xpandit
asked on
Yealink T48S phones download a CA certificate even when disabled
Skype for business 2015 Yealink T48S | Trusted Certificate
I need assistance with phones we recently purchased, all T48S handsets with Skype for business firmware.
I have tried all 3 latest available firmware and stuck with this version as it offered a simpler login screen for users.

Scenario:
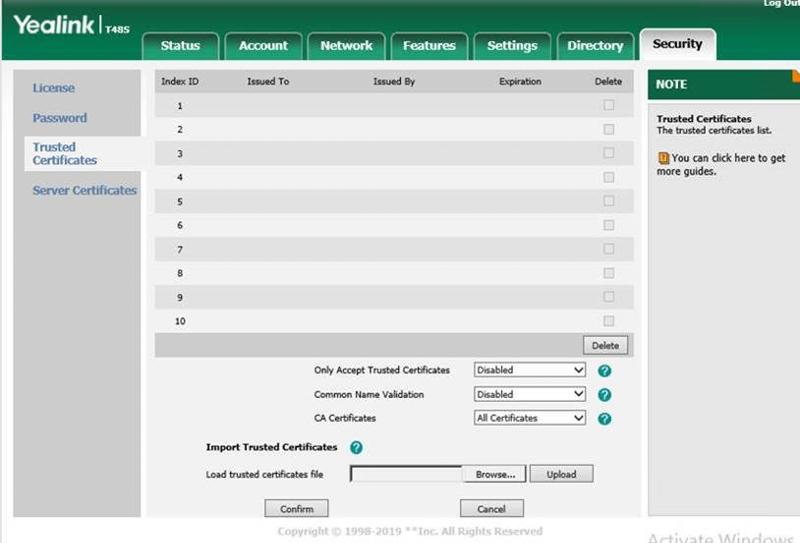
Phones register correctly for as long as the the trusted certificate is not present.
Periodically the handsets will populate with a CA certificate on line 1 even though everything is set to disabled below and then the users are unable to sign into the phones.
i did some googling and found this command but its only relevant for SKype for Business online
https://docs.microsoft.com/en-us/powershell/module/skype/set-csipphonepolicy?view=skype-ps
What is causing the phones to download the internal root domain CA certificate?
I need assistance with phones we recently purchased, all T48S handsets with Skype for business firmware.
I have tried all 3 latest available firmware and stuck with this version as it offered a simpler login screen for users.

Scenario:
Phones register correctly for as long as the the trusted certificate is not present.
Periodically the handsets will populate with a CA certificate on line 1 even though everything is set to disabled below and then the users are unable to sign into the phones.

i did some googling and found this command but its only relevant for SKype for Business online
https://docs.microsoft.com/en-us/powershell/module/skype/set-csipphonepolicy?view=skype-ps
What is causing the phones to download the internal root domain CA certificate?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I have exactly the same problem you had, could you please help me and tell me how you solved it?
I already tried the masnrock solution, but it didn't work
Thank you.
I already tried the masnrock solution, but it didn't work
Thank you.
The first setting is for Only Accept Trusted Certificates. The wording is the key here, it says nothing about refusing all certificates.
Straight from the T48S admin guide with respect to that setting:
The second setting where you chose Disabled is Common Name Validation. This just gets into whether or not it will validate the Common Name on the certificate. Since you chose Disabled, it will simply skip the step of validating the Common Name.
From the admin guide for the T48S:
Basically, it's always going to download this. What it does with it depends on your phone settings.
You might have to tweak the settings to something like this:
Only Accept Trusted Certificates: Enabled
CA Certificates: Default Certificates.
Also, delete that internal CA certificate from the phone.
That should prevent the phone from looking internal CA certificate, and also make the phone look solely at the built in trusted certificates list (which should remain empty).