Implementing SSL with redirects
I am hosting a couple of web sites on couple Linux boxes and OWA on a Windows box in my office. Currently http is forwarded to Host_W and https is forwarded to Host_M. Host_W serves pages for www.site-m.biz, www.site-d.net, and www.site-f.com while it forwards requests for host_l.site-s.org and www.site-s.org to Host_L. The current structure looks like this:
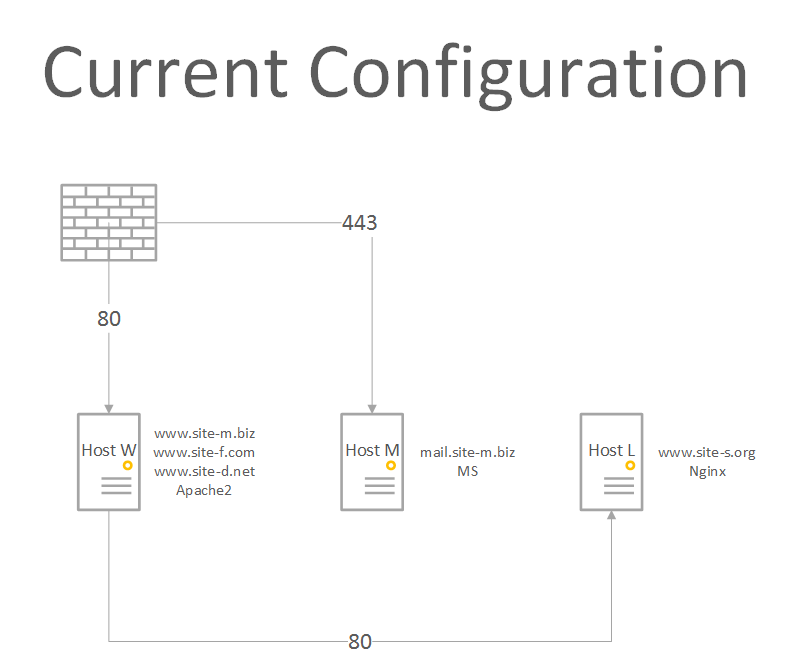
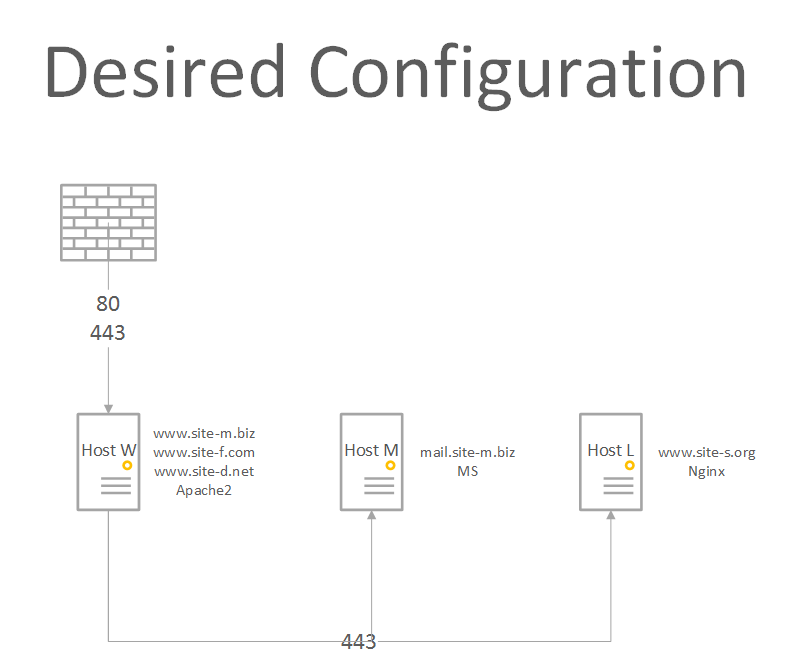
What I want to do is forward both http and https to Host_W while serving the same three sites and forward https requests for mail.site-m.biz to Host_M and requests for site-s.org to Host_L. The structure would look something like:
I have attached sanitized copies of what I think are the relevant config files.
The port forward is not a problem, simple change on the firewall. Installing Let's Encrypt certificate on both Nginx and Apache2 are heavily documented and a Godaddy certificate for mail.site-m.biz is already installed on Host-M.
What I don't have a handle on is the changes needed on the Apache2 on Host_W. I think it would be just to add something to the site-m.biz.conf like (and something similar to site-l.org.conf):
I found the above at Server Fault and removed the SSLCertificateFile and SSLCertificateKeyFile directives as the certificate for mail.site-m.biz is not installed on Host-W.
Do I need to install the certificate from Host-M for mail.site-m.biz on Host-W? If so would I add the SSLCertificateFile and SSLCertificateKeyFile directives?
Host_L---default.txt
site-s.org.conf.txt
site-m.biz.conf.txt

What I want to do is forward both http and https to Host_W while serving the same three sites and forward https requests for mail.site-m.biz to Host_M and requests for site-s.org to Host_L. The structure would look something like:

I have attached sanitized copies of what I think are the relevant config files.
The port forward is not a problem, simple change on the firewall. Installing Let's Encrypt certificate on both Nginx and Apache2 are heavily documented and a Godaddy certificate for mail.site-m.biz is already installed on Host-M.
What I don't have a handle on is the changes needed on the Apache2 on Host_W. I think it would be just to add something to the site-m.biz.conf like (and something similar to site-l.org.conf):
<VirtualHost *:443>
ServerName mail.site-m.biz
SSLEngine On
SSLProxyEngine On
ProxyRequests Off
SSLProxyCheckPeerCN off
SSLProxyCheckPeerName off
SSLProxyCheckPeerExpire off
SSLInsecureRenegotiation on
SSLProxyVerify none
SSLVerifyClient none
ProxyPass / https://mail.site-m.biz/
ProxyPassReverse / https://mail.site-m.biz/
<Location "/">
Require all granted
</Location>
</VirtualHost>I found the above at Server Fault and removed the SSLCertificateFile and SSLCertificateKeyFile directives as the certificate for mail.site-m.biz is not installed on Host-W.
Do I need to install the certificate from Host-M for mail.site-m.biz on Host-W? If so would I add the SSLCertificateFile and SSLCertificateKeyFile directives?
Host_L---default.txt
site-s.org.conf.txt
site-m.biz.conf.txt
Having difficulty untangling what you are after.
You can setup a reverse proxy that will see the http, HTTPS requests and then do whatever you need load balance, or direct the queries to which ever node, nodes.....
Using squid as a reverse proxy that distributes the requests based on the URL ....
You can setup a reverse proxy that will see the http, HTTPS requests and then do whatever you need load balance, or direct the queries to which ever node, nodes.....
Using squid as a reverse proxy that distributes the requests based on the URL ....
ASKER
I currently have https forwarded from my firewall to my Microsoft Exchange Server for OWA and etc. If I forward https from my firewall to my Apache web server, what do I need to add to the attached above site-m.biz.conf.txt file to send https over to my Exchange Server.
I have LE certs on other servers that I did not mention but because of https going to my Exchange I have to manually renew (every 90 days) via DNS validation. I would like to start using https validation on my other sites.
The GoDaddy Cert on my Exchange Server will expire in mid-2019 - at that point I will be replacing it with a LE cert.
I have LE certs on other servers that I did not mention but because of https going to my Exchange I have to manually renew (every 90 days) via DNS validation. I would like to start using https validation on my other sites.
The GoDaddy Cert on my Exchange Server will expire in mid-2019 - at that point I will be replacing it with a LE cert.
IMHO try haproxy, nginx or squid as reverse proxy.
Those are made to handle these kind of issues.
haproxy will have relatively low overhead, and it can even dispatch on domain name without decrypting the stream using SNI.
Those are made to handle these kind of issues.
haproxy will have relatively low overhead, and it can even dispatch on domain name without decrypting the stream using SNI.
You would need to add the proxyPass to forward the requests to the owa
And then reverse to strip out the references to reflect.
The difficulty you may run into us owa may code the responses based on the requesting source.
Test it out first to make sure,
I.e. /somefolder will be the root of the owa
Proxypass /somefolder HTTPS://exchange server/owa
Reverseproxypass HTTPS://exchangeserver/owa /somefolder
Test the functionality. Often exchange owa sets up in HTTPS which adds overhead.... If http to the internal system....
Not sure why you have certs terminating every 90 days, lets encrypt ?
And then reverse to strip out the references to reflect.
The difficulty you may run into us owa may code the responses based on the requesting source.
Test it out first to make sure,
I.e. /somefolder will be the root of the owa
Proxypass /somefolder HTTPS://exchange server/owa
Reverseproxypass HTTPS://exchangeserver/owa /somefolder
Test the functionality. Often exchange owa sets up in HTTPS which adds overhead.... If http to the internal system....
Not sure why you have certs terminating every 90 days, lets encrypt ?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
in haproxy: (core description) for HTTP PROXY
in haproxy: (core description) for HTTPS SNI (no certificate on proxy, backend server provides the correct certificate.
THe examples are not complete, log options etc. etc. are left out for clarity.
...
frontend
bind :::443 v4v6 ssl cert /some/certificate/for *-site-m.mbiz
mode http
acl ISMAIL header(req.hostname) mail.site-m.biz
acl ISWWW header(req.hostname) www.site-m.biz
acl ISHOSTL header(req.hostname) host-l.site-s.org
acl ISWWWO req.hostname) www.site-s.org
use-backend be_mail if ISMAIL
use-backend be_wwwb if ISWWW
use-backend be_wwwo if ISWWWO
default_backend https_default_backend;
backend be_mail
mode http
server srv_mail1 mailsite-mbiz:443 ssl
server srv_mail2 mailsite-mbiz-server2:443 ssl in haproxy: (core description) for HTTPS SNI (no certificate on proxy, backend server provides the correct certificate.
...
frontend
bind :::443 v4v6
mode tcp
tcp-request inspect-delay 5s
tcp-request content accept if { req_ssl_hello_type 1 }
acl ISMAIL req_ssl_sni mail.site-m.biz
acl ISWWW req_ssl_sni www.site-m.biz
use_backend bes_mail if ISMAIL
use_backend bes_wwwo if ISWWWO
default_backend bes_ssl
backend bes_mail
mode tcp
server ssrv_mail1 mailsite-mbiz:443
server ssrv_mail2 mailsite-mbiz-server2:443 THe examples are not complete, log options etc. etc. are left out for clarity.
ASKER
Thanks , That is kind of what I tried with HAProxy - and failed. The Nginx solution I posted above is what is working.
ok np.
(wrt. haproxy SNI only works in tcp mode, req.header only in http mode... which is the major difference between the two configs.)
Most important is a working solution.
(wrt. haproxy SNI only works in tcp mode, req.header only in http mode... which is the major difference between the two configs.)
Most important is a working solution.
Open in new window
To see your entire redirect chain + also allow you to debug your redirect chains, without fighting with HSTS or browser caching.
Simple solution. Don't use any SSL Proxy directives at all. You'll waste hours of your life, you'll never get back.
Sounds like you already have a good handle on using LetsEncrypt certs.
Easy solution, is just ensure every single site is SSL wrapped + you'll be done.
Also... sigh... regards your GoDaddy cert... Likely best to change this to an LE cert too (unless it's an EV cert), so you can auto renew this cert via CRON, just like all your other LE certs. Otherwise, you'll always have one oddball machine... which someone will have to go through many manual steps to update every time it expires. Just a thought.