Problem with multi-tenant Exchange setup and certificates
Hello. We have an Exchange 2010 server with a wildcard SSL certificate covering a particular domain, let's call it main.exa.
The server is multi-tenant, so it covers more than one e-mail domain. Let's call the other domains test1.exa and test2.exa.
These other domains are not certified, but we are redirecting autodiscover.test1.exa and autodiscover.test2.exa to autodiscover.main.exa. There are guides online to do this, but this doesn't seem to work.
What happens is, if I connect Outlook from an external PC to an address from test1 or test2, I'll always get a certificate warning saying for instance test1.exa doesn't have a certificate.
I was wondering if someone can shed any light on this conundrum. Thanks.
The server is multi-tenant, so it covers more than one e-mail domain. Let's call the other domains test1.exa and test2.exa.
These other domains are not certified, but we are redirecting autodiscover.test1.exa and autodiscover.test2.exa to autodiscover.main.exa. There are guides online to do this, but this doesn't seem to work.
What happens is, if I connect Outlook from an external PC to an address from test1 or test2, I'll always get a certificate warning saying for instance test1.exa doesn't have a certificate.
I was wondering if someone can shed any light on this conundrum. Thanks.
ASKER
The wildcard only covers the first domain, but all the domains are managed by the same Exchange server. I am trying to redirect autodiscovery to the certified domain via DNS, since I read it should work. It doesn't though.
This is one of the guides I followed:
https://social.technet.microsoft.com/wiki/contents/articles/5787.exchange-2010-multi-tenant-autodiscover-and-dns-configuration.aspx
This is one of the guides I followed:
https://social.technet.microsoft.com/wiki/contents/articles/5787.exchange-2010-multi-tenant-autodiscover-and-dns-configuration.aspx
OK, I think the CNAME is creating issues
All you can do is:
skip CNAME record - its not required
point autodiscover.test1.exa to IIS redirection server public IP address
On IIS server configure redirection to https://mail.domain.com/autodiscover URL
OR
use SRV record method which will be more accurate and simple in this case
All you can do is:
skip CNAME record - its not required
point autodiscover.test1.exa to IIS redirection server public IP address
On IIS server configure redirection to https://mail.domain.com/autodiscover URL
OR
use SRV record method which will be more accurate and simple in this case
You can have one common name and one autodiscover name in certificate and redirect.
please check this article on how to configure multidomain in Exchange 2010.
https://www.experts-exchange.com/articles/29657/Exchange-2010-Fix-for-an-Invalid-certificate-and-related-issues.html
please check this article on how to configure multidomain in Exchange 2010.
https://www.experts-exchange.com/articles/29657/Exchange-2010-Fix-for-an-Invalid-certificate-and-related-issues.html
Hi there,
The problem
you have 3 domains:
main.exa. (autodiscover.main.exa)
test1.exa ((autodiscover.main.exa)
test2.exa (autodiscover.test2.exa)
in here you are using incorrectly the record "autodiscover".
If you have only one wildcard, let's say: *.main.exa
Then you would use only two records, no matter how many domains you have or will have.
This records are:
For the other domains:
test1.exa and test2.exa
Will use an "autodiscover method" that uses your principal certificate, but WON'T BE "Autodiscover.<domain>"
You will use a called SVR Record method for each domain, in your internal DNS if you want and/or your Public DNS (registrar).
Here's an example
https://www.a2hosting.com/kb/getting-started-guide/configuring-domain-settings/adding-an-srv-record-to-a-domain
Create Record.
Service: _autodiscover
Protocol: _tcp
Priority: 100
Weight: 1
Port: 443
Target (Hostname): <whatever>.main.exa (following example : mail.main.exa)
And that's all you need ...
Footnote: All your users from test1.exa and test2.exa will be asked with this question:
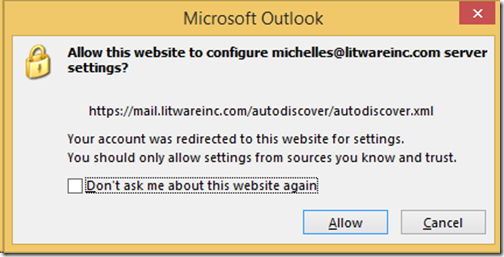
https://markgossa.blogspot.com/2015/11/exchange-2013-2016-autodiscover-srv-record.html
Another alternative is to get an Expensive certificate that allows you 6 Subject Alternative Names (6 Sans, why 6? the formula is #domains x 2, in this case, #domains is 3, so 3x2 = 6.)
Those records would be:
And you can use any of those as principal :)
The problem
you have 3 domains:
main.exa. (autodiscover.main.exa)
test1.exa ((autodiscover.main.exa)
test2.exa (autodiscover.test2.exa)
in here you are using incorrectly the record "autodiscover".
If you have only one wildcard, let's say: *.main.exa
Then you would use only two records, no matter how many domains you have or will have.
This records are:
- <whatever>.main.exa (ex: mail.main.exa)
- autodiscover.main.exa
For the other domains:
test1.exa and test2.exa
Will use an "autodiscover method" that uses your principal certificate, but WON'T BE "Autodiscover.<domain>"
You will use a called SVR Record method for each domain, in your internal DNS if you want and/or your Public DNS (registrar).
Here's an example
https://www.a2hosting.com/kb/getting-started-guide/configuring-domain-settings/adding-an-srv-record-to-a-domain
Create Record.
Service: _autodiscover
Protocol: _tcp
Priority: 100
Weight: 1
Port: 443
Target (Hostname): <whatever>.main.exa (following example : mail.main.exa)
And that's all you need ...
Footnote: All your users from test1.exa and test2.exa will be asked with this question:

https://markgossa.blogspot.com/2015/11/exchange-2013-2016-autodiscover-srv-record.html
Another alternative is to get an Expensive certificate that allows you 6 Subject Alternative Names (6 Sans, why 6? the formula is #domains x 2, in this case, #domains is 3, so 3x2 = 6.)
Those records would be:
- autodiscover.main.exa
- autodiscover.test1.exa
- autodsicover.test2.exa
- mail.main.exa
- mail.test1.exa
- mail.test2.exa
And you can use any of those as principal :)
The Microsoft-recommended way is to setup an separate HTTP website that redirects to your HTTPS autodiscover (this is how O365 works).
You create a CNAME record to this address (which doesn't require a cert) which only exists to perform a 301 redirect to the FQDN of your HTTPS version (which has a matching SSL cert).
All works fine.
Note: Always choose generic, non-client specific FQDNs/SSLs for your multitenanted systems.
Note: if the http FQDN isn't something you want to share with clients, you can create an A record instead of a CNAME,but the CNAME method is the recommended way from Microsoft.
Note: The HTTP & HTTPS websites cannot be on the same external IP address.
You create a CNAME record to this address (which doesn't require a cert) which only exists to perform a 301 redirect to the FQDN of your HTTPS version (which has a matching SSL cert).
All works fine.
Note: Always choose generic, non-client specific FQDNs/SSLs for your multitenanted systems.
Note: if the http FQDN isn't something you want to share with clients, you can create an A record instead of a CNAME,but the CNAME method is the recommended way from Microsoft.
Note: The HTTP & HTTPS websites cannot be on the same external IP address.
ASKER
We have tried most suggestions, but nothing has worked. We are still trying, I'll report back soon.
Probably, Daniele, you're doing something wrong, tell us what you've done so we can follow you :)
scenario is not that complicated as you think
I already given you couple of valid suggestions
I don't know what exactly if you are attempted?
I already given you couple of valid suggestions
I don't know what exactly if you are attempted?
ASKER
I will be back to this at the end of next week, then I'll report with more details.
We have tried most suggestions, but nothing has worked. We are still trying, I'll report back soon.We need more info than that to be able to assist you.
Please advise what you have tried and what occurred, including error messages etc.
ASKER
So I'm back here after a while. Nothing worked, so we opted for separate certificates and we are going with those for the moment. Not really a solution, but we don't have time to go deeper.
ASKER
So I'm back here after a while. Nothing worked, so we opted for separate certificates and we are going with those for the moment. Not really a solution, but we don't have time to go deeper.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I mean it would cover one level only
If test1.exa and test2.exa are two domains, wildcard can't cover both domains?
It can cover name1.test1.exa, name2. test1.com and so on
It seems issue exists with wildcard certificate