The name on the security certificate is invalid or does not match the name on the site
The external address is the address that is resolved. So with no external address assigned you will not be able to resolve to it.
Make sure that the address that is resolved matches what is in the Cert. Normally you want to purchase a trusted third party SAN cert to address multiple domain names. Your server has an internal address that is pointed to exchange.domainname.local and your Cert does not have this address in the Cert.
If you click on the View Certificate you will see the chain and it probably is Exchange.domainame.com
If you change the internal URL address to Exchange.domainame.com and make sure you can resolve this address internally you will most likely be fine. You may have to create a DNS zone for domainname.com and add a A-Record of a CNAME for this address.
Make sure that the address that is resolved matches what is in the Cert. Normally you want to purchase a trusted third party SAN cert to address multiple domain names. Your server has an internal address that is pointed to exchange.domainname.local and your Cert does not have this address in the Cert.
If you click on the View Certificate you will see the chain and it probably is Exchange.domainame.com
If you change the internal URL address to Exchange.domainame.com and make sure you can resolve this address internally you will most likely be fine. You may have to create a DNS zone for domainname.com and add a A-Record of a CNAME for this address.
What version of exchange is this? you can get a publicly signed SSL certificate for ales that ten dollars these days?
Outlook Error “The name of the security certificate is invalid or does not match the name of the site.”
Pete
Outlook Error “The name of the security certificate is invalid or does not match the name of the site.”
Pete
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
If you click on the View Certificate you will see the chain and it probably is Exchange.domainame.comit's failing exchange.clientdomain.loca
Normally you want to purchase a trusted third party SAN cert to address multiple domain names. Your server has an internal address that is pointed to exchange.domainname.local and your Cert does not have this address in the Cert.
A UCC\SAN cert was purchased and installed which allows up to 5 names and only three are used. If I rekey the cert and add exchange.clientdomain.loca
My understanding is exchange.clientdomain.loca
I don't mind rekeying the cert if it's not going to disconnect or give a cert error to current mobile users. Will make the change if its the best option and needs to be done.
Is there a way to create a self-signed cert since this is .local and/or use DNS on the server? You mentioned create a CNAME and Host A record.
its very unlikely you can add your internal domain to the SSL cert as this practice was ceased several years ago. Very few CAs will allow you to do this and insist all domains on the SSL cert are backed up by public DNS records.
Just amend your internal addresses as advised and it works as designed.
Just amend your internal addresses as advised and it works as designed.
ASKER
Pete may just rekey the current cert, was hoping not to break current mobile devices. If they don't disconnect or give a cert error then will do this now. Since the failing cert name is exchange.clientdomain.loca
ASKER
Steve, setting up the internal DNS now. Is the 2010 article ok for a 2016 Exchange server? I'm assuming so because all the powershell commands work so far for the following.
Set-WebServicesVirtualDire
Set-WebServicesVirtualDire
I tested the get- commands for the internal DNS configuration and assuming set- will work if get- is pulling up information. There's been several warnings in powershell for years some of the commands are changing. Cert errors become a nightmare when they get halfway installed / configured and trying to avoid this. I'm probably too cautious when it comes to certs.
Set-WebServicesVirtualDire
Set-WebServicesVirtualDire
I tested the get- commands for the internal DNS configuration and assuming set- will work if get- is pulling up information. There's been several warnings in powershell for years some of the commands are changing. Cert errors become a nightmare when they get halfway installed / configured and trying to avoid this. I'm probably too cautious when it comes to certs.
ASKER
Didn't answer this prior, exchange 2016.
ASKER
Set-ClientAccessServer -Identity EXCHANGE -AutoDiscoverServiceIntern
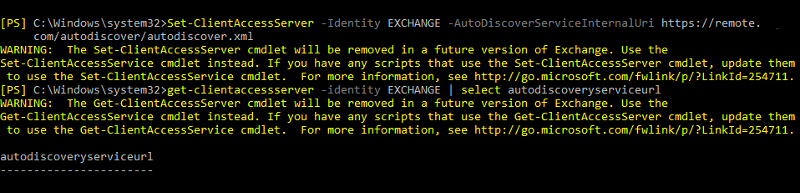

ASKER
ASKER
Just amend your internal addresses as advised and it works as designed.Steve any ideas?
.local is no longer allowed to be added to SAN certs.
Your best course of action is to change both the internal and external address to be exchange.domain.com and use your public cert that you have for the server.
Your best course of action is to change both the internal and external address to be exchange.domain.com and use your public cert that you have for the server.
ASKER
I did this already.
Set-WebServicesVirtualDire
Set-WebServicesVirtualDire
The DNS settings I configured above are now routing logons to exchange outside and Outlook won't launch new profiles. Assuming this is due to the DNS changes made and the Set-ClientAccessServer -Identity EXCHANGE -AutoDiscoverServiceIntern
Good news current Outlook users just get the annoying cert error. Bad news no new profiles can be added to Outlook. I'm assuming deleting the remote.clientdomain.com forward lookup zone will resolve this.
Am I correct thinking if Set-ClientAccessServer -Identity EXCHANGE -AutoDiscoverServiceIntern
Set-WebServicesVirtualDire
Set-WebServicesVirtualDire
The DNS settings I configured above are now routing logons to exchange outside and Outlook won't launch new profiles. Assuming this is due to the DNS changes made and the Set-ClientAccessServer -Identity EXCHANGE -AutoDiscoverServiceIntern
Good news current Outlook users just get the annoying cert error. Bad news no new profiles can be added to Outlook. I'm assuming deleting the remote.clientdomain.com forward lookup zone will resolve this.
Am I correct thinking if Set-ClientAccessServer -Identity EXCHANGE -AutoDiscoverServiceIntern
ASKER
You may have to create a DNS zone for domainname.com and add a A-Record of a CNAME for this address.yo_bee do you mind clarifying. I configured the zone but haven't made any records, only the default records were created.
First thing is that your Active Directory domain relies heavily on DNS and when you create your first Domain Controller it will also create your DNS zone for domain.local if that is what you call the domain. When you join computers to your domain they will register with the DNS server under the domain.local. Now you want to have some control of what IP's are registered with other domains (i.e. exchange.domain.com) so you need to create a new zone that has domain.com. Once this is created you can added a new A-Record for exchange.domain.com and put the internal IP-Address of that server in to the record. Once this is done you should ping it from command prompt and see if it resolves that correct internal IP. You should already have a public DNS record for this same A-Record that points to your public IP issued by your ISP.

Going back up a few responses, the reason your set-clientaccessserver seemed not to work is you checked it with a completely wrong attribute. There is no such attribute as autodiscoveryserviceurl. It is autodiscoverserviceinterna
the scp listed is what outlook used internally. You need to be sure your internal clients can resolve the address returned to either your exchange server or the Exchange VIP on your load balancer.
Lastly, you need to make sure this FQDN is listed on your certificate as a SAN name. If you are using a Wildcard cert, it may work. I had no luck with them in the past and use UC certs for exchange exclusively.
the scp listed is what outlook used internally. You need to be sure your internal clients can resolve the address returned to either your exchange server or the Exchange VIP on your load balancer.
Lastly, you need to make sure this FQDN is listed on your certificate as a SAN name. If you are using a Wildcard cert, it may work. I had no luck with them in the past and use UC certs for exchange exclusively.
Outlook anywhere or Outlook client show Security Alert or certificate error , you need to read this article before:
http://www.shudnow.net/2013/07/26/outlook-certificate-error-and-autodiscover-domain-com-not-working/?fbclid=IwAR2sKW9nZSABZvbHdpyy2emDVdtJPGKmz2yoPqFWvOjMPcQJ9UBAWshcIU0
Use the Set-ClientAccessService cmdlet to modify settings that are associated with the Client Access server role.
https://docs.microsoft.com/en-us/powershell/module/exchange/client-access-servers/set-clientaccessservice?view=exchange-ps
http://www.shudnow.net/2013/07/26/outlook-certificate-error-and-autodiscover-domain-com-not-working/?fbclid=IwAR2sKW9nZSABZvbHdpyy2emDVdtJPGKmz2yoPqFWvOjMPcQJ9UBAWshcIU0
Use the Set-ClientAccessService cmdlet to modify settings that are associated with the Client Access server role.
https://docs.microsoft.com/en-us/powershell/module/exchange/client-access-servers/set-clientaccessservice?view=exchange-ps
Sorry for not responding, caught up on other stuff.
http://www.mustbegeek.com/configure-external-and-internal-url-in-exchange-2016/
Basically, you should set the internal & external URls to use the external domain so they work with your SSL cert.
E.G
Old:
External: mail.company.com/<various Exchange URLs>
Internal: server.internalDomain.loca
Becomes
External: mail.company.com/<various Exchange URLs>
internal: mail.company.com/<various Exchange URLs>
to prevent unnecessary traffic going out over your routers, you should also create an internal DNS entry (or zone, depending on your setup) to direct mail.company.com to your Exchanges internal IP.
Is the 2010 article ok for a 2016 Exchange server?yes but bets to use the right one now we know which Exch version you're on:
http://www.mustbegeek.com/configure-external-and-internal-url-in-exchange-2016/
Basically, you should set the internal & external URls to use the external domain so they work with your SSL cert.
E.G
Old:
External: mail.company.com/<various Exchange URLs>
Internal: server.internalDomain.loca
Becomes
External: mail.company.com/<various Exchange URLs>
internal: mail.company.com/<various Exchange URLs>
to prevent unnecessary traffic going out over your routers, you should also create an internal DNS entry (or zone, depending on your setup) to direct mail.company.com to your Exchanges internal IP.
ASKER
I did everything the thread requested and for whatever reason continued to have issues. I was pressed for time so I opened a live session here and the problem was resolved. I would like to mention the tech that helped me during the live session but can't find this setting in EE, would someone please point it to me.
Thank you.
Thank you.
do you still need help?
ASKER
No the problem was resolved after I paid an EE for live support and for the life of me I can't remember who it was. I also can't find the transaction in EE and why I'm asking how to go about finding this information.
Do you know what it was?
ASKER
Thank you for everyone that helped on this. Was a combination of reading older information and somehow combined with missing information on the Exchange server. Maybe going to fast and simply overlooking details. We found an internal URL incorrectly configured and had to make an additional DNS entry. As mentioned I also had an EE tech take a look and this is the work that was performed. Sorry for the delay it's been a busy month. Thanks again for all the help.
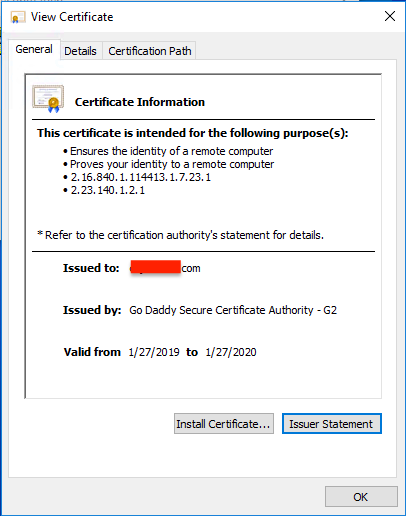
ASKER
My understanding is both directories should be set to https://remote.clientsdomain.com
Set-WebServicesVirtualDire
Set-WebServicesVirtualDire
Run this and restart IIS?