DAG with two Nodes.
Only have one cert and that is installed on both servers
Both servers have 4 other certs but the are all self signed certs the same on both and the are still al valid
I think this might be the issue.
On Node 2 the Cert is not assigned to any services and it is the primary Node at the moment.
Am i on the right track ?
If so is there a command line to assign the same roles as node 1?
Thanks
Tom
certissue3.PNG
certissue4.PNG
Yes two Exchanges Servers this is a DAG with two Nodes.
Only have one cert and that is installed on both servers
Both servers have 4 other certs but the are all self signed certs the same on both and the are still al valid
I think this might be the issue.
On Node 2 the Cert is not assigned to any services and it is the primary Node at the moment.
Am i on the right track ?
If so is there a command line to assign the same roles as node 1?
Thanks
Tom
certissue3.PNG
certissue4.PNG
You need to assign the services to on all the exchange servers. Just go into the EAC and assign the services to the cert. The self-signed certs are fine, but you need to assign the services to the digicert cert. That will fix your issue.
ASKER
Tim
Added the same services as Node1 on Node 2
I went to a workstation running outlook 2016 close it started it I got both messages so on message 1 I clicked on do not show this again and hit allow.
The second one I installed the cert again.
I closed outlook and started again and this time no cert messages
I will continue to test over the weekend with the other client.
Stand by for my results.
Thanks for you help
Added the same services as Node1 on Node 2
I went to a workstation running outlook 2016 close it started it I got both messages so on message 1 I clicked on do not show this again and hit allow.
The second one I installed the cert again.
I closed outlook and started again and this time no cert messages
I will continue to test over the weekend with the other client.
Stand by for my results.
Thanks for you help
you should be good now.
ASKER
Tim
My clients are all getting this now
At least they are getting the same error now.
Any ideas?
Thank you,
Tom
certissue5.PNG
My clients are all getting this now
At least they are getting the same error now.
Any ideas?
Thank you,
Tom
certissue5.PNG
That is because your outlook clients are connecting to a name space that is not on your cert. Run the below and let me know the results. you will need to run this on both servers.
$Server = "exchange server name"
Get-OutlookAnywhere –Server $Server | ft Internalhostname, Externalhostname
Get-OWAVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-ECPVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-OABVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-ActiveSyncVirtualDirec
Get-WebServicesVirtualDire
Get-MapiVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-ClientAccessServer | select identity,autodiscoverservi
Looking specifically at the results from outlook anywhere, MAPI, and client access server, does your SSL cert have the names space listed that these virtual directories show?
$Server = "exchange server name"
Get-OutlookAnywhere –Server $Server | ft Internalhostname, Externalhostname
Get-OWAVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-ECPVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-OABVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-ActiveSyncVirtualDirec
Get-WebServicesVirtualDire
Get-MapiVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
Get-ClientAccessServer | select identity,autodiscoverservi
Looking specifically at the results from outlook anywhere, MAPI, and client access server, does your SSL cert have the names space listed that these virtual directories show?
ASKER
Tim
Node 1
My SANs from DigiCert
Thoughts? DNS? maybe?
Node 1
[[PS] C:\Windows\system32>$Server = "TGCS021-N1"
[PS] C:\Windows\system32>Get-OutlookAnywhere -Server $Server | ft Internalhostname, Externalhostname
InternalHostname ExternalHostname
---------------- ----------------
webmail.tgcsnet.com webmail.tgcsnet.com
[PS] C:\Windows\system32>Get-OWAVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/owa https://webmail.tgcsnet.com/owa
[PS] C:\Windows\system32> Get-ECPVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/ecp https://webmail.tgcsnet.com/ecp
[PS] C:\Windows\system32>Get-OABVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/oab https://webmail.tgcsnet.com/oab
[PS] C:\Windows\system32>Get-ActiveSyncVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/Microsoft-Server-ActiveSync https://webmail.tgcsnet.com/Microsoft-Server-ActiveSync
[PS] C:\Windows\system32>Get-WebServicesVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/EWS/Exchange.asmx https://webmail.tgcsnet.com/EWS/Exchange.asmx
[PS] C:\Windows\system32>Get-MapiVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/mapi https://webmail.tgcsnet.com/mapi
[PS] C:\Windows\system32>Get-ClientAccessServer | select identity,autodiscoverserviceinternaluri
WARNING: The Get-ClientAccessServer cmdlet will be removed in a future version of Exchange. Use the
Get-ClientAccessService cmdlet instead. If you have any scripts that use the Get-ClientAccessServer cmdlet, update them
to use the Get-ClientAccessService cmdlet. For more information, see http://go.microsoft.com/fwlink/p/?LinkId=254711.
Identity AutoDiscoverServiceInternalUri
-------- ------------------------------
TGCS021-N1 https://autodiscover.tgcsnet.com/autodiscover/autodiscover.xml
TGCS021-N2 https://autodiscover.tgcsnet.com/autodiscover/autodiscover.xml
[PS] C:\Windows\system32>/code]
Node 2
[code][PS] C:\Windows\system32>$Server = "TGCS021-N2"
[PS] C:\Windows\system32>Get-OutlookAnywhere -Server $Server | ft Internalhostname, Externalhostname
Creating a new session for implicit remoting of "Get-OutlookAnywhere" command...
InternalHostname ExternalHostname
---------------- ----------------
webmail.tgcsnet.com webmail.tgcsnet.com
[PS] C:\Windows\system32>Get-OWAVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/owa https://webmail.tgcsnet.com/owa
[PS] C:\Windows\system32>Get-ECPVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/ecp https://webmail.tgcsnet.com/ecp
[PS] C:\Windows\system32>Get-OABVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/oab https://webmail.tgcsnet.com/oab
[PS] C:\Windows\system32>Get-ActiveSyncVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/Microsoft-Server-ActiveSync https://webmail.tgcsnet.com/Microsoft-Server-ActiveSync
[PS] C:\Windows\system32>Get-WebServicesVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/EWS/Exchange.asmx https://webmail.tgcsnet.com/EWS/Exchange.asmx
[PS] C:\Windows\system32>Get-MapiVirtualDirectory -Server $Server | ft InternalURL, ExternalURL
InternalUrl ExternalUrl
----------- -----------
https://webmail.tgcsnet.com/mapi https://webmail.tgcsnet.com/mapi
[PS] C:\Windows\system32>Get-ClientAccessServer | select identity,autodiscoverserviceinternaluri
WARNING: The Get-ClientAccessServer cmdlet will be removed in a future version of Exchange. Use the
Get-ClientAccessService cmdlet instead. If you have any scripts that use the Get-ClientAccessServer cmdlet, update them
to use the Get-ClientAccessService cmdlet. For more information, see http://go.microsoft.com/fwlink/p/?LinkId=254711.
Identity AutoDiscoverServiceInternalUri
-------- ------------------------------
TGCS021-N1 https://autodiscover.tgcsnet.com/autodiscover/autodiscover.xml
TGCS021-N2 https://autodiscover.tgcsnet.com/autodiscover/autodiscover.xml
[PS] C:\Windows\system32>My SANs from DigiCert
Certificate Type Multi-Domain SSL
Common Name tgcsnet.com ( Check Installation)
SANs tgcsnet.com
webmail.tgcsnet.com
mail.tgcsnet.com
autodiscover.tgcsnet.com
tgcs021-n1.our.network.tgcsnet.com Thoughts? DNS? maybe?
That looks good. Maybe DNS. Do you have 2 internal DNS records for autodiscover pointing to both of your exchange servers? If not, create 2 internal DNS autodiscover A records and point them to the servers.
autodiscover.tgcsnet.com point to internal IP of first server
autodiscover.tgcsnet.com point to internal IP of second server
allow for AD DNS replication.
autodiscover.tgcsnet.com point to internal IP of first server
autodiscover.tgcsnet.com point to internal IP of second server
allow for AD DNS replication.
ASKER
Tim
I have two Windows 2012 R2 Servers as DC's both running internal DNS servers
Here is my DNS records for this
They are SRV records
dns3.PNG
I have two Windows 2012 R2 Servers as DC's both running internal DNS servers
Here is my DNS records for this
They are SRV records
dns3.PNG
I believe that is the issue. I have never used a srv for autodiscover. your clientaccessseever name space doesnt match so outlook is giving that error. I would have used a normal A record because you can match that name space. since you are using the srv record and I have never used that method, I'm completely sure on how to tell you to fix it, but I'm pretty sure that is the issue.
you can test by removing the SCP since you have a srv autodiscover record. run the following and remove the SCP since outlook looks at the srv record instead.
Set-ClientAccessServer –Identity ServerName -AutoDiscoverSe
you will need to remove it from both servers. that may fix your issue because outlook will not look at SCP record, yours look at srv.
Set-ClientAccessServer –Identity ServerName -AutoDiscoverSe
you will need to remove it from both servers. that may fix your issue because outlook will not look at SCP record, yours look at srv.
ASKER
I would first try to clear the SCP first because you can always change it back. leave the srv. you will need to restart IIS
If you still get the error then you can remove the SRV and create the A records for the SCP, but still restart IIS even if you remove the srv record and use the SCP.
Also looking at your screen shot, don't use the underscord (_) just use autodiscover, and create 2 of them with each pointing to one of the exchange servers.
If you choose to go this route anyway.
If you choose to go this route anyway.
ASKER
Tim
Created two A records on my internal DNS servers and I am still getting the popup message about the server
The third line has the error. red X on it
Thoughts.
Created two A records on my internal DNS servers and I am still getting the popup message about the server
The third line has the error. red X on it
Thoughts.
did you remove the SRV records?
also the 2 DNS autodiscover records is that exact name on your cert, like autodiscover.domain.com
you are not using local host files are you?
also the 2 DNS autodiscover records is that exact name on your cert, like autodiscover.domain.com
you are not using local host files are you?
Can you show me the A record you created?
ASKER
Tim
Yes in my cert the name matches hope it is not case sensitive? My SANs in the certs was posted in this thread.
image attached of the A Records.
I did not delete the srv records
What is the difference with _autodiscover and just autodiscover?
dns5.PNG
Yes in my cert the name matches hope it is not case sensitive? My SANs in the certs was posted in this thread.
image attached of the A Records.
I did not delete the srv records
What is the difference with _autodiscover and just autodiscover?
dns5.PNG
you need to delete those srv records, or try my recommendation of clearing the SCP with the cmdlets I sent.
ASKER
Tim
Just deleted the SRV records and checked on both DNS Servers they are now gone.
How long before I can check my outlook clients?
Just deleted the SRV records and checked on both DNS Servers they are now gone.
How long before I can check my outlook clients?
wait for AD replication and also restart IIS.
ASKER
Tim
I will wait for awhile to restart IIS
I will wait for awhile to restart IIS
that's fine
ASKER
Tim
Just restarted IIS on my of my clients I closed out look and started it up again
Same results 'security Alert' The name of the security certificate is invalid or does not match the name of the site RED X
Any ideas?
Maybe I did not wait long enough?
Just restarted IIS on my of my clients I closed out look and started it up again
Same results 'security Alert' The name of the security certificate is invalid or does not match the name of the site RED X
Any ideas?
Maybe I did not wait long enough?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
After you try that let me know and there is something else I would like you to check.
If it's still failing test the configuration settings, so open outlook and on the outlook icon in the lower right corner do the following:
Hold the ctrl key and right click the outlook icon, and select Test email auto-configuration and test with the options I have selected and he know the results of the log. See my screenshot:
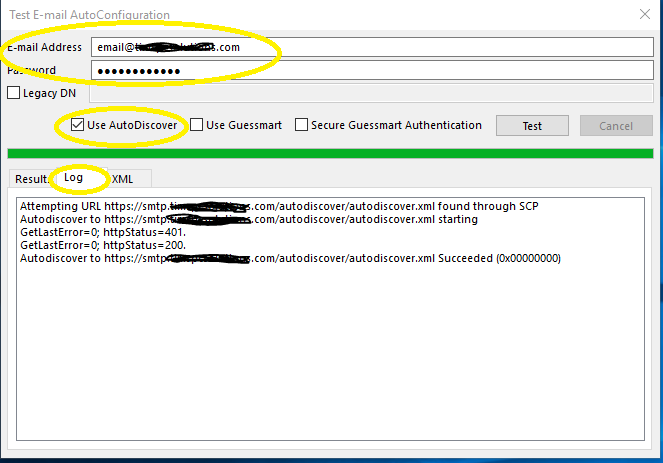
Hold the ctrl key and right click the outlook icon, and select Test email auto-configuration and test with the options I have selected and he know the results of the log. See my screenshot:
ASKER
Tim
After all the changes to DNS and recreating all users profile in outlook the problem seems to have bee corrected
Thank you
Tom
After all the changes to DNS and recreating all users profile in outlook the problem seems to have bee corrected
Thank you
Tom
Good deal.
the second error I would suggest getting instructions from digicert site on installing the cert correctly to exchange.