Ac3
asked on
How to gain root access to a vulnerable Red hat Linux server?
How to gain root access to a vulnerable Red hat Linux server?
I only have the following details.
1) There are 3 services running. (SSH, FTP and HTTP)
2) I managed to get some user username and password, however when i tried to login into the server, i recieved the error permission denied.
I only have the following details.
1) There are 3 services running. (SSH, FTP and HTTP)
2) I managed to get some user username and password, however when i tried to login into the server, i recieved the error permission denied.
ASKER
The server is a virtual image that was given to me.
I have some user that i can access using the ssh, and the others are access using ftp
I have some user that i can access using the ssh, and the others are access using ftp
Unsure if this is true "I have some user that i can access using the ssh", what else is required.
If you can login with via ssh... well... so long as the user has admin/sudo privilege, you can ssh in + do whatever's required.
So first question...
Let me know if you can complete an ssh login + if the related user has sudo privilege... specifically you can do this...
If you can login with via ssh... well... so long as the user has admin/sudo privilege, you can ssh in + do whatever's required.
So first question...
Let me know if you can complete an ssh login + if the related user has sudo privilege... specifically you can do this...
sudo bashASKER
So if this is an image you have, you should be able to get console access. With console access you can manipulate boot parameters... Once you do that you have root.
If you can't get console access, then it isn't your system to work on.
If you can't get console access, then it isn't your system to work on.
You're pretty much out of luck then, for getting to root the easy way.
If I were faced with this, here's what I'd do.
1) create an ssh key pair
2) manually add the public key to ~root/.ssh/authorized_keys
3) start the virtual image
4) shell into root via your private key from step #1
Now then... how you do step #2 will depend on the form of your virtual image.
You will have to arrange to mount this image in a format which allows you to access all files in the file system... via normal file operations...
In other words, if your image is compressed or encrypted, you will have to mount the image in such a way as to uncompress/decrypt your image, then unmount it in such a way to preserve the changes you've made to authorized_keys.
What's required to accomplish this is very complex + exceeds a simple EE comment.
Tip: By far the easiest solution will be to acquire the root password of your image from the person who created the image.
If I were faced with this, here's what I'd do.
1) create an ssh key pair
2) manually add the public key to ~root/.ssh/authorized_keys
3) start the virtual image
4) shell into root via your private key from step #1
Now then... how you do step #2 will depend on the form of your virtual image.
You will have to arrange to mount this image in a format which allows you to access all files in the file system... via normal file operations...
In other words, if your image is compressed or encrypted, you will have to mount the image in such a way as to uncompress/decrypt your image, then unmount it in such a way to preserve the changes you've made to authorized_keys.
What's required to accomplish this is very complex + exceeds a simple EE comment.
Tip: By far the easiest solution will be to acquire the root password of your image from the person who created the image.
ASKER
Hey David,
Thanks for your suggestion. Could you teach me how to create a ssh key path? I'm kind of new to Linux with only 2 weeks of learning.
Thanks for your suggestion. Could you teach me how to create a ssh key path? I'm kind of new to Linux with only 2 weeks of learning.
ASKER
Hi Scott,
This image is given to me as a homework assignment. Thus I do not have any console access to it. I was hoping that you will be able to help me and hopefully widen my knowledge in Linux.
This image is given to me as a homework assignment. Thus I do not have any console access to it. I was hoping that you will be able to help me and hopefully widen my knowledge in Linux.
If this in an assignment, then all access you require should be available.
If not, request your instructor provide you with the root password...
Or...
Follows steps above to give yourself root access.
If not, request your instructor provide you with the root password...
Or...
Follows steps above to give yourself root access.
ASKER
Hi David,
Yes this is an assignment. However no access was being given to me.
Yes this is an assignment. However no access was being given to me.
What kind of assignment? And if we do your homework, will you learn the lesson and pass any future tests?
ASKER
Hi Scott,
I'm just trying to understand how to gain root access of a vulnerable Red Hat Linux server, not doing it for me.
The main question of this is to gain root access, the other question of the assignment I'm more or less able to solve them by myself.
I'm just trying to understand how to gain root access of a vulnerable Red Hat Linux server, not doing it for me.
The main question of this is to gain root access, the other question of the assignment I'm more or less able to solve them by myself.
You're doing it wrong.
You need to read the instructions and title in your CTF game for this target. There should be a hint on what to do. You also don't need full root access, just access to the flag.txt file contents.
That's all the hint you need to succeed.
You need to read the instructions and title in your CTF game for this target. There should be a hint on what to do. You also don't need full root access, just access to the flag.txt file contents.
That's all the hint you need to succeed.
ASKER
Hi serialband,
I have access the flag.txt and there is nothing useful I can use from here. The content of the flag.txt is for my other questions of my assignment which i have solved it.
I have access the flag.txt and there is nothing useful I can use from here. The content of the flag.txt is for my other questions of my assignment which i have solved it.
Then each of your assignment steps should be giving clues to the next step. Getting actual root in the real world is not really that easy. The assignments are designed as step by step building blocks to the next step. These CTFs are more logical progression. You should have clues to the solution as you finish each of the previous steps. That's generally how CTF are designed.
Is this a currently running public CTF? Which one is it?
Or, is this a private one for a class and inaccessible to he public?
Is this a currently running public CTF? Which one is it?
Or, is this a private one for a class and inaccessible to he public?
I assume since you are told the systems OS, and that it is vulnerable, you are going to have to scan for any listed vulnerabilities for that OS listed in the CVE's.
Now to actually gain access you will need some sort of exploit kit to actually get in, or the skills to write your own.
If you just need to show the steps needed, I gave you more clues.
Usually an attacker only has the OS signatures from scans or other signs, and knows how to get in or which kits to unleash... Except for the script kiddies, that just unleash a full kit on everything and hope one breaks...
Since you have some access, you can get the exact Redhat kernel version running and then look up the cve'S on it. That should give you clues on what to try and hit...
Now to actually gain access you will need some sort of exploit kit to actually get in, or the skills to write your own.
If you just need to show the steps needed, I gave you more clues.
Usually an attacker only has the OS signatures from scans or other signs, and knows how to get in or which kits to unleash... Except for the script kiddies, that just unleash a full kit on everything and hope one breaks...
Since you have some access, you can get the exact Redhat kernel version running and then look up the cve'S on it. That should give you clues on what to try and hit...
You have access to the system... so you need to check if the tools
have any vulnerabilities on board and use those.
Clues: Tools that run as root them selves and and provide some network access or other command entry means.
You have to approach this as an escape-room.
have any vulnerabilities on board and use those.
Clues: Tools that run as root them selves and and provide some network access or other command entry means.
You have to approach this as an escape-room.
ANother clue... uname -a should give you running kernel.
I see 4 hints: (or files in you case...)
1 flag.txt
2 a packet capture (someone made a network recording)...
3 a history of commands from previous logon
4 some shell settings from a previous run.
1 flag.txt
2 a packet capture (someone made a network recording)...
3 a history of commands from previous logon
4 some shell settings from a previous run.
ASKER
Hi Scott and noci,
I have did a vulnerability scan and the vulnerabilities falls under Joomla using http port.
I have did a vulnerability scan and the vulnerabilities falls under Joomla using http port.
ASKER
Hi noci,
in regards to the hints,
1) flag.txt contains only an answer to a sub question in regards to my assignment.
2) capture.pcapng contains a username and password to a user, however, when i were to use that credentials to login, i get permission denied.
3 and 4) are you meaning the .bash_history and .bash_profile?
in regards to the hints,
1) flag.txt contains only an answer to a sub question in regards to my assignment.
2) capture.pcapng contains a username and password to a user, however, when i were to use that credentials to login, i get permission denied.
3 and 4) are you meaning the .bash_history and .bash_profile?
ref. 3) & 4)... yes.
capture should also provide protocol info, connection method....
You many not be able to logon interactively, but can use FTP or some other means... Are they by change joomla info...?
capture should also provide protocol info, connection method....
You many not be able to logon interactively, but can use FTP or some other means... Are they by change joomla info...?
ASKER
Hi noci,
I have viewed the contents inside the .bash_history and .bash_profile.
For .bash_history, there is only the codes that i have previously keyed in the ftp when i had access to the user account.
For .bash_profile, the image attached is the result i get.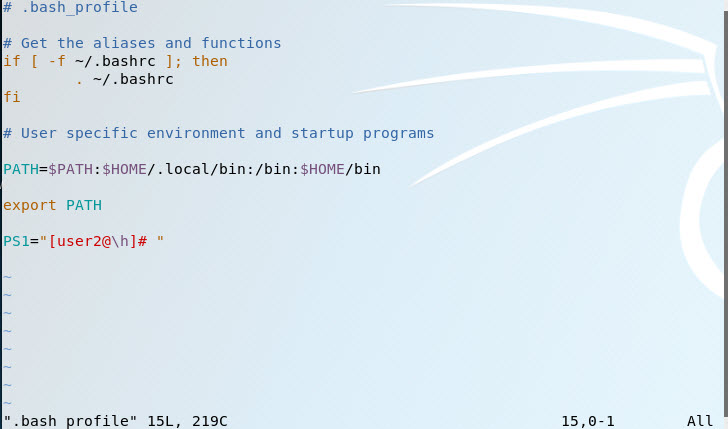
As for your second question, I'm not too sure as to what you mean by change joomla info. So sorry about that.
I have viewed the contents inside the .bash_history and .bash_profile.
For .bash_history, there is only the codes that i have previously keyed in the ftp when i had access to the user account.
For .bash_profile, the image attached is the result i get.

As for your second question, I'm not too sure as to what you mean by change joomla info. So sorry about that.
the bash history is interesting from BEFORE your commands. (if you can get the original image try to investigate again.
Esp. by getting a copy of those files in a safe place... (just logging in and running random stuff and logging out again will remove any potentially usefull info).
Check CVE entries for problems with joomla... (and are there no other services active... only http(s)?)
Check the capture again if there is anything useful... it's not just username & password also access method, portnumber, protocols etc. etc.
Esp. by getting a copy of those files in a safe place... (just logging in and running random stuff and logging out again will remove any potentially usefull info).
Check CVE entries for problems with joomla... (and are there no other services active... only http(s)?)
Check the capture again if there is anything useful... it's not just username & password also access method, portnumber, protocols etc. etc.
Hi,
also check /etc/hosts.allow and /etc/hosts.deny files. Add your client system to /etc/hosts.allow and try again.
Cheers
also check /etc/hosts.allow and /etc/hosts.deny files. Add your client system to /etc/hosts.allow and try again.
Cheers
ASKER
Hi dfke,
i've tried to access it but to no success.
Cheers
i've tried to access it but to no success.
Cheers
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
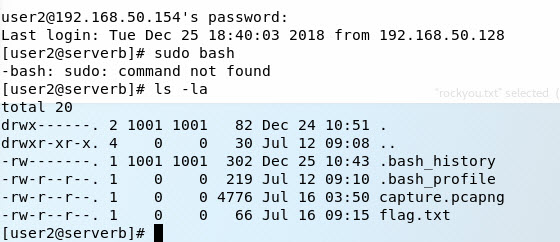
You said you have a user/pass + you failed to mention which service.
Each service - SSH, FTP, HTTP - are all very different. Having some HTTP basic auth password won't grant you access to any SSH or SFTP service... at least it shouldn't, unless a hosting company has seriously munged up their permission system.
So you should get a permission denied, depending on what you're doing.
Questions... State why...
1) You can't just open a ticket with your hosting company + ask for a password reset.
2) Specific service you have a user/pass for.
3) Specific service you're trying to login to.
4) State whether you're trying to do Penetration Testing or trying to login this machine for some other reason.