A virus crypted all my personal data saved on my drives. How can I decrypt them ?
Hello to everyone,
while I was installing some software,I don't know where I have clicked,but something very bad is happened. I've activated a virus that has crypted a lot of important data saved on all the attached disks. The files after that they have been crypted appears like this :
autoexec.bat.id[0E9A1736-2
WhatsApp.lnk.id[0E9A1736-2
This is the message that I seen after some time :
what should I do now ? is there a way to decrypt these files ? I don't know how much money he wants,but I don't have money to give to him. I hope that someone can help me. thanks.
while I was installing some software,I don't know where I have clicked,but something very bad is happened. I've activated a virus that has crypted a lot of important data saved on all the attached disks. The files after that they have been crypted appears like this :
autoexec.bat.id[0E9A1736-2
WhatsApp.lnk.id[0E9A1736-2
This is the message that I seen after some time :
All you files have been encrypted due to a security problem with your PC. If you want to restore them, there are 2 ways of contact.
1. Jabber contact - recovermyfiles2019@thesecure.biz
- https://www.wikihow.com/Create-a-Jabber-Account
- https://psi-im.org/download/
- Once you created a jabber account. Make sure you add the contact first and wait for our approval to begin sending message.
- Directly messaging us with out accepting your request will result to Forbidden message
2. Bitmessage contact address- BM-2cVoXfF2BdYyfxBrady3hopZN6izutPyE r
- https://bitmessage.org/wiki/Main_Page
- After all the sync is finish. You can directly send message here.
Try both method of contact to ensure we receive your message.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of file must be less tthan 4mb(non achieved), and files should not contact valuable information. (databases, backups, large excel sheets, etc.)
Where to buy bitcoins?
* The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click
'Buy bitcoins', and select the seller by payment method and price:
https://localbitcoins.com/buy_bitcoins
* Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price
(they add their fee to our) or you can become a victim of a scam.
what should I do now ? is there a way to decrypt these files ? I don't know how much money he wants,but I don't have money to give to him. I hope that someone can help me. thanks.
Do you have any backups so you can just blow away your installation and restore things? Otherwise I think you are out of luck. Either you pay these hackers in the hopes they do decrypt your files, or blow away you installation and start fresh loosing all you data.
ASKER
no.
you're pretty much done, either pay the ransom or those files are gone. There is no known way of decrypting them.
if you are very, very lucky there might be a decryptor available. Kaspersky has a few https://noransom.kaspersky.com/
if you are very, very lucky there might be a decryptor available. Kaspersky has a few https://noransom.kaspersky.com/
google: Ransomware Decryptor
also returns other decryptors, e.g.
https://www.emsisoft.com/ransomware-decryption-tools/free-download
https://www.nomoreransom.org/en/decryption-tools.html
also returns other decryptors, e.g.
https://www.emsisoft.com/ransomware-decryption-tools/free-download
https://www.nomoreransom.org/en/decryption-tools.html
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Always have multiple backups with at least one copy that you don't keep connected all the time.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
To eradicate the virus is not enough to scan every drive with karspersky total security ?
Strictly this is not a virus so AV software may not detect it, you should look at running both anti-virus and anti-malware software.
The ADAME suffix to your files says this is a newer variant.
For the time being assume all your data is lost, it might be possible to recover in the future if someone cracks this specific variation and posts the details online so some experts suggest saving the encrypted data in case this happens.
Just a thought though if they are offering to decrypt 5 test files and return then you could set up a temporary email address and compare the encrypted and decrypted versions on a sandboxed machine. Panda offer an online comparison tool that might be able to extract the encryption key.
The ADAME suffix to your files says this is a newer variant.
For the time being assume all your data is lost, it might be possible to recover in the future if someone cracks this specific variation and posts the details online so some experts suggest saving the encrypted data in case this happens.
Just a thought though if they are offering to decrypt 5 test files and return then you could set up a temporary email address and compare the encrypted and decrypted versions on a sandboxed machine. Panda offer an online comparison tool that might be able to extract the encryption key.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Whats the best tool that i can install to detect It ?
while I was installing some software,I don't know where I have clicked,but something very bad is happened.What software were you installing and where did you download it from?
ASKER
Dont remember
You don't remember what software you were downloading or from where, so that makes it even tougher to figure out where your problem started from.
You don't have backups of your data, so that option is out.
So the next question is whether that can be replaced from another source easily. And what is that data worth to you?
So if you absolutely cannot be afford to be without the data you're left with only two choices:
You don't have backups of your data, so that option is out.
So the next question is whether that can be replaced from another source easily. And what is that data worth to you?
So if you absolutely cannot be afford to be without the data you're left with only two choices:
- Data recovery service - Expensive, and not guaranteed. If you're lucky, you'll be able to recover a subset of the files from your drives. If you go this route, only use legit services.
- Contact the party, find out how much they want, then pay the ransom. Nothing is guaranteed. If you get your data back, you may very well end up with some nasty embedded surprises. This is where you should be reading Dr. Klahn's advice very closely.
ASKER
what about to call the authorities ? right now I didn't read yet that someone wanted to do that.
That is a good thing, which might stop more files from getting encrypted. But it still won't solve for the already encrypted files. When did this problem start? And are you able to look at your internet history in your web browser?
Is this affecting a business or personal data?
ASKER
Man,the virus is still on my disk,probably. I've reinstalled the OS without formatting the disk. The old installation of windows have been placed on the folder windows.000. I'm talking about windows 7. I can't boot that installation anymore. but if the files are still there,with a good knowledge about how and where to check,I think that more informations about the virus can be gathered. I have also a lot of encrypted files on this disk. Anyway,there is also a chance that it does not appear anymore because I'm not using a common home user PC. I'm using a very old mac mini. If the virus wants to save its ass in the boot files for example,it can't because the mac mini has a different boot procedure. No,this is not the business PC. it's my personal PC. I use this not very powerful machine because the main PC is broken.
ASKER
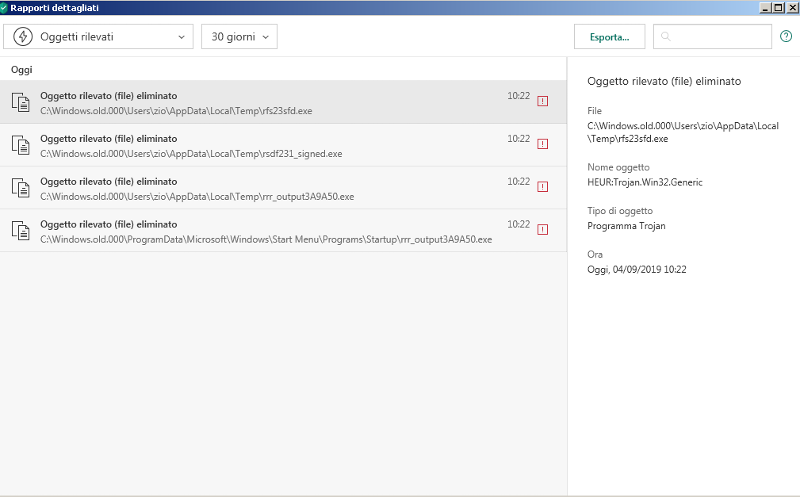
what about the picture that I have posted earlier ? Do u think that karsperky catch it ?
These viruses/malware are continually evolving and so one application might catch it, but miss others, and vice versa. Some of this can come down to luck of the draw. The important thing today is to have both an antivirus and malware protection, but even that is by far no guarantee.
You also should never be using free software online, unless you truly know the source.
You need multiple backups and they should never be continually connected to the device. So you want them unplugged, or off-site, when not being used for active backups.
You should only use a User Account for your main profile, and have a separate Administrator account that you use only as required (with different passwords). This minimizes what your account can do and can thus limit what malware/virus can do as well since they will lack elevated privileged.
You also should never be using free software online, unless you truly know the source.
You need multiple backups and they should never be continually connected to the device. So you want them unplugged, or off-site, when not being used for active backups.
You should only use a User Account for your main profile, and have a separate Administrator account that you use only as required (with different passwords). This minimizes what your account can do and can thus limit what malware/virus can do as well since they will lack elevated privileged.
ASKER
Linux
Dont rememberor don't want to say?
You also should never be using free software online, unless you truly know the source.That's always been true even of paid software. There are a lot of scammers out there.
You can't catch these with AV software. AV only comes into play for detecting an existing virus or malware. It's there to inoculate you against current infections. It has always been reactionary. You can't inoculate against something that hasn't been identified yet.
You should have had proper backups. Lesson learned. Don't keep reinstalling. If you want a chance of recovering the data, you need a brand new disk that you must wipe completely and start over with a fresh install. Save the old disk until a time when someone reverse engineers the decryptor.
Save the old disk until a time when someone reverse engineers the decryptor.Good advice.
ASKER
Can It be removed with a deeph format made with a lot of 0 AnD 1 ?
better use dban : http://www.dban.org/
ASKER
Are u sure that It works ? Because i read that It comes out again and again whatever thing u do
Yes that works. The reason it returns is that it's often a downloaded executable or email attachment that the user relaunches once the system is cleaned from reinstalled data.
ASKER
1) i tried to register an account on jabber,because I want to try to chat wth the hackers. I tried several servers,but none worked. can someone give me a working server for jabber ?
2) I'm not experienced in cryptography,but what happens if when the ramsonware comes out,it finds the informations encrypted with a tool like veracrypt ? it does encrypt them again ? Are the "on the fly" encrypting tools a valid defence ? I read also that there are tools which hides the files. when you save the file on the disk is encrypted,when u run it,it is decrypted. sounds good. or not ?
3) they are able to encrypt also the files saved in cloud like google drive ?
2) I'm not experienced in cryptography,but what happens if when the ramsonware comes out,it finds the informations encrypted with a tool like veracrypt ? it does encrypt them again ? Are the "on the fly" encrypting tools a valid defence ? I read also that there are tools which hides the files. when you save the file on the disk is encrypted,when u run it,it is decrypted. sounds good. or not ?
3) they are able to encrypt also the files saved in cloud like google drive ?
1) i tried to register an account on jabber,because I want to try to chat wth the hackers. I tried several servers,but none worked. can someone give me a working server for jabber ?
That just means their jabber servers have likely been taken down and/or got moved. Only the original hackers will be able to provide you the server. Jabber servers are run by individuals.
Encryption does not work the way you think. It just works on data. Encrypting an encrypted disk means you have to decrypt the data before you can use your own decryption key.
If you weer connected to a cloud service such as google drive while the ransomeware encryptor is running, it can encrypt the data on google drive while you have access to it.
I agree with serialband, the encryption routine doesn't care about the files themselves, it just encrypts everything regardless of file types. So even in the case of a TrueCrypt encrypted file, it would just encrypt it to lock it.
Most newer ransomware attack all connected drives, anything readily accessible by the host, this is why off-site, disconnected backup are now critical.
Sadly, as originally stated, I think you are stuck getting a new drive and starting fresh.
Good luck, I know how frustrating and time consuming all of this can be!
Most newer ransomware attack all connected drives, anything readily accessible by the host, this is why off-site, disconnected backup are now critical.
Sadly, as originally stated, I think you are stuck getting a new drive and starting fresh.
Good luck, I know how frustrating and time consuming all of this can be!
Think of encryption as a locked box with a key. You lock your documents in a locked box. It's now "encrypted" and not accessible without the key.
The malware comes by with another box and puts your box inside their box and locks it with their key. Now, you'll have to get their key to get into their box to access your the documents in your own box. Without their key, you can't use your own key to get at your own documents.
The malware comes by with another box and puts your box inside their box and locks it with their key. Now, you'll have to get their key to get into their box to access your the documents in your own box. Without their key, you can't use your own key to get at your own documents.
ASKER
A brute attack to find the key Can be done ? How much computational power needs to do that
ASKER
As i said the old windows installation is still on the sane disk. Is there a method to know which files have been used to encrypt everything ? If i dont pay in a given time the encrypted files will be deleted ? Can work a tool like recuva to recover the files befiore to be encrypted ?
“A brute attack to find the key Can be done ? How much computational power needs to do that”
It uses AES256 so in order to find the key with brute force you’d need to try at least (2^256)/2 combinations, that’s multiple lifetimes.
Brute force for AES256 is considered impractical.
I think you’re at the bargaining stage of the five stages of grief right now ...
It uses AES256 so in order to find the key with brute force you’d need to try at least (2^256)/2 combinations, that’s multiple lifetimes.
Brute force for AES256 is considered impractical.
I think you’re at the bargaining stage of the five stages of grief right now ...
ASKER
Can work a tool like recuva to recover the files befiore to be encrypted ?
No. Deleting a file is different than encrypting a file.
ASKER
Maybe I've got an idea to minimize the problems caused by this kind of viruses. I'm thinking about a script that detaches the disk when,for some reason,on the disk appears a lot of files that haven't a known extension. In my case at a certain point,a lot of ADAM files appeared on the disk. ADAM is not a common extension,so the script should detect that on the disk there are more than a given number of unknown files and it should detach all the (external) disks where and when this happens. I'm thinking about a monitoring tool and we should use the operator "if in the disk there are a certain number of files NOT called as those present inside a list.
You can't detach a disk that has files in use. You have to force a detach, causing "possible data loss" and the computer would generate and error or prompt.
You can as a human, physically pull the USB cable. It's far simpler to make a backup copy and keep the data secured that way.
You can as a human, physically pull the USB cable. It's far simpler to make a backup copy and keep the data secured that way.
ASKER
I disagree. Usually you havent big loss of data when you force a disk to be detached. Plus,even if you have some loss,its acceptable against more work to do with the restoring. And your idea to detach the disk manually is not good because usually you have no time to realize whats happening. Or you are not in front of the pc.
There are a great deal of people/companies all trying to stop this type of thing from happening, but none have managed as of yet. And even if you did come up with a way to stop this current version, they'd mutate it into something else to get around your protection. It's a never ending game of cat and mouse!
You're not going to manage to decrypt your files without the decryption key, which you'd have to pay for, and hope they give you.
Furthermore, they probably use some custom deletion process that will make the files unrecoverable, but this is just a guess on my part. Even if you could recover your files after the deadline and they deleted them, you'd still be facing the same issue of them all being encrypted and no way to decrypt them.
Sadly, you're going to have to accept your fate and start over.
You're not going to manage to decrypt your files without the decryption key, which you'd have to pay for, and hope they give you.
Furthermore, they probably use some custom deletion process that will make the files unrecoverable, but this is just a guess on my part. Even if you could recover your files after the deadline and they deleted them, you'd still be facing the same issue of them all being encrypted and no way to decrypt them.
Sadly, you're going to have to accept your fate and start over.
if you do detach the disk while is is actively writing you will get corrupted data. I'm guessing you are willing to lose some files but not all files. The problem being that an important file may be lost (either encrypted or corrupted (same end result as far as you are concerned)
The experts don't want your disk to be so corrupted that it shows up as RAW and you have to use disk recovery software to recover what can be recovered. Again you are looking at lost data.
Hardware/Software is the lowest cost of the chain, the data is the most important item.. hardware/software can be replaced, some data cannot. If there was a magic bullet to prevent ransomware do you think the municipalities/schools/hos
After the time period only the decryption key is deleted. The files will not be deleted. They might as well be deleted since they are only occupying disk space and not useable.
All of my important data is saved to an offline external disk AND uploaded to 2 different cloud providers.(I use syncback pro) I also run a honeypot that if any data file is changed the system is shut down. I have a logon message set to inform me that ransomware is detected. I have deceased family and friends that I hold the only copy of their pictures. My daughter in a separate location gets a hard drive every so often that has my offsite backups.
The experts don't want your disk to be so corrupted that it shows up as RAW and you have to use disk recovery software to recover what can be recovered. Again you are looking at lost data.
Hardware/Software is the lowest cost of the chain, the data is the most important item.. hardware/software can be replaced, some data cannot. If there was a magic bullet to prevent ransomware do you think the municipalities/schools/hos
After the time period only the decryption key is deleted. The files will not be deleted. They might as well be deleted since they are only occupying disk space and not useable.
All of my important data is saved to an offline external disk AND uploaded to 2 different cloud providers.(I use syncback pro) I also run a honeypot that if any data file is changed the system is shut down. I have a logon message set to inform me that ransomware is detected. I have deceased family and friends that I hold the only copy of their pictures. My daughter in a separate location gets a hard drive every so often that has my offsite backups.
Generally, the operating system won't let you detach the disk through software means without prompting you when files are being accessed. So while the ransomeware is encrypting your disk, you won't be able to software eject the external disk. You'd have to override the system and that's going to require privilege elevation. You'd have to physically pull the connection to forcibly disconnect it quicker. This should only corrupt the files that it was "currently" encrypting. Written properly, the ransomeware can simultaneously encrypt as many files as there are CPU threads on your system. More than that, and the extra files would be waiting for the next thread to be released. The number of threads would be the total number of corrupt files you might encounter, however, they may only do one file at a time.
The "magic" is to use offline backup copies. Implemented properly, worst case is you lose up to a week of data to less than a day of data. Unfortunately, this requires manual intervention either weekly or daily, usually done by a systems administrator. Contrary to popular belief, well run computer systems do not run completely on their own.
I've been doing offline backups for more than 2 decades, before ransomeware became popular. Larger corporations used tapes. They'd also have already taken one set of tapes to off-site storage. This is not new technology. Companies have been doing this for decades. It's only home and small business users that are new to this concept. I've used external disks drives for backups even all the way back in the 90s, onto a 2 GB external unit at smaller places and used floppy/zip/jazz/magneto-op
Offline backups are the only real solution to this problem. There is no panacea. Start doing proper backups from now on. You can't magically automate offline backups. You need a gap to the automation to be sure it's offline. Right now, and for the near future, only a human can do this.
The "magic" is to use offline backup copies. Implemented properly, worst case is you lose up to a week of data to less than a day of data. Unfortunately, this requires manual intervention either weekly or daily, usually done by a systems administrator. Contrary to popular belief, well run computer systems do not run completely on their own.
I've been doing offline backups for more than 2 decades, before ransomeware became popular. Larger corporations used tapes. They'd also have already taken one set of tapes to off-site storage. This is not new technology. Companies have been doing this for decades. It's only home and small business users that are new to this concept. I've used external disks drives for backups even all the way back in the 90s, onto a 2 GB external unit at smaller places and used floppy/zip/jazz/magneto-op
Offline backups are the only real solution to this problem. There is no panacea. Start doing proper backups from now on. You can't magically automate offline backups. You need a gap to the automation to be sure it's offline. Right now, and for the near future, only a human can do this.
ASKER
what about to hide informations with a tool like this ?
https://www.cypherix.com/hide-data/
they say : Hide your secret data, files, folders completely. Unless you unhide it yourself, nobody can find it.
what it means hide here ? it means that the data will be encrypted or hidden ? if hidden,the ransomware can't encrypt them ? is this right ?
https://www.cypherix.com/hide-data/
they say : Hide your secret data, files, folders completely. Unless you unhide it yourself, nobody can find it.
what it means hide here ? it means that the data will be encrypted or hidden ? if hidden,the ransomware can't encrypt them ? is this right ?
Usually you havent big loss of data when you force a disk to be detached.This isn't always true. Depending on the drive format, you can actually loose all your data if you don't eject it properly. It may not have happened to you, but it does happen. There are procedure to eject/detached drives and they exist for a reason.
Hiding files/folders... these are all great ideas, but the ransomware routines don't care about most of that stuff. They normally work at a low level and can see everything on the drive regardless of the special techniques you've used to obfuscate them. They don't care what it is, or what format they are in. They just grab anything they can an encrypt it.
This discussion is just turning in circles at this point. Several people have pretty much all told you the same thing: pay and retrieve your data, don't pay and start anew. Moving forward, a proper backup disconnected plan is critical. That will avoid this from happening again to you in the future.
Good luck.
ASKER
No,not yet in circle. The idea of hiding data was new.
Hiding data doesn't work though. Setting the attributes to HIDDEN/SYSTEM only hide it from explorer IF hide protected files is checked. the idea of having a secret folder within an encrypted folder (to hide from customs/police/extortionis
ASKER
what do u mean with "except if the container is encrypted by ransomware" ?
The "container" is the encrypted disk. If the ransomeware encrypts the disk with its own encryption, then you'd have to undo that first before you can decrypt your disk for access. I gave you the locked box within another locked box metaphor as a way to describe that process. It's several comments back.
ASKER
It seems that for some phobos released at the beginning of 2019 the data recovery tool "Stellar" worked.
ASKER
this is what I want to do. Since the disk that I'm using now could be again infected by the ransomware phobos adam and i don't want to format it because i want to try to recover some data with stellar,I've thought to :
1) find a version of windows 10 which run from the DVD and is it loaded inside the RAM memory,like the linux live versions
2) installing the recovery tool "Stellar" and try to recover the deleted files on the drive C by the ransomware.
so,now I need to find the windows 10 live dvd. someone knows one ? thanks.
1) find a version of windows 10 which run from the DVD and is it loaded inside the RAM memory,like the linux live versions
2) installing the recovery tool "Stellar" and try to recover the deleted files on the drive C by the ransomware.
so,now I need to find the windows 10 live dvd. someone knows one ? thanks.
Microsoft did not design Windows 10 as a live DVD. There is a project that is attempting that, however, I don't recommend it, as Windows needs a lot more than 4.7 GB to run properly. 4.7 GB is a stripped down Windows. It would be easier to boot from a linux live DVD/CD and use that to examine files, but you are likely not Linux savvy enough to do so.
If you really want to recover data, you should buy new disks drives. Buy 1 to install windows on as the boot disk. <- Easier than working on a "Windows Live DVD" Buy 1 to copy/clone your ransomware encrypted data disk. Once you've cloned it, save the original disk in case you mess up. You have to spend some money to keep data safe. You should have done it with backups, but you didn't. Now, you have to do it with proper recovery methods and that costs more in time, money, and resources than a backup. You just need to mess up one time and that data becomes permanently lost. If you really want to try a recovery, stop messing with the disk until you're ready to work on the data.
At this point, you really should hire someone, or find a friend that more IT savvy than you if you wish to recover the data. If you're already resigned to the fact that you lost the data, and you're just playing around, then ok, I guess you keep trying.
You can choose to ignore the recommendation and keep messing with the original disk, but that's your choice.
If you really want to recover data, you should buy new disks drives. Buy 1 to install windows on as the boot disk. <- Easier than working on a "Windows Live DVD" Buy 1 to copy/clone your ransomware encrypted data disk. Once you've cloned it, save the original disk in case you mess up. You have to spend some money to keep data safe. You should have done it with backups, but you didn't. Now, you have to do it with proper recovery methods and that costs more in time, money, and resources than a backup. You just need to mess up one time and that data becomes permanently lost. If you really want to try a recovery, stop messing with the disk until you're ready to work on the data.
At this point, you really should hire someone, or find a friend that more IT savvy than you if you wish to recover the data. If you're already resigned to the fact that you lost the data, and you're just playing around, then ok, I guess you keep trying.
You can choose to ignore the recommendation and keep messing with the original disk, but that's your choice.
It seems that for some phobos released at the beginning of 2019 the data recovery tool "Stellar" worked.Stellar does not solve a ransomware issue. It is a data recovery tool. A lot of ransomware will read a file, encrypt with the result being saved to a new file, then delete the original. If you're lucky, that section of the disk hasn't been written over yet, which would help your chances of data recovery. But as I mentioned before (and others have as well), it would be best that you get a professional involved if you want to go down the data recovery route.
1) find a version of windows 10 which run from the DVD and is it loaded inside the RAM memory,like the linux live versionsserialband answered this very accurately. However, there are tools that may help you which utilize a live CD (Active@ Data Studio is one such product, which includes a file recovery application). But as noted, you *should* make a clone of your drive and work with that because you would never want to chance destroying the original. See the last sentence from the previous paragraph.
you are a person who tends to blame very much himself and also the others people. You almost enjoy thinking about punishments for those who did wrong: you seem to be a sado masochistic person.Even if you consider serialband's comment harsh, what he is saying is true. We've provided the best advice to you based on the information you've provided. You're insisting on a way to recover the data, which is likely to be expensive, plus not necessarily be guaranteed (remember you mentioned at the beginning that you didn't have the money to spend). To be fair, we don't know what exactly is in the information that you've lost access to. However, at some point, you have to determine what you're willing to do and spend to try to get it back.
ASKER
I think that I've found an easy way to protect the data from the attack of the ransomware,but I need some help from a coder able with the batch scripting. And I can't explain here how to do,because this post can be read also by the persons that creates the ransomwares. So,if someone has good batch scripting skills contact me.
I'd wager that your simple way is not going to work.
ASKER
I see that we start bad,man. You suspect that it will not work without to know what I've thought.
The purpose of the Experts Exchange is to help people to resolve their problems but if they do not want to follow the advice we give, maybe we are wasting each other's time.
i think that thousands of people thought about such ways, so i doubdt you'll find a good solution, ..BUT it's Always possible
the only secure way to protect data, is to have the data on a device that is not connected to anything, afaik
the only secure way to protect data, is to have the data on a device that is not connected to anything, afaik
ASKER
Excuse me again,if I reopen this post,but I read somewhere,that's possible to create an intricate maze of folders to hide files, making the life very hard to the ransomwares from reaching the files. This idea excites me a lot and I would like some suggestions on how to implement it. I would also like to know if ransomwares are capable of encrypting the first of all folders,let's say the root folder,which contains all the other ones. I've also read that the maze can be created to trap, making the ransomwares turn around in circles forever,without ever being able to reach the files,or giving to you the time to kill or to investigate how it works. is this possible ? is not an exciting idea ?
I've also read that the maze can be created to trap, making the ransomwares turn around in circles forever,without ever being able to reach the files,or giving to you the time to kill or to investigate how it works. is this possible ? is not an exciting idea ?
not if the ransomware is multi-threaded.. you may trap one thread but the other threads that are not trapped will carry on as per usual. You could also make any file operations unstable if not break them.
not if the ransomware is multi-threaded.. you may trap one thread but the other threads that are not trapped will carry on as per usual. You could also make any file operations unstable if not break them.