John Sheehan
asked on
Working with Windows Firewall Exceptions
After a nasty Trojan virus, we have implemented windows firewall SMB block rules on our client computers to block incoming SMB. This allows us to protect computers on the same network from a lot of malware file dropping.
We are also implementing a new Patch Manager that uses WSUS as an intermediary. This mechanism requires SMB and WMI. So, with Group Policy I tried to put in an exception in the rules using an allow if secure, then putting in the computers that need access. I found out that if there are local rules that allow SMB and they are merged, it will allow anything through. I also went the route of setting up a machine (windows 10) firewall manually, then exporting all the firewall rules with an exception (defined in remote computer scope), then denying local firewall rules and local security connections through the GPO. This, initially, I thought worked. However, when testing the same GPO on a windows 7 machine, it did not clear out the local firewall rules.
Is there something different I need to do for windows 7 firewall, or is there another route we should take? Right now our LAN to LAN segments are protected with firewall, but clients on the same segment are vulnerable to each other unless I do a block rule (which takes precedent over any allow rule).
We are also implementing a new Patch Manager that uses WSUS as an intermediary. This mechanism requires SMB and WMI. So, with Group Policy I tried to put in an exception in the rules using an allow if secure, then putting in the computers that need access. I found out that if there are local rules that allow SMB and they are merged, it will allow anything through. I also went the route of setting up a machine (windows 10) firewall manually, then exporting all the firewall rules with an exception (defined in remote computer scope), then denying local firewall rules and local security connections through the GPO. This, initially, I thought worked. However, when testing the same GPO on a windows 7 machine, it did not clear out the local firewall rules.
Is there something different I need to do for windows 7 firewall, or is there another route we should take? Right now our LAN to LAN segments are protected with firewall, but clients on the same segment are vulnerable to each other unless I do a block rule (which takes precedent over any allow rule).
What was the virus or viruses? Emotet?
ASKER
It was Emotet, along with all the things it delivers in its payload. We rebuilt the affected subnets from scratch and implemented all security measures in a primer we got on it. We now segment each department with a LAN firewall, which is great for protecting, say, auditing from purchasing, but it doesn't solve the problem of protecting clients on the same subnet from themselves. So the SMB block rule is crucial moving forward, but it isn't friendly to a lot of the deployment tools out there.
Okay, then the first place to start is to remove SMBv1 from _all_ desktops and servers:
If the domain controllers were compromised then the domain is considered pwned. There is no more trust there!
We worked with a situation where we needed to step the PDCe back to prior to the Emotet infection, create new domain admin accounts, and clean-up the other servers by recovering them from the same point in time.
As far as the specific question around ports:
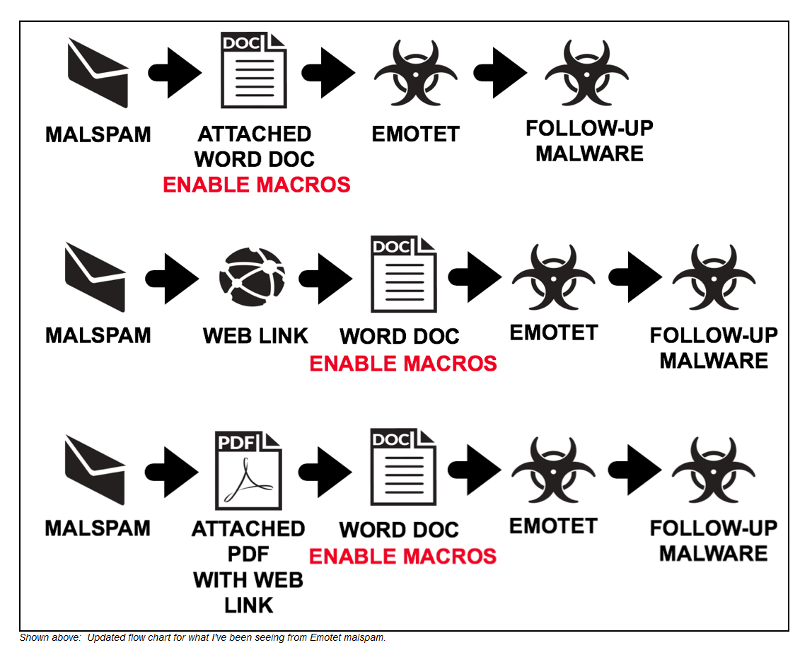 Image Credit: Malware-Traffic-Analysis
Image Credit: Malware-Traffic-Analysis
http://malware-traffic-analysis.net/ <-- This site has a lot of Packet Captures (PCaps) of various infections. We ended up blocking HTTP/HTTPS and Emotet's C&C ports along with exfiltration ports for all domain controllers by default.
Disable on Windows 10
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol -Restart
# Check
Get-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
# Check and Disable on Windows 7
Get-Item HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters | ForEach-Object {Get-ItemProperty $_.pspath}
# Disable SMBv1 on Windows 7
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 -Force
Restart-Computer
# Disable on Windows Server 2012 RTM
# Check
Get-SmbServerConfiguration | Select-Object EnableSMB1Protocol
# Disable
Set-SmbServerConfiguration -EnableSMB1Protocol $false -Confirm:$FalseIf the domain controllers were compromised then the domain is considered pwned. There is no more trust there!
We worked with a situation where we needed to step the PDCe back to prior to the Emotet infection, create new domain admin accounts, and clean-up the other servers by recovering them from the same point in time.
As far as the specific question around ports:
http://malware-traffic-analysis.net/ <-- This site has a lot of Packet Captures (PCaps) of various infections. We ended up blocking HTTP/HTTPS and Emotet's C&C ports along with exfiltration ports for all domain controllers by default.
This mechanism requires SMB and WMI.Just configure the allowed remote IP, all others will be blocked. Secure connections require a CA to configure IPSEC
This might be useful
https://www.experts-exchange.com/articles/31687/Windows-Firewall-as-Code.html
ASKER
As far as the DC's being compromised - we had 1 of 4 in the affected sub net. It's been decommissioned and we demoted the Administrator account, and changed passwords across the board. Is this good enough? It's been a few months, and our IDS hasn't kicked off anymore alerts to C&C servers.
Ouch. :(
Make sure all Admin accounts are audited for access! Make sure there's an automatic audit for rogue admins too.
We would have stepped the domain PDCe back via restore, set up new VMs for the replacement DCs, promoted them in, and then deployed them to the requisite sites.
Being aware of what's happening on the domain network is now all the more important.
Make sure all Admin accounts are audited for access! Make sure there's an automatic audit for rogue admins too.
We would have stepped the domain PDCe back via restore, set up new VMs for the replacement DCs, promoted them in, and then deployed them to the requisite sites.
Being aware of what's happening on the domain network is now all the more important.
ASKER
I'm shipping audit logs to a syslog server. We've also augmented our current anti-virus with Cisco AMP.
Our main issue has been we've seen a huge increase in spam email containing malware directed at us (and spoofed ones from us)- probably because Outlook contacts got scrapped on a number of machines.
Still - I gotta figure out the SMB firewall rules to get patch manager up, like you said, our best defense is making sure we are up to date with patches.
Our main issue has been we've seen a huge increase in spam email containing malware directed at us (and spoofed ones from us)- probably because Outlook contacts got scrapped on a number of machines.
Still - I gotta figure out the SMB firewall rules to get patch manager up, like you said, our best defense is making sure we are up to date with patches.
SPF, DMARC, and DKIM are the way forward. The first is mandatory while the second two take some work. With all three in place almost all phishing attempts against your org and others goes away.
ASKER
SPF is implemented - we are looking into DMARC and DKIM. Thanks for your responses. I'm actually doing some test deployments with the Firewall rules this evening - looking into it more, seems I needed to export policy from both Windows 10 and 7, and apply each policy to corresponding OS's.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I got the GPO working doing the following:
Created two GPO's - one for Windows 7 that I created on a windows 7 machine then imported the config from there, then the same process with windows 10
I used scope and allowed from remote IP
Then I used WMI and filtered for Windows 10 desktops and Windows 7 on the corresponding GPO policies.
Thanks for the help!
Created two GPO's - one for Windows 7 that I created on a windows 7 machine then imported the config from there, then the same process with windows 10
I used scope and allowed from remote IP
Then I used WMI and filtered for Windows 10 desktops and Windows 7 on the corresponding GPO policies.
Thanks for the help!
As a note: If "Authenticated Users" was removed from the SCOPE tab make sure to add it back to the SECURITY tab with READ permissions. That way there will be no issues reading at the machine level.