Configuring the Windows Firewall Service by GPO - a Couple of Questions
Hi all,
We are switching to using the Windows Firewall for clients after using Sophos for many years. At the moment I am configuring a GPO and have a couple of queries.
1.) How can I stop or restart the Windows Firewall service?
I have noticed that when I go to services and look at Windows Defender Firewall, everything is greyed out and I have no option to stop or restart it (yes, I am running services with admin credentials). If I run Task Manager as administrator and access services this way, when I attempt to stop with Windows Defender Firewall service I get:
The operation could not be completed. Access denied.
2.) Problems with logging.
a.) I have enabled logging in the GPO. I left it with the default %windir%\system32\logfiles
b.) I quite like the idea of changing the path where the log file saves to a central shared location. I was thinking of using a %computername% variable in the file name to save a different file for each computer.
is this possible?
Thanks in advance
We are switching to using the Windows Firewall for clients after using Sophos for many years. At the moment I am configuring a GPO and have a couple of queries.
1.) How can I stop or restart the Windows Firewall service?
I have noticed that when I go to services and look at Windows Defender Firewall, everything is greyed out and I have no option to stop or restart it (yes, I am running services with admin credentials). If I run Task Manager as administrator and access services this way, when I attempt to stop with Windows Defender Firewall service I get:
The operation could not be completed. Access denied.
2.) Problems with logging.
a.) I have enabled logging in the GPO. I left it with the default %windir%\system32\logfiles
b.) I quite like the idea of changing the path where the log file saves to a central shared location. I was thinking of using a %computername% variable in the file name to save a different file for each computer.
is this possible?
Thanks in advance
ASKER
Ah
That's group policy that's disabled it, if you have a current policy (i'm guessing sophos) it'll gray it out and prevent any changes as it's being managed by an alternative source. I.E GPO, McAfee, Sophos etc etc.
Hence why you can't change it.
Regards
Alex
That's group policy that's disabled it, if you have a current policy (i'm guessing sophos) it'll gray it out and prevent any changes as it's being managed by an alternative source. I.E GPO, McAfee, Sophos etc etc.
Hence why you can't change it.
Regards
Alex
ASKER
This is the strange thing. I have the same policy pointing to Windows 7 and Windows 10 machines.
I just noticed that on my Windows 7 test machine I can start and stop the service manually (as long as I run services as administrator), but on the Windows 10 machine, I cannot.
I am fairly sure they have the same set of policies assigned to them.
Regarding problem 2.), I tried changing the log location to C:\pfirewall.log but the file is still not created.
I just noticed that on my Windows 7 test machine I can start and stop the service manually (as long as I run services as administrator), but on the Windows 10 machine, I cannot.
I am fairly sure they have the same set of policies assigned to them.
Regarding problem 2.), I tried changing the log location to C:\pfirewall.log but the file is still not created.
If the service is stopped, you'll lose network connectivity as a "Feature" in windows 7
Windows 10 has probably disabled that functionality completely.
Run RSOP.MSC as an admin and go through it that way and see what policy is applying.
It won't create it in the root of c:\ you need to put it into a folder because of UAC :)
Windows 10 has probably disabled that functionality completely.
Run RSOP.MSC as an admin and go through it that way and see what policy is applying.
It won't create it in the root of c:\ you need to put it into a folder because of UAC :)
ASKER
Do I need to create the 'logs' folder myself? Or should the policy create that folder path?
It "Should" create it on it's own, however for the purpose of testing, just make it to ensure it's there correctly.
ASKER
OK, I have made a bit of progress with this....
1.) I have set the GPO to create the file C:\firewall_log\pfirewall.
2.) The folder (c:\firewall_log) was not automatically being created so I configured the GPO to create the folder and also assign the MpsSvc user full permissions on the folder. As you can see in the screenshot below this has been successfully created.
3.) For testing, I have configured the GPO to log all dropped and successful packets.
As you can see below, the log file is now successful being created and it has added the heading to the pfirewall.log. However, it does not seem to be actually logging anything.
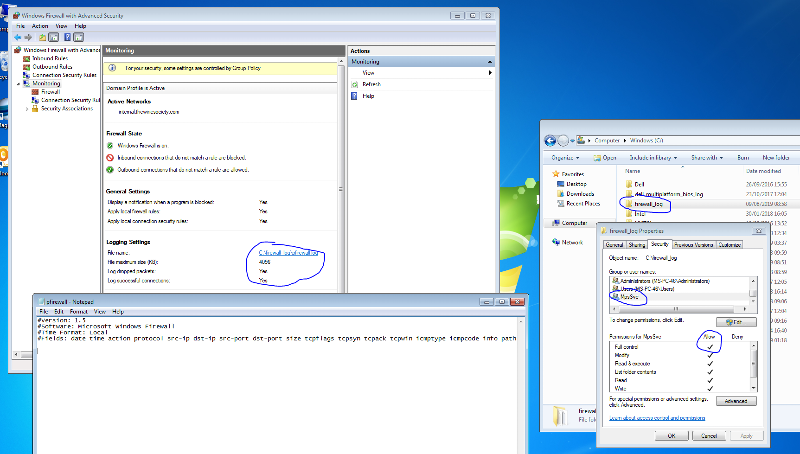
Any ideas why it is not actually logging the packets?
1.) I have set the GPO to create the file C:\firewall_log\pfirewall.
2.) The folder (c:\firewall_log) was not automatically being created so I configured the GPO to create the folder and also assign the MpsSvc user full permissions on the folder. As you can see in the screenshot below this has been successfully created.
3.) For testing, I have configured the GPO to log all dropped and successful packets.
As you can see below, the log file is now successful being created and it has added the heading to the pfirewall.log. However, it does not seem to be actually logging anything.
Any ideas why it is not actually logging the packets?
No is the short answer, maybe it's not dropped any packets, alternatively it would have made some connections and dropped them in there. I'd test by making connections to a server or something and see if that works. It could only be logging connections that are refused at a guess.
Sorry :(
Sorry :(
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
I'm assuming this is windows 10, that's by default. Go to
Control Panel\All Control Panel Items\Windows Defender Firewall
Stop it in there.
2.) Problems with logging.
Drop the logs into a top level folder in your C:\ I.E c:\logs and see if that works, then you'll know if it's a permissions issue or an issue with your group policy doing the logging.
Let me know how you get on.
Regards
Alex