Cisco ASA 5505 to 5520 layer 3 tunnel
How to configure a ipsec tunnel between a Cisco ASA 5520 and a Cisco ASA 5505?
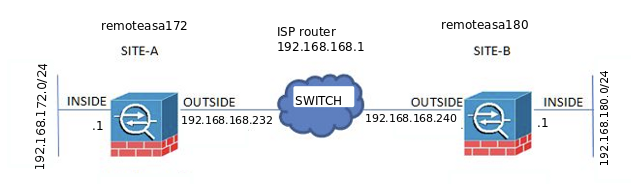 ==========================
==========================
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
: ASA Version 9.1(7)32
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 182.168.172.0 255.255.255.0 192.168.180.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.180.0 255.255.255.0 192.168.168.240 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 80 match address LAN_Traffic
crypto map CMAP 80 set peer 192.168.168.240
crypto map CMAP 80 set ikev1 transform-set TS
crypto map enable interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
dhcpd dns 192.168.168.1
dhcpd lease 3000
dhcpd ping_timeout 20
dhcpd domain mydomain.com
dhcpd option 3 ip 192.168.172.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examp
!
dhcpd address 192.168.172.3-192.168.172.
dhcpd enable inside
!
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa172#
==========================
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
: ASA Version 9.2(4)5
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 192.168.180.0 255.255.255.0 192.168.172.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.172.0 255.255.255.0 192.168.168.232 1
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
dhcpd dns 192.168.168.1
dhcpd ping_timeout 20
dhcpd domain myudomain.com
dhcpd auto_config outside
dhcpd option 3 ip 192.168.180.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examp
!
dhcpd address 192.168.180.3-192.168.180.
dhcpd enable inside
!
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa180#
 ==========================
==========================remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
: ASA Version 9.1(7)32
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 182.168.172.0 255.255.255.0 192.168.180.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.180.0 255.255.255.0 192.168.168.240 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 80 match address LAN_Traffic
crypto map CMAP 80 set peer 192.168.168.240
crypto map CMAP 80 set ikev1 transform-set TS
crypto map enable interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
dhcpd dns 192.168.168.1
dhcpd lease 3000
dhcpd ping_timeout 20
dhcpd domain mydomain.com
dhcpd option 3 ip 192.168.172.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examp
!
dhcpd address 192.168.172.3-192.168.172.
dhcpd enable inside
!
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa172#
==========================
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
: ASA Version 9.2(4)5
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 192.168.180.0 255.255.255.0 192.168.172.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.172.0 255.255.255.0 192.168.168.232 1
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
dhcpd dns 192.168.168.1
dhcpd ping_timeout 20
dhcpd domain myudomain.com
dhcpd auto_config outside
dhcpd option 3 ip 192.168.180.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examp
!
dhcpd address 192.168.180.3-192.168.180.
dhcpd enable inside
!
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa180#
ASKER
Hi atlas_shuddered, thanks for your reply, I wiped my ASAs and entered the configuration that you gave me. The 5505 will not put an ip addr on the interface, it says to put it in a vlan. It all went in without an error but I still get nothing..
COMPLETE CONFIGURATIONS
-----------------=========
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172# sh run
: Saved
:
: Serial Number: JMX1519L0A3
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
:
ASA Version 9.1(7)32
!
hostname remoteasa172
domain-name cortana.com
enable password N7HlIItY8AVJppkQ encrypted
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
nameif mngt
security-level 0
ip address 10.10.10.12 255.255.255.224
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name cortana.com
object-group network local-network
network-object 192.168.172.0 255.255.255.0
object-group network remote-network
network-object 192.168.180.0 255.255.255.0
access-list asa-router-vpn extended permit ip object-group local-network object-group remote-network
pager lines 24
logging enable
logging timestamp
logging monitor debugging
logging buffered informational
logging asdm informational
mtu management 1500
mtu outside 1500
mtu inside 1500
mtu mngt 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
icmp permit any mngt
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 10 match address asa-router-vpn
crypto map outside_map 10 set peer 192.168.168.240
crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA
crypto map outside_map interface outside
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.168.0 255.255.255.0 outside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd ping_timeout 20
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username ahuffman password J6PHrYG.ftfCg3oL encrypted
username cisco password 73ozQQQ.JMBHDyQz encrypted
tunnel-group 192.168.168.240 type ipsec-l2l
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:9865e29590e
: end
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
-----------------=========
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180# sh run
: Saved
:
: Serial Number: JMX1650Z14E
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
:
ASA Version 9.2(4)5
!
hostname remoteasa180
domain-name cortana.com
enable password N7HlIItY8AVJppkQ encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
shutdown
no nameif
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
shutdown
no nameif
security-level 0
ip address dhcp setroute
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name cortana.com
object network obj_any
subnet 0.0.0.0 0.0.0.0
object-group network local-network
network-object 192.168.180.0 255.255.255.0
object-group network remote-network
network-object 192.168.172.0 255.255.255.0
access-list asa-router-vpn extended permit ip object-group local-network object-group remote-network
pager lines 24
logging enable
logging timestamp
logging buffered informational
logging asdm informational
mtu inside 1500
mtu outside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 10 match address asa-router-vpn
crypto map outside_map 10 set peer 192.168.168.232
crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA
crypto map outside_map interface outside
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.180.0 255.255.255.0 inside
ssh 192.168.168.0 255.255.255.0 outside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd ping_timeout 20
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 73ozQQQ.JMBHDyQz encrypted
!
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:cc8ddafec7f
: end
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
COMPLETE CONFIGURATIONS
-----------------=========
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172# sh run
: Saved
:
: Serial Number: JMX1519L0A3
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
:
ASA Version 9.1(7)32
!
hostname remoteasa172
domain-name cortana.com
enable password N7HlIItY8AVJppkQ encrypted
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
nameif mngt
security-level 0
ip address 10.10.10.12 255.255.255.224
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name cortana.com
object-group network local-network
network-object 192.168.172.0 255.255.255.0
object-group network remote-network
network-object 192.168.180.0 255.255.255.0
access-list asa-router-vpn extended permit ip object-group local-network object-group remote-network
pager lines 24
logging enable
logging timestamp
logging monitor debugging
logging buffered informational
logging asdm informational
mtu management 1500
mtu outside 1500
mtu inside 1500
mtu mngt 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
icmp permit any mngt
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 10 match address asa-router-vpn
crypto map outside_map 10 set peer 192.168.168.240
crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA
crypto map outside_map interface outside
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.168.0 255.255.255.0 outside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd ping_timeout 20
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username ahuffman password J6PHrYG.ftfCg3oL encrypted
username cisco password 73ozQQQ.JMBHDyQz encrypted
tunnel-group 192.168.168.240 type ipsec-l2l
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:9865e29590e
: end
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
-----------------=========
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180# sh run
: Saved
:
: Serial Number: JMX1650Z14E
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
:
ASA Version 9.2(4)5
!
hostname remoteasa180
domain-name cortana.com
enable password N7HlIItY8AVJppkQ encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
shutdown
no nameif
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
shutdown
no nameif
security-level 0
ip address dhcp setroute
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name cortana.com
object network obj_any
subnet 0.0.0.0 0.0.0.0
object-group network local-network
network-object 192.168.180.0 255.255.255.0
object-group network remote-network
network-object 192.168.172.0 255.255.255.0
access-list asa-router-vpn extended permit ip object-group local-network object-group remote-network
pager lines 24
logging enable
logging timestamp
logging buffered informational
logging asdm informational
mtu inside 1500
mtu outside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static local-network local-network destination static remote-network remote-network no-proxy-arp route-lookup
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 10 match address asa-router-vpn
crypto map outside_map 10 set peer 192.168.168.232
crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA
crypto map outside_map interface outside
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.180.0 255.255.255.0 inside
ssh 192.168.168.0 255.255.255.0 outside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd ping_timeout 20
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 73ozQQQ.JMBHDyQz encrypted
!
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:cc8ddafec7f
: end
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
Try this on the 5505. I hope I got the right one. Check the interface IPs and if they aren't correct to the 5505 let me know and I will update:
interface Vlan1
shutdown
no nameif
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 192.168.168.232
!
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
!
crypto ipsec transform-set L2L esp-aes-256 esp-sha-hmac
!
access-list LAN_Traffic extended permit ip 192.168.180.0 255.255.255.0 192.168.172.0.0 255.255.255.0
!
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
pre-shared-key WhateverYouSetThisTo
!
crypto map L2L 1 match address LAN_Traffic
crypto map L2L 1 set peer 192.168.168.232
crypto map L2L 1 set transform-set L2L
!
crypto map L2L interface outside
And on the 5520:
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.720.0 255.255.255.0
!
crypto isakmp policy 1
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
!
crypto ikev1 enable outside
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
pre-shared-key WhateverYouSetThisTo
!
object-group network local-network
network-object 192.168.172.0 255.255.255.0
object-group network remote-network
network-object 192.168.180.0 255.255.255.0
!
access-list asa-router-vpn extended permit ip object-group local-network
object-group remote-network
!
nat (inside,outside) source static local-network local-network destination
static remote-network remote-network no-proxy-arp route-lookup
!
access-list INTERESTING permit ip 192.168.172.0 255.255.255.0 192.168.180.0 255.255.255.0
crypto ipsec ikev1 transform-set ESP-AES128-SHA esp-aes esp-sha-hmac
crypto map VPN-MAP 10 match address INTERESTING
crypto map VPN-MAP 10 set peer 192.168.168.240
crypto map VPN-MAP 10 set ikev1 transform-set ESP-AES128-SHA
crypto map VPN-MAP interface outsideThis question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
ASA172
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
object-group network local-network
network-object 192.168.172.0 255.255.255.0
object-group network remote-network
network-object 192.168.180.0 255.255.255.0
!
access-list asa-router-vpn extended permit ip object-group local-network
object-group remote-network
!
nat (inside,outside) source static local-network local-network destination
static remote-network remote-network no-proxy-arp route-lookup
!
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
!
crypto map outside_map 10 match address asa-router-vpn
crypto map outside_map 10 set peer 192.168.168.240
crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA
crypto map outside_map interface outside
++++++++++++++++++++++++++
++++++++++++++++++++++++++
ASA180
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.180.0 255.255.255.0
!
object-group network local-network
network-object 192.168.180.0 255.255.255.0
object-group network remote-network
network-object 192.168.172.0 255.255.255.0
!
access-list asa-router-vpn extended permit ip object-group local-network
object-group remote-network
!
nat (inside,outside) source static local-network local-network destination
static remote-network remote-network no-proxy-arp route-lookup
!
crypto ipsec ikev1 transform-set ESP-AES-SHA esp-aes esp-sha-hmac
!
crypto map outside_map 10 match address asa-router-vpn
crypto map outside_map 10 set peer 192.168.168.232
crypto map outside_map 10 set ikev1 transform-set ESP-AES-SHA
crypto map outside_map interface outside