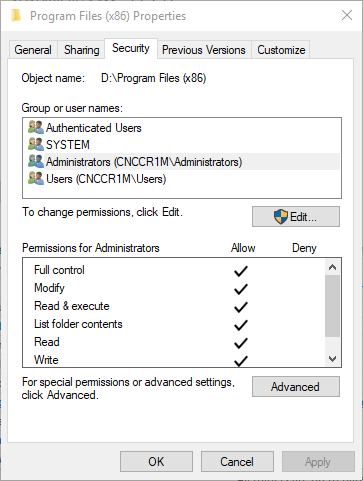
Security settings for Program Files (x86)
What you see is normal (i.e., what I see on my machines). Application packages can use Program Files but it is restricted against users and users (any kind of user) should not use this folder. It is specifically not for data storage.
I have a d:\Program Files (x86) as well. I created it because I install almost everything onto my D:\ drive. But my folder permissions a very different.
icacls output:
D:\Program Files (x86)>icacls .
. BUILTIN\Administrators:(F)
BUILTIN\Administrators:(OI
NT AUTHORITY\SYSTEM:(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(
NT AUTHORITY\Authenticated Users:(M)
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(M)
BUILTIN\Users:(RX)
BUILTIN\Users:(OI)(CI)(IO)
Successfully processed 1 files; Failed processing 0 files
D:\Program Files (x86)>
icacls output:
D:\Program Files (x86)>icacls .
. BUILTIN\Administrators:(F)
BUILTIN\Administrators:(OI
NT AUTHORITY\SYSTEM:(F)
NT AUTHORITY\SYSTEM:(OI)(CI)(
NT AUTHORITY\Authenticated Users:(M)
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(M)
BUILTIN\Users:(RX)
BUILTIN\Users:(OI)(CI)(IO)
Successfully processed 1 files; Failed processing 0 files
D:\Program Files (x86)>
Ben, I just noticed a typo. Take the command
icacls "d:\Program Files (x86)"ASKER
Hi,
Here's the results of the icacls command:
C:\Windows\system32>icacls
d:\Program Files (x86) NT SERVICE\TrustedInstaller:(
NT SERVICE\TrustedInstaller:(
NT AUTHORITY\SYSTEM:(M)
NT AUTHORITY\SYSTEM:(OI)(CI)(
BUILTIN\Administrators:(M)
BUILTIN\Administrators:(OI
BUILTIN\Users:(RX)
BUILTIN\Users:(OI)(CI)(IO)
CREATOR OWNER:(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(OI)(CI)(IO)(GR,G
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(OI)(CI)(IO)(GR,G
Successfully processed 1 files; Failed processing 0 files
The problem is I can't even copy (xcopy/robocopy) this folder. I'm trying to migrate it to a new drive as this one is failing and am unable to. Nor can I add permissions for domain admins to it.
--Ben
Here's the results of the icacls command:
C:\Windows\system32>icacls
d:\Program Files (x86) NT SERVICE\TrustedInstaller:(
NT SERVICE\TrustedInstaller:(
NT AUTHORITY\SYSTEM:(M)
NT AUTHORITY\SYSTEM:(OI)(CI)(
BUILTIN\Administrators:(M)
BUILTIN\Administrators:(OI
BUILTIN\Users:(RX)
BUILTIN\Users:(OI)(CI)(IO)
CREATOR OWNER:(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(OI)(CI)(IO)(GR,G
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(OI)(CI)(IO)(GR,G
Successfully processed 1 files; Failed processing 0 files
The problem is I can't even copy (xcopy/robocopy) this folder. I'm trying to migrate it to a new drive as this one is failing and am unable to. Nor can I add permissions for domain admins to it.
--Ben
You need to install into Program Files, not copy installations into it.
As your command output shows, the group administrators has full access. Your screenshot needs to be scrolled down a little and you'll see a checkmark at "special permissions". Why "special"? Because you set both modify and full for some odd reason.
->So why doesn't it work the way you want? Because of UAC. Try the actions elevated and anything will just work.
->So why doesn't it work the way you want? Because of UAC. Try the actions elevated and anything will just work.
ASKER
How do I assign full access to domain admins for this folder? I copy stuff around at times logged in with that level but don't see a way to add a user/group.
How do I assign full access to domain admins for this folder? I copy stuff around at times logged in with that level but don't see a way to add a user/group.Domain Admins have full access to this folder. They are part of the Administrators group
...as Shaun says. However, Domain admins are also governed by UAC, which means, you need to elevate to make changes to that folder even as admin/domain admin.
To prove it, do the following: activate the local admin account like this
Now logon with that account and all will just work (accounts named "administrator" are not governed by UAC).
To prove it, do the following: activate the local admin account like this
net user administrator /active temppasswordNow logon with that account and all will just work (accounts named "administrator" are not governed by UAC).
ASKER
Sorry, will have to set this aside for the moment. Acronis Trueimage tanked a new drive on this workstation so badly that even the BIOS won't complete booting with it attached. Need to unwind that first. Am at a loss of words to describe how enthused I am about this.
--Ben
--Ben
ASKER
Hi,
Well that was a PITA; the vendor sent the wrong model on that drive. Wasn't obvious at all.
Yes, local accounts (including Administrator) have all the functionality enabled with no issues. What can I do to get the domain admin group access to that same level of access? Other side-effects I'm seeing are I can't open the Action Center; search next to the Windows icon is inactive.
Left-clicking the Windows icon does nothing. All work with a local account.
--Ben
Well that was a PITA; the vendor sent the wrong model on that drive. Wasn't obvious at all.
Yes, local accounts (including Administrator) have all the functionality enabled with no issues. What can I do to get the domain admin group access to that same level of access? Other side-effects I'm seeing are I can't open the Action Center; search next to the Windows icon is inactive.
Left-clicking the Windows icon does nothing. All work with a local account.
--Ben
Domain admins should NEVER even be used on endpoints. Don't even think about it, it's too risky.
I'll tell you how to get along: if you are using a domain account that is local admin on a machine and you copy to that folder, UAC will kick in with a confirmation prompt. You confirm it and that's it, file copied - normal and expected behavior.
If you use programs that are not UAC aware, like for example notepad and you try to modify a text file (be it an .ini file) within a folder of program files, you will need to elevate the program (notepad), first, by right clicking notepad and selecting "run as administrator". That's all.
I'll tell you how to get along: if you are using a domain account that is local admin on a machine and you copy to that folder, UAC will kick in with a confirmation prompt. You confirm it and that's it, file copied - normal and expected behavior.
If you use programs that are not UAC aware, like for example notepad and you try to modify a text file (be it an .ini file) within a folder of program files, you will need to elevate the program (notepad), first, by right clicking notepad and selecting "run as administrator". That's all.
ASKER
I'm getting to that point but am still trying to understand why a domain admin can't access basic functionality that disappeared when I logged in with those credentials. I know of no way to open the action center or left click on the Windows icon with 'run as administrator' elevation. Am I missing something?
--Ben
--Ben
Describe what you are trying to elevate exactly. If it's an application, we right click the executable.
If it's just copying within explorer, UAC (unless it's turned off) will even automatically offer to elevate explorer via the consent dialogue.
If it's just copying within explorer, UAC (unless it's turned off) will even automatically offer to elevate explorer via the consent dialogue.
ASKER
Good morning,
Not so much elevating an app as significant functionality in Win 10 while logged on as a domain admin is non-functional. Left-clicking on the Windows icon does nothing. The 'Type here to search' is disabled. On the right side of the task bar, right-clicking the notifications icon and clicking on Open Action Center does nothing.
All these work when I log in as a local admin/normal user, so there has to be something tweaked in UAC somehow.
Not so much elevating an app as significant functionality in Win 10 while logged on as a domain admin is non-functional. Left-clicking on the Windows icon does nothing. The 'Type here to search' is disabled. On the right side of the task bar, right-clicking the notifications icon and clicking on Open Action Center does nothing.
All these work when I log in as a local admin/normal user, so there has to be something tweaked in UAC somehow.
What you describe is not connected to your original question and has nothing to do with permissions or UAC.
If these problems occur, usually, the user profile is toast and needs to be renewed.
If these problems occur, usually, the user profile is toast and needs to be renewed.
ASKER
Oh! That's interesting. Would that be as simple as logging in with a local admin account and killing the \users\... domain admin folder, then logging back in as the domain admin?
No, never just delete the folder. Logon as another user, press winkey+pause together, at the left, go to advanced system settings ->user profiles ->settings and delete it there (after backing up its data if any).
ASKER
Where do I go to see its data first? It may not have anything I really care about.
You logon as that user and look at the documents folder or wherever that admin saves his data (if any).
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Please share the following details:
1 the output of
Open in new window
2 how and why you created d:\Program Files (x86)