Rick_Penney
asked on
Best Practice Management of HP Pro Curve and Cisco switches
Hi, I am after some advice on management vlans on HP Procurve 2920 24POE switches please.
Our switches currently have 2 vlans, both vlans (vlan 1 and vlan2) are being used for data.
The ip address and management of the switch was set via the setup tool so its being managed over vlan1
For security I plan to set up vlan 100 on port 24 to use for management purposes, the switches will all plug back into a cisco 2950 switch
We also have a few Cisco 2960 switches which I will also setup Vlan 100 and plug back into the Cisco 2950
Is this the best way to set up the management vlan on the HPs, or should I use the Front Management port that is present on the HP 2920s and plug all these back into my Cisco 2950 switch?
A quick google shows commands on how to enable the oobm management port, however it says
OOBM is not compatible with a management VLAN. If you attempt to enable OOBM when a management VLAN is enabled, the command will be rejected and you will receive an error message.
If an OOBM IP address exists and you disable OOBM, the OOBM IP address configuration is maintained. If you enable OOBM and there is a pre-existing OOBM IP address, it will be reinstated. Network OOBM is enabled by default.
Does this just mean that no other vlan interface can have an IP Address set against it?
If this is the case, can I still assign a vlan id of vlan 100 to the oobm, so that the Cisco 2960s can also be managed?
Hope that made sense?
Update:
On drawing it out, see attached file, for me to be able to manage these switches using the management IP Addresses on vlan100 from my PC that will be on vlan 1, if I use the Cisco 2950 switch previously mentioned, I think I will be in one big STP loop.
Therefore, is the best solution to keep the vlans as mentioned, but discard the cisco 2950 management switch and just tag the ports to allow all vlans?
regards
Rick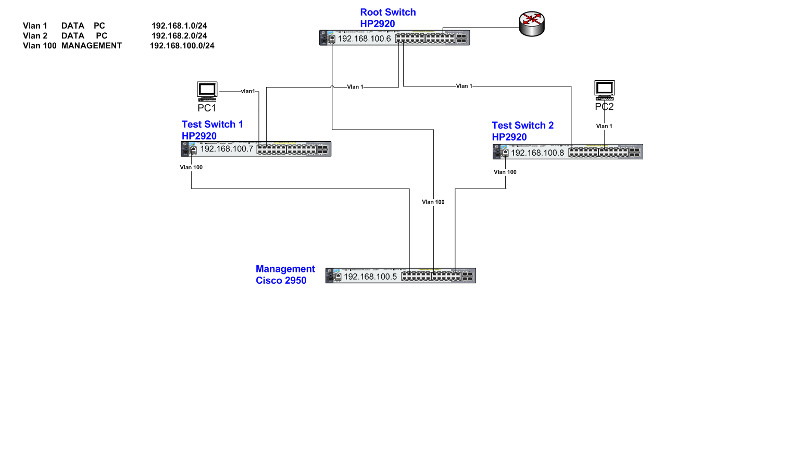
Our switches currently have 2 vlans, both vlans (vlan 1 and vlan2) are being used for data.
The ip address and management of the switch was set via the setup tool so its being managed over vlan1
For security I plan to set up vlan 100 on port 24 to use for management purposes, the switches will all plug back into a cisco 2950 switch
We also have a few Cisco 2960 switches which I will also setup Vlan 100 and plug back into the Cisco 2950
Is this the best way to set up the management vlan on the HPs, or should I use the Front Management port that is present on the HP 2920s and plug all these back into my Cisco 2950 switch?
A quick google shows commands on how to enable the oobm management port, however it says
OOBM is not compatible with a management VLAN. If you attempt to enable OOBM when a management VLAN is enabled, the command will be rejected and you will receive an error message.
If an OOBM IP address exists and you disable OOBM, the OOBM IP address configuration is maintained. If you enable OOBM and there is a pre-existing OOBM IP address, it will be reinstated. Network OOBM is enabled by default.
Does this just mean that no other vlan interface can have an IP Address set against it?
If this is the case, can I still assign a vlan id of vlan 100 to the oobm, so that the Cisco 2960s can also be managed?
Hope that made sense?
Update:
On drawing it out, see attached file, for me to be able to manage these switches using the management IP Addresses on vlan100 from my PC that will be on vlan 1, if I use the Cisco 2950 switch previously mentioned, I think I will be in one big STP loop.
Therefore, is the best solution to keep the vlans as mentioned, but discard the cisco 2950 management switch and just tag the ports to allow all vlans?
regards
Rick

ASKER
Thank you for your reply, its much appreciated. If i set them up as access ports, does that mean that I would have to plug my laptop into the Cisco 2950 to manage all the switches over vlan 100?
The two reasons I have for needing to manage them from a laptop on vlan 1 is for upgrading firmware out of hours whilst vpn'd in from home, and also that I didn't mention, we have 3 physical locations that it would be helpful to be able to manage them over the WAN
kind regards
Rick
The two reasons I have for needing to manage them from a laptop on vlan 1 is for upgrading firmware out of hours whilst vpn'd in from home, and also that I didn't mention, we have 3 physical locations that it would be helpful to be able to manage them over the WAN
kind regards
Rick
you could build a trunk link back to the switch that you are connected to (meaning you would have two connections between - one for your management connection and one for the prod side. So in this case your traffic would go from your PC to your local switch, up a trunk on vlan X to the 2950, routed on the 2950 from vlan X to vlan 100, then back down the access link back to your switch for management.
Having said all this, I want to point out that this is the scenario for how you are saying you want things to look but it is not how I would build out your switch management based on how you have communicated your environment.
Having said all this, I want to point out that this is the scenario for how you are saying you want things to look but it is not how I would build out your switch management based on how you have communicated your environment.
ASKER
Thank you, i'm conscious i've taken a lot of your time, i follow what you are saying but also how would you do it.
The diagram is just a test bed, but in production each of our three physical sites has a root switch connected to approx 10 other switches.
We have two vlans, one for office clients on vlan 1 (7 switches), the other in the workshop vlan 2 (3 switches)
Every device regardless of vlan needs to see all devices in both vlans. (sort of defeats the object but there is a reason for it).
The router that the root switch connects to has sub interfaces for each subnet and is doing the routing between subnets.
All is working ok and remote management is done over vlan1, i'm only looking to change the management from a security point of view
regards.
The diagram is just a test bed, but in production each of our three physical sites has a root switch connected to approx 10 other switches.
We have two vlans, one for office clients on vlan 1 (7 switches), the other in the workshop vlan 2 (3 switches)
Every device regardless of vlan needs to see all devices in both vlans. (sort of defeats the object but there is a reason for it).
The router that the root switch connects to has sub interfaces for each subnet and is doing the routing between subnets.
All is working ok and remote management is done over vlan1, i'm only looking to change the management from a security point of view
regards.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Many thanks for all your time and help with this, its much appreciated.
kind regards, Rick
kind regards, Rick
No worries. Cheers
Unless you are going to drop the 2950 behind a firewall then I would just go with your first idea. Simpler in the log run.