Sys_Admin1
asked on
On Server 2012r2 how to log logon/off events on the local member server
I am the sys admin in a large organization that practices 'separation of duties'. At my division I have admin rights to do everything, EXCEPT logon to the domain controllers. I am trying to track logon events on local member servers, but I can't seem to get the audit logon events listed in event viewer. I have server GPOs to enable success/failure of 'audit logon events'.
I thought 'audit logon events' are shown on the local server and 'audit account logon events' are shown on the domain controller?
How do I audit local logon events on the member servers?
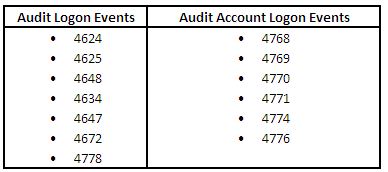
I thought 'audit logon events' are shown on the local server and 'audit account logon events' are shown on the domain controller?
How do I audit local logon events on the member servers?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
If you want post the error you get.
After creating a new AD policy you should be able to edit it....
After creating a new AD policy you should be able to edit it....
ASKER
Thanks, the DA updated the advanced audit configuration and it works. Appreciate the help!
ASKER
Sorry to reopen this, but I have another question. We've enabled all the appropriate events (we think) but are not getting failed log on attempts 4625. I've tried logging in with an account without permission and with an admin account using a bad password, neither get logged.
Sure the GPO gets applies to the system? Run
gpresult /h result.html ASKER
According to this:
https://docs.microsoft.com
you should get
Events List:
4624(S): An account was successfully logged on.
4625(F): An account failed to log on.
4648(S): A logon was attempted using explicit credentials.
4675(S): SIDs were filtered.
https://docs.microsoft.com
creates
Events List:
4634(S): An account was logged off.
4647(S): User initiated logoff.
https://docs.microsoft.com
you should get
Events List:
4624(S): An account was successfully logged on.
4625(F): An account failed to log on.
4648(S): A logon was attempted using explicit credentials.
4675(S): SIDs were filtered.
https://docs.microsoft.com
creates
Events List:
4634(S): An account was logged off.
4647(S): User initiated logoff.
ASKER
Thanks for that. I am getting 24, 34, 47,48, but no 25 (and no 75). Very strange.
Did you check for event 4625 with a domain user or a local user?
ASKER
Domain user. Everyone logs in using domain creds. If domain users won't be audited for failed attempts using these settings, is there a way to do it?
Just tested with Windows 10 as a domain user.
If I log on with a wrong password, Event 4625 gets logged.
Same for logging on as an unknown user...
Did you remove the standard auditing GPO settings under Local Policies -> Audit Policy?
Otherwise I'm stuck here... you may consider opening a new question ...
If I log on with a wrong password, Event 4625 gets logged.
Same for logging on as an unknown user...
Did you remove the standard auditing GPO settings under Local Policies -> Audit Policy?
Otherwise I'm stuck here... you may consider opening a new question ...
ASKER
I did remove auditing from the local polilcies/ audit policy. There may be something hanging around in another GPO that is stepping on it through, and I will have another look at gpresult. I have been tied up with other issues, but I will circle back to this when time permits.
Thanks for all the help, I appreciate it.
Thanks for all the help, I appreciate it.
No problem, thanks for the update!
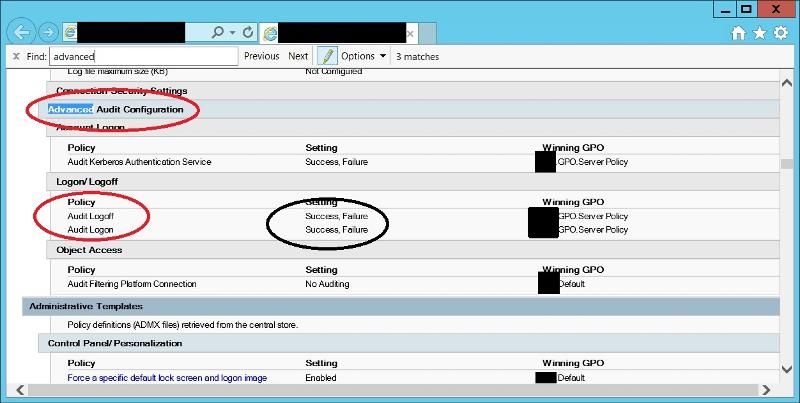
ASKER
I'm talking with the domain admin now to try to figure it out. Appreciate the help. I will post back when/if I get it sorted.