fyrfyter88
asked on
Watchguard Firewall with two interfaces not allowing VOIP phone to connect
My current setup is this- I use a Watchguard firewall.
Interface 0 is external.
Interface 1 is trusted-192.168.1.1/24
Interface 2 is trusted-192.168.3.1/24
There is a VPN to another office that is 192.168.2.1/24
Our phone system is 192.168.1.5
If I plug a phone into the .2 network the phone will connect up without an issue.
If I plug a phone into the .3 network the phone will NOT connect up.
I assume there needs to be a policy in place to get the two to talk. I am unsure of what the policy needs to be.
Interface 0 is external.
Interface 1 is trusted-192.168.1.1/24
Interface 2 is trusted-192.168.3.1/24
There is a VPN to another office that is 192.168.2.1/24
Our phone system is 192.168.1.5
If I plug a phone into the .2 network the phone will connect up without an issue.
If I plug a phone into the .3 network the phone will NOT connect up.
I assume there needs to be a policy in place to get the two to talk. I am unsure of what the policy needs to be.
Either ensure the phone gets a fixed address and allow traffic from that address -> PBX on all ports.
Or ensure SIP, SIPS, and relevant RTP ports are allowed. SIP = 5060 (TCP or UDP) SIPS = (5061, UDP),RTP ports should be configured in the phone and in the PBX.
so the may vary. Those are always UDP.
Or ensure SIP, SIPS, and relevant RTP ports are allowed. SIP = 5060 (TCP or UDP) SIPS = (5061, UDP),RTP ports should be configured in the phone and in the PBX.
so the may vary. Those are always UDP.
ASKER
If I am on the .3 network I can ping the phone system on the .1 network. I cannot connect to the phone system via the browser, however. I have attached a pic of my current rule. The 1. network and the 3. network are on the same watchguard different interfaces (FYI). The 1. and the 2. network are VPN between two watchguards (FYI).
I have tried to create a rule that has the "from" the .3 interface and the "to" as a voip.SNAT as shown in the current poicy. That did not work.
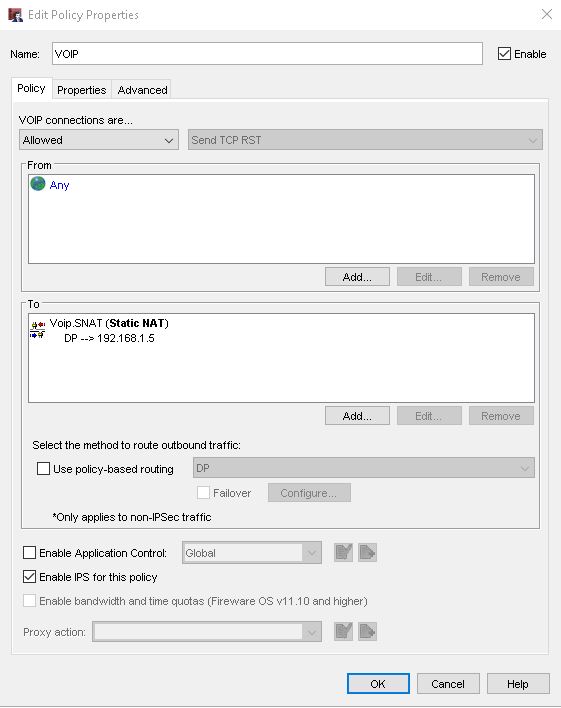
I have tried to create a rule that has the "from" the .3 interface and the "to" as a voip.SNAT as shown in the current poicy. That did not work.
If the 192.168.1.1/24 and 192.168.2.1/24 are connected via VPN tunnel and you are wanting to get the two to talk to each other, sounds like you don't need to create a policy, but rather fix your routing.
So create a static route that says:
Destination: 192.168.2.0/24
Gateway: [VPN Tunnel Address]
If you create that on the 192.168.1.1/24 Firewall, it will allow that network to communicate to 192.168.2.0/24 or at least know where to send it.
You may need to create a policy after that to actually allow 192.168.1.0/24 to talk to 192.168.2.0/24
So create a static route that says:
Destination: 192.168.2.0/24
Gateway: [VPN Tunnel Address]
If you create that on the 192.168.1.1/24 Firewall, it will allow that network to communicate to 192.168.2.0/24 or at least know where to send it.
You may need to create a policy after that to actually allow 192.168.1.0/24 to talk to 192.168.2.0/24
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
I recommend looking at the rules between the .1 and .2 networks. Check to see what is different there. Should help narrow things down pretty fast.
What subnet do the phones get their IP addresses from? Could even be something related to DHCP. A missing DHCP option for the .3 network is one example.