Site to Site VPN ASA 5510 to Meraki
I just set up a site to site VPN between an ASA 5510 and a Meraki MX64. The site are connected and up but cant communicate across them. Im sure its a routing issue. Here is an image of my setup.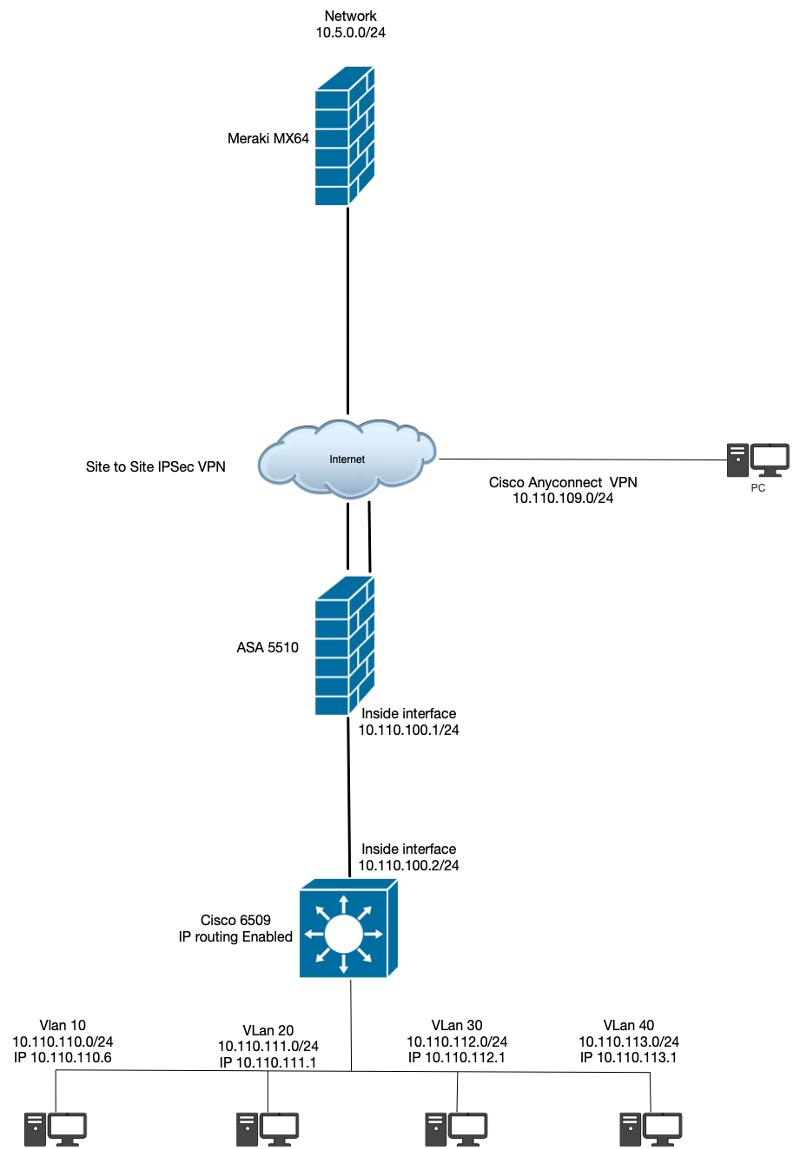
I cant ping anything on the inside of either.
Here is what I have for routing
nat (inside,outside) source static NETWORK_OBJ_10.110.100.0_2

I cant ping anything on the inside of either.
Here is what I have for routing
nat (inside,outside) source static NETWORK_OBJ_10.110.100.0_2
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I used the VPN wizard to create the VPN.
Here is a striped out copy of my ASA config
ASA-Current.rtf
Here is a striped out copy of my ASA config
ASA-Current.rtf
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I did insure the Meraki side. The Meraki side uses 10.5.0.0/24 only. Im assuming all the traffice from the ASA side will be only 10.110.110.0/24 because the router is in that network
As ITguy mentioned. Could be your firewall rules. Briefly glancing at your config, I don't see rules to allow the traffic out to the VPN.
ASKER
OK so from the cisco switch I ping the meraki network but non of the vlans can and vice versa. Any ideas on allowing the vLans to pass the traffice back and forth I assumed the switch would just pass back and forth between the vLans
What does the routing look like on the 6500 switch. I assume a default route to the ASA? On the Miraki, do you have routes to the vlan network? Also does your nonat policy cover all networks involved?
ASKER
OK so I have the tunnel running from the switch I can ping the Meraki network from the Meraki net work I can ping the switch. I added a route for the meraki network to the switch and created Nat rules. Still cant access Meraki get to the Vlans. I dont think its a switch issue because the anyconnecrt vpn can access everything just fine. I dont think its a meraki issue because I can ping everything back there. Here are my rules>
ACLs
access-list outside_cryptomap extended permit ip 10.110.100.0 255.255.255.0 object obj-TN (This one works fine)
access-list outside_cryptomap extended permit ip 10.110.110.0 255.255.255.0 object obj-TN
NAT rules
nat (inside,outside) source static NETWORK_OBJ_10.110.100.0_2
nat (inside,outside) source static obj-vLan10 obj-vLan10 destination static obj-TN obj-TN (Vlan10 is my 110 network)
CryptoMap
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer XX.XXX.XX.XXX
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map interface outside
What am I missing.
ACLs
access-list outside_cryptomap extended permit ip 10.110.100.0 255.255.255.0 object obj-TN (This one works fine)
access-list outside_cryptomap extended permit ip 10.110.110.0 255.255.255.0 object obj-TN
NAT rules
nat (inside,outside) source static NETWORK_OBJ_10.110.100.0_2
nat (inside,outside) source static obj-vLan10 obj-vLan10 destination static obj-TN obj-TN (Vlan10 is my 110 network)
CryptoMap
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer XX.XXX.XX.XXX
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map interface outside
What am I missing.
I'm confused. You have the tunnel running from the switch? Can you clarify what you mean here?
ASKER
OK so it re connected the VPN and that worked.
ASKER
Thanks it seemed to be a mix of both
@Member_2_6567402
Glad you were able to get it resolved.
Glad you were able to get it resolved.
Assuming you have Deny ALL as a default, you would need to selectively allow traffic to pass on the VPN to LAN or LAN to VPN zone.
At least that is the first thing I would check.