Sonicwall hacking of configuration
I inherited a client that had a loose security environment and that turned into a ransomware attack. Things have been weird ever since. One of the weird situations is us finding ports 443 and 80 open and forwarded to our jump box. We deleted those ports or so we thought because they popped up again. We chalked it up to maybe not applying the setting. So maybe it didnt get saved. However, the client reported internet issues that felt like someone did a loopback in the network. Then i looked at the router and found these ports open again w a loop back comment. We changed the password of the router last time. We are really at a loss as to why we are being haunted by this issue. Any thoughts? Two factor authentication does not come out for sonicwall until later in the year. We are setting up LDAP tomorrow and VLAN segmentation on the 20th for some additional protection but we are still unclear how this individual is lurking.
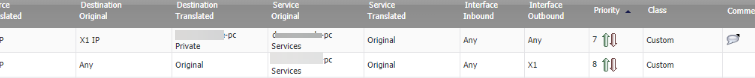
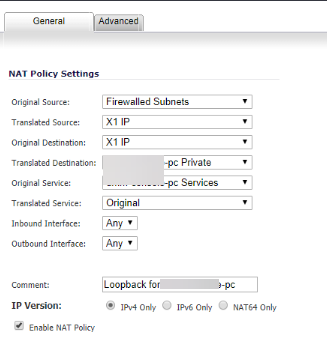


ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER