Emotet Trojan
Emotet Trojan!!
Currently dealing with an Emotet Trojan on a domain network with around 20 machines.
I know that the files replicates itself across the network and is generally a massive pain and is quite aggressive.
Does anyone have any tips at all that I could use to try and eradicate the malicious code.
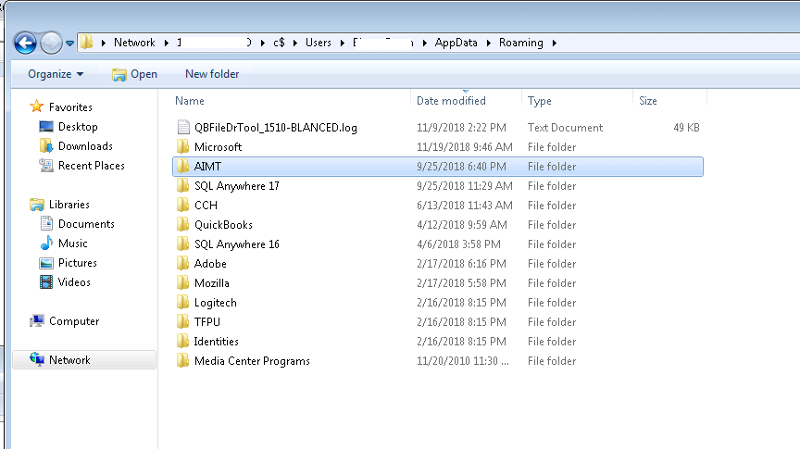
I thought I cleared it by taking all machines offline and manually cleaning them by removing the files that were sat in SYSTEMROOT and user appdata etc.
Any pointers would be really appreciated, also if there is any specific software that removes this Trojan, that would also be of great help.
Thanks!!!
Currently dealing with an Emotet Trojan on a domain network with around 20 machines.
I know that the files replicates itself across the network and is generally a massive pain and is quite aggressive.
Does anyone have any tips at all that I could use to try and eradicate the malicious code.
I thought I cleared it by taking all machines offline and manually cleaning them by removing the files that were sat in SYSTEMROOT and user appdata etc.
Any pointers would be really appreciated, also if there is any specific software that removes this Trojan, that would also be of great help.
Thanks!!!
ASKER
@John - I was hoping no one was going to say this haha! Yea tried that, we use Sophos Cloud with Intercept X, but by the looks of things, neither of those systems can do anything once it’s on the system.
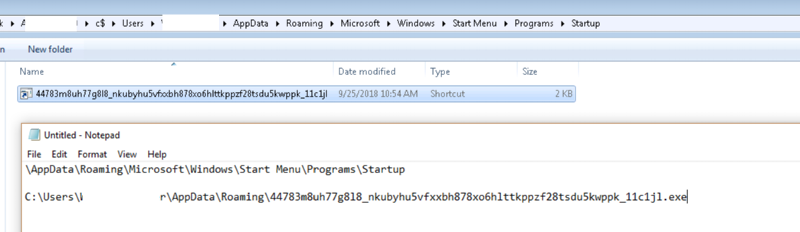
I’m taking the network offline again tomorrow and performing another manual clean, do you know of any other locations Emotet might be hiding?
I’m taking the network offline again tomorrow and performing another manual clean, do you know of any other locations Emotet might be hiding?
Been dealing with this at one site off and on. Their recovered domain (stepped back to prior to the bug) is sitting on our bench for delivery this weekend.
1: Hopefully via an uncompromised machine/VM install RSAT (Remote Server Administrator Tools)
2: Use Active Directory Users & Computers to MANAGE each server and add TEMPAdminUser and use a password generator to local admins
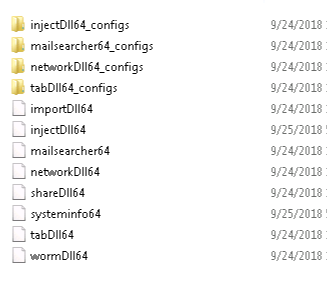
3: Explorer --> \\ServerName\c$\Users\*.ex
4: Explorer --> \\ServerName\c$\Windows\Sy
5: Explorer --> \\ServerName\c$\Windows\Te
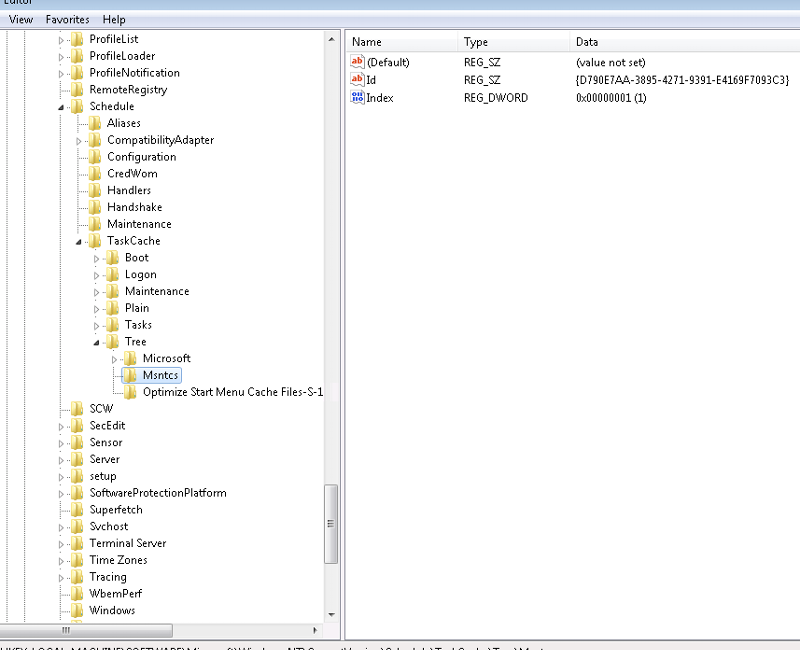
6: Regedit --> Mount ServerName Hive --> Clean all RUN keys of references
7: Log on to SERVERNAME using TEMPLocalAdmin
8: Task Manager --> END TASK --> Little Gear with no Name (check sub-services)
9: Task Scheduler --> DEL MSNCTS or FOREIGN
10: C:\Users\*.EXE SEARCH then SHFT DELETE
11: Elevated PowerShell: Remove-WindowsFeature FS-SMB1 -Restart
12: PATCH
That's a rough corral and mitigate strategy that I used.
If DCs are compromised then start fishing through the backups for a point in time to restore from as there's no more trust. Period. Full Stop.
1: Hopefully via an uncompromised machine/VM install RSAT (Remote Server Administrator Tools)
2: Use Active Directory Users & Computers to MANAGE each server and add TEMPAdminUser and use a password generator to local admins
3: Explorer --> \\ServerName\c$\Users\*.ex
4: Explorer --> \\ServerName\c$\Windows\Sy
5: Explorer --> \\ServerName\c$\Windows\Te
6: Regedit --> Mount ServerName Hive --> Clean all RUN keys of references
7: Log on to SERVERNAME using TEMPLocalAdmin
8: Task Manager --> END TASK --> Little Gear with no Name (check sub-services)
9: Task Scheduler --> DEL MSNCTS or FOREIGN
10: C:\Users\*.EXE SEARCH then SHFT DELETE
11: Elevated PowerShell: Remove-WindowsFeature FS-SMB1 -Restart
12: PATCH
That's a rough corral and mitigate strategy that I used.
If DCs are compromised then start fishing through the backups for a point in time to restore from as there's no more trust. Period. Full Stop.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
MS Eternal Blue patch https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
ASKER
Thanks for all your help to all who contributed!
I managed to clear the malware network wide by using your suggestions, I found that also using netstat on an isolated network with machines that were still showing the malware even after deletion helped as well. It appeared one of three machines was being used as a host to send out a request to get the exe from a server based in Mexico. Removed machine from network and blocked IP, managed to save the network.
Cheers!
I managed to clear the malware network wide by using your suggestions, I found that also using netstat on an isolated network with machines that were still showing the malware even after deletion helped as well. It appeared one of three machines was being used as a host to send out a request to get the exe from a server based in Mexico. Removed machine from network and blocked IP, managed to save the network.
Cheers!
Glad to hear you didn't have to wipe and reload..
In addition to your steps, run Malwarebytes - Full Scan and a Full Scan with your own Anti Virus.