Self-signed certificate vs ca signed certificate,
Self-signed certificate vs ca signed certificate,
I have done some reading online about this topic but I get this : "The primary operational difference between a self-signed certificate and a CA certificate is that with self-signed, a browser will generally give some type of error, warning that the certificate is not issued by a CA"
I believe self signed certificate is free and the CA certificate is not.
if so, then why would not everyone use the self signed?
any explanation on this topic will be very much appreciated.
thank you
I have done some reading online about this topic but I get this : "The primary operational difference between a self-signed certificate and a CA certificate is that with self-signed, a browser will generally give some type of error, warning that the certificate is not issued by a CA"
I believe self signed certificate is free and the CA certificate is not.
if so, then why would not everyone use the self signed?
any explanation on this topic will be very much appreciated.
thank you
To make it clearer.
replace certificate with identification.
You can laminate your own ID (self signed certificate)
Your company can create a laminated employee ID (Personal CA issued/signed certificate)
You use a government issued ID (Publicly known, trusted CA signed certificate)
replace certificate with identification.
You can laminate your own ID (self signed certificate)
Your company can create a laminated employee ID (Personal CA issued/signed certificate)
You use a government issued ID (Publicly known, trusted CA signed certificate)
What most users are not aware of is that self-signed certificates can end up costing them more in the long run.
While self-signed certificates also encrypt customers' log in and other personal account credentials, they prompt most web servers to display a security alert because the certificate was not verified by a trusted CA. Often the alerts advise the visitor to abort browsing the page for security reasons. This is as mentioned already. (1) Reputation does not bode positively to getting a good business prospects.
While concerns over trustworthiness may ring true for self-signed certificates used on a publicly accessible service, it may not be the case as there is the operational consideration to run own CA and the necessary infrastructure esp for small businesses for the case of internal usage. So they may still consider self-signed certificates as a valid alternative for securing internal communications. (2) This is risk acceptance.
Of course, if properly secured, self-signed certificates can still has a lower risk for internal communications since channel are still encrypted.
However, (3) if you do not have the ability to continuously monitor and protect self-signed certificates, cyber-criminals or internal threats can conduct man-in-the-middle (MitM) attacks to impersonate the websites or systems or devices, which you have no good way to verify since it is a self issued certificate.
For example, one variant of the Dyre banking Trojan uses a self-signed certificate to communicate with its command-and-control (C&C) server over ports 443 and 4443. This certificate makes the Dyre variant's exfiltration traffic look like regular browser traffic, thereby rendering the malware more difficult to detect and analyze.
Another point that why others prefer for CA signed certificate is that (4) CAs can revoke a certificate when they discover it has been compromised, but organizations cannot revoke a self-signed certificate. Instead they must replace or rotate the certificate. This inability to rapidly revoke a compromised private key associated with a self-signed certificate may open the door to malicious attackers.
All said, there is (5) good reason still for self signed like developer need to test out the signed codes, legacy network device can only get self signed certificate, etc.
What I can say is that (6) production system should avoid using self signed and minimally have a CA signed. There is 3rd party CA like Global sign, Digicert, Verisign. There is also free CA signed version like Let's Encrypt but it had a short renewal period (every 90 days) which some may find it acceptable still. Note it also does not offer direct support to the subscribers.
While self-signed certificates also encrypt customers' log in and other personal account credentials, they prompt most web servers to display a security alert because the certificate was not verified by a trusted CA. Often the alerts advise the visitor to abort browsing the page for security reasons. This is as mentioned already. (1) Reputation does not bode positively to getting a good business prospects.
While concerns over trustworthiness may ring true for self-signed certificates used on a publicly accessible service, it may not be the case as there is the operational consideration to run own CA and the necessary infrastructure esp for small businesses for the case of internal usage. So they may still consider self-signed certificates as a valid alternative for securing internal communications. (2) This is risk acceptance.
Of course, if properly secured, self-signed certificates can still has a lower risk for internal communications since channel are still encrypted.
However, (3) if you do not have the ability to continuously monitor and protect self-signed certificates, cyber-criminals or internal threats can conduct man-in-the-middle (MitM) attacks to impersonate the websites or systems or devices, which you have no good way to verify since it is a self issued certificate.
For example, one variant of the Dyre banking Trojan uses a self-signed certificate to communicate with its command-and-control (C&C) server over ports 443 and 4443. This certificate makes the Dyre variant's exfiltration traffic look like regular browser traffic, thereby rendering the malware more difficult to detect and analyze.
Another point that why others prefer for CA signed certificate is that (4) CAs can revoke a certificate when they discover it has been compromised, but organizations cannot revoke a self-signed certificate. Instead they must replace or rotate the certificate. This inability to rapidly revoke a compromised private key associated with a self-signed certificate may open the door to malicious attackers.
All said, there is (5) good reason still for self signed like developer need to test out the signed codes, legacy network device can only get self signed certificate, etc.
What I can say is that (6) production system should avoid using self signed and minimally have a CA signed. There is 3rd party CA like Global sign, Digicert, Verisign. There is also free CA signed version like Let's Encrypt but it had a short renewal period (every 90 days) which some may find it acceptable still. Note it also does not offer direct support to the subscribers.
Self-signed certificates are used in the realm of internal application communications. These are usually set and forget scenarios that self-signed certificates are best used for such as Microsoft Exchange Server (server to server comms vis New-ExchangeCertificate). It removes a dependency that becomes a risk to the stability of the system. Basically for internal application chatter, self-signed is perfect even in production. In a small business, self-signed will be fine with only a few clients as there is not much overhead in trusting the cert on a small sample of devices. In Medium to enterprise environments you would not do this.
Private CA (internal PKI) is best used for internal applications/services where your corporate clients and devices are communicating. For example your Intranet, and other internal sites, internal web apps, client auth certs (think Radius, WiFi, etc.). Like a self-signed certificate, these are free. The difference is you will just need to push out certificate root chain to be trusted by all your devices, and then any certificate issued from that chain is automatically trusted by all devices. Not to be used for unmanaged clients (e.g. BYOD or customer machines).
Public CA is best used for internet facing applications used by customers and employees that need to be trusted by any device. Your homepage, etc. Use your CA of choice from free to not free.
Private CA (internal PKI) is best used for internal applications/services where your corporate clients and devices are communicating. For example your Intranet, and other internal sites, internal web apps, client auth certs (think Radius, WiFi, etc.). Like a self-signed certificate, these are free. The difference is you will just need to push out certificate root chain to be trusted by all your devices, and then any certificate issued from that chain is automatically trusted by all devices. Not to be used for unmanaged clients (e.g. BYOD or customer machines).
Public CA is best used for internet facing applications used by customers and employees that need to be trusted by any device. Your homepage, etc. Use your CA of choice from free to not free.
You can also just use https://LetsEncrypt.org free certs, which provides a standard/accepted issuance chain, resolving all Private CA challenges.
If you use a self-signed certificate in any applications lets say apache webserver. if you try to browse your web site which is configured on the default webserver throws certificate error because the CA is not available in your browser. if you want ignore this error install the self isgned CA to authority certificate of your browser.
If you use a self-signed certificate in any applications lets say apache webserver.
Not an accurate way to say it. If you use a self-signed certificate in a client facing application such as a web server. Many applications use self-contained and self-managed self-signed certificates and for good reason. Saying any application is misleading.
You can also just use https://LetsEncrypt.org free certs, which provides a standard/accepted issuance chain, resolving all Private CA challenges.
Using Lets Encrypt in itself could introduce points of instability and unnecessary complication to an application that only requires self-signed certificates or internal PKI. For example Let's Encrypt for an old ATM networks is not viable. These sorts of ATM networks are closed systems with no Internet access and in many cases SHA256 support is not an option. In this case internal PKI is your best option. There is really no 1 solution in the world of PKI that solves all problems, you pick the best in breed solution and always consult with your vendor documentation as to their recommended solution to make an informed decision so that you can avoid future technical debt.
ASKER
Thank you Guys
If I understand Self-Signed Certificate is free , but CA Certificate is not.
So internally to the company we still can use Self-Signed Certificate, even though end users will get that error message ,but they still can click on "Continue to this web site......)
the question is whether Self-Signed has an expiration date or never expires.. if it has an expiration date then how to make it Permanent , also if there is a way to get rid of that error message that would be helpful :
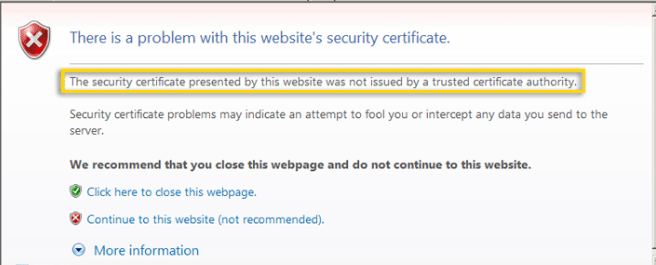
Thank you
If I understand Self-Signed Certificate is free , but CA Certificate is not.
So internally to the company we still can use Self-Signed Certificate, even though end users will get that error message ,but they still can click on "Continue to this web site......)
the question is whether Self-Signed has an expiration date or never expires.. if it has an expiration date then how to make it Permanent , also if there is a way to get rid of that error message that would be helpful :
Thank you
Open the certificate and tells you the length of tine for which it is valid. Usually it is in years, but it does expires at some point.
IMHO, if you do not want to install a Windows CA, using OpenSSL as a CA is the next thing.
Point being, if you take the time, you would avoid these notices/errors.
IMHO, if you do not want to install a Windows CA, using OpenSSL as a CA is the next thing.
Point being, if you take the time, you would avoid these notices/errors.
CA cert can be free, if you are referring to the trusted root card certificate. You can see your cert store for those list that comes with Windows. The 3rd party CA also let you download the CA and intermediate CA certificate without a cost.
Self signed certificate will expire, same as the rest of the certificate. The question should be when will it expire. Next time you produce a self-signed certificate, make it long-lived. Certificates expire mostly in order to make revocation work (certificate expiry prevents CRL from growing indefinitely). For a self-signed certificate, there is no revocation, so you can make the certificate valid for 20 years or as long...
Self signed certificate will expire, same as the rest of the certificate. The question should be when will it expire. Next time you produce a self-signed certificate, make it long-lived. Certificates expire mostly in order to make revocation work (certificate expiry prevents CRL from growing indefinitely). For a self-signed certificate, there is no revocation, so you can make the certificate valid for 20 years or as long...
ASKER
The take away :
The only time I need paid CA, is if I have a public access to an application.
if an Application is used internally only, Self Signed will be fine , or as :
btan has commented above :
The only time I need paid CA, is if I have a public access to an application.
if an Application is used internally only, Self Signed will be fine , or as :
btan has commented above :
CA cert can be free, if you are referring to the trusted root card certificate
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you Guys!!
You're welcome!
Good luck!
Good luck!
Ca certificate has two options:
You can be your own CA which will have a similar as your self-signed, but once you add your CA's public certificate as trusted, all subsequently signed certs by your CA will be trusted by systems that added ...
A public CA signed certificate are automatically trusted by all/everybody.